Tom creates a complex alarm system with too many points of access. This is the concept he forgot to abide by.
What is Keep It Simple
A computer input device in the form of a small panel containing different touch-sensitive areas.
A. Touch Pad
B. Mouse
C. Keyboard
D. Monitor
What is A. Touch Pad
This attack attempts to find out your credentials by repetitively trying all combinations of possible credentials and usually is automated using a tool
A. Dictionary Attack
B. Phishing Attack
C. Credential Stuffing
D. Brute Force Attack
What is D. Brute Force Attack
This is a ___ topology
A. Star
B. Bus
C. Mesh
D. Tree

What is B. Bus
IP Address
What is Internet Protocol Address
A Denial of Service attack can result in a crashed system and represents the undermining of this concept
What is Availability
Which of the following is an input device?
A. Speaker
B. Microphone
C. Monitor
D. Printer
What is B. microphone
This security system is used to monitor the incoming and outgoing traffic on a network and blocks traffic based on assigned security policies
A. Router
B. Switch
C. Firewall
D. Packet Sniffer
What is C. Firewall
Which is bigger - a LAN or a WAN?
What is a WAN
For extra points - what do these two things stand for?
VPN
What is Virtual Private Network
Purdue University is utilizing this concept when they secure their data with a firewall, passwords, two-factor authentication, and encryption.
What is Defense in Depth
The brain of the computer is called this
What is the CPU
For extra points - what does it stand for?
These are the advantages of using a VPN
1. VPNs encrypt traffic
2. VPNs can connect remote office locations cheaply (compared to WANs)
3. VPNs disguise the identity of the user
The HTTP service uses this port number to communicate
A. 443
B. 25
C. 40
D. 80
What is D. 80
HTTP
What is HyperText Transer Protocol
For extra points - what does HTTPS stand for?
The property that information is not disclosed to individuals, devices, or processes unless they have been authorized to access the information.
What is Confidentiality
This piece of hardware allows the Raspberry Pi to control and monitor the outside world through electronic circuits.
A. CPU
B. RAM
C. GPIO pins
D. Ethernet Port

What is C. GPIO pins

The practice and study of techniques for securing information and communication mainly to protect the data from third parties that the data is not intended for
A. Data Hiding
B. Cryptography
C. Antivirus
D. Firewalls
What is B. Cryptography
This is the globally unique, physically embedded address given to devices in a network
A. IP Address
B. MAC Address
C. Hostname
D. Port Number
What is B. MAC Address (Media Access Control)
DNS
What is Domain Name System
The property that information, an information system, or a component of a system has not been modified or destroyed in an unauthorized manner.
What is Integrity
This is indicated by the red light on the Raspberry Pi.
A. The Pi has an active power source
B. The Pi is low on battery
C. The Pi has no network connection
D. The Pi is in shutdown mode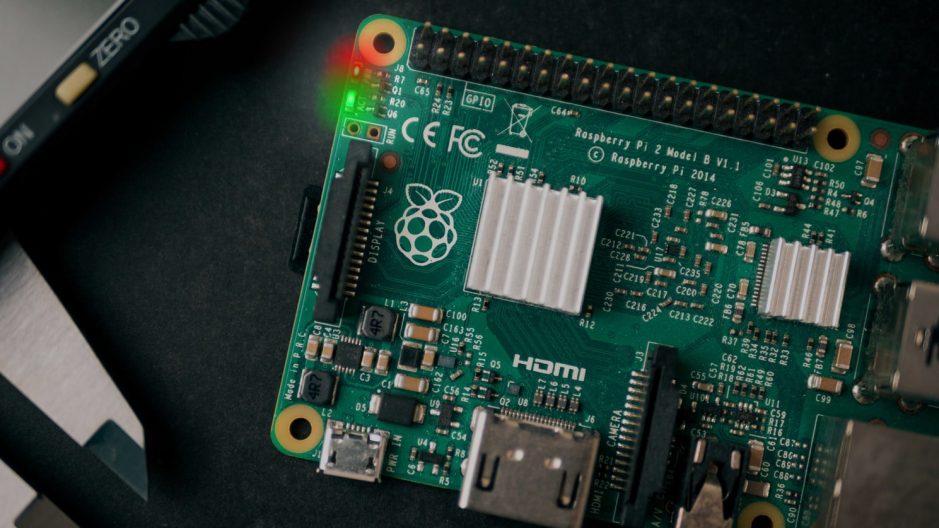
What is A. The Pi has an active power source

The CIA Triad is a model designed to guide policies in information security and is made up of these components
A. Confirmation, Information, Assurance
B. Calculations, Investigation, Awareness
C. Confidentiality, Integrity, Availability
D. Credibility, Internet, ASCII
What is Confidentiality, Integrity, Availability
This layer of the OSI Reference Model is concerned with transmitting raw bits over a communication channel such as an Ethernet cable
A. Physical
B. Data Link
C. Network
D. Transport
What is A. Physical

APT
What is Advanced Persistent Threat