A binary number that ends in a 1 will be...
Odd
No negative zero, and x + -x == 0
Hexadecimal is base ______
16
What does it mean for a network to be "scalable"?
It can expand effectively when new computers are added.
A caesar cipher is known as symmetric encryption. Public-key encryption is known as ___________ encryption.
Asymmetric! :)
Convert 8 to binary
1000
Our negative decimal to binary conversion algorithm is known as what?
Two's complement
Where is hex used in computer science?
Most commonly to represent colors, but anywhere binary is appropriate!
What trait does a fault-tolerant network have?
If one computer on it dies, the network still continues to function.
What is ASCII?
A system for converting between integers and characters, for encoding strings (and just about everything else)
Convert 1010 to decimal
10
Convert -12 to binary
12: 00...1100
flip: 11...0011
add one for final result: 11...0100
What range of letters are used in hex, and what decimal values do they represent?
A-F, 10-15
The diagram below represents a small network. Is it redundant?
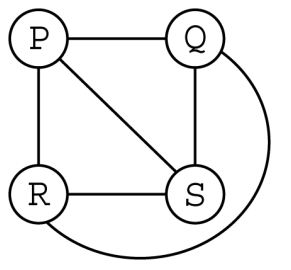
Yes; there are multiple paths between each node on the graph.
Take a look at the ASCII table. Which two integers, combined, represent the message "Hi"?
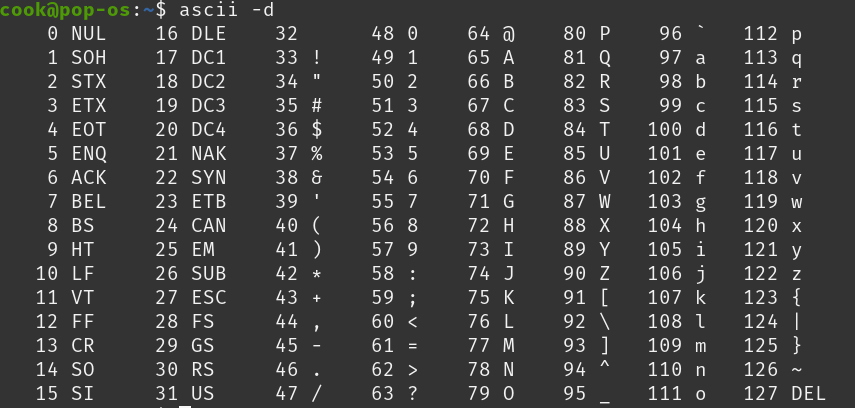
72 105
Convert 11111 to decimal
31
Convert -1 to binary
positive: 00...01
flip bits: 11...10
add one to get result: 11...11
Convert B3 to binary.
10110011
Name 2 types of malware and what they do.
Answers vary!
What's the difference between encoding and encryption?
Encoding: changing the format of data (to make it easier to send, read, process, whatever)
Encryption: encoding data for the purpose of making it hard to "crack" and read if you're not the intended recipient.
Convert 72 to binary
1001000
Convert -19 to binary.
Positive 19: 00...10011
Flip: 11...01100
Add one to get result: 11...01101
Convert 87 (hex) to binary
10000111
What's the main weakness or drawback of using antivirus software, and how can you protect yourself in light of it?
Antivirus software is reactive, not proactive. Protect yourself with VPNs, MFA, not being stupid, rotating passwords, etc etc etc
Intercepting and reading a user's packets as they send them to the router is known as what type of attack?
"Monkey in the middle"