An encryption is...
What is encoding data to prevent others from accessing it?
Data mining is...
What is is a field of study that analyzes large datasets?
Phishing is...
"Scientific research that the general population helps to conduct" is...
What is citizen science?
World Wide Web is...
What is originally created for scientist to share their research, but is now used as a system of interconnected public webpages accessible through the Internet?
What is a key?
Machine learning is...
What is a subset of data mining; machine learning uses algorithms to analyze data and predict behavior and is used in Artificial Intelligence (AI)?
Virus Vs. Worm
What is A worm can operate independently, while a virus is an infected file that must be activated by the user?
"Gaps between those who have access to the internet and those who do not" is...
What is digital divide?
Name 2 way social media has shaped history.
Answers may vary.
The difference between symmetric key encryption and public key encryption is...
What is...
Symmetric key encryption uses one key for encrypting & decrypting, while public key encryption uses a public key to encrypt & a private key to decrypt.
Name an example of a digital footprint.
Answers may vary
Name an example of an multi-factor authentication.
Answers may vary.
"The person who created something determines who uses their creation" is...
What is copyright?
Peer-to-peer networks are...
What is used to illegally share files of all types?
Decode the following Caesar Cipher (shift of 7):
Dl dpss whzz aopz HW alza!
What is we will pass this AP exam!
How is bias relevant in computer science?
What is that people write the algorithms, and our biases can make their way into the algorithms and the data used by innovations without us realizing it?
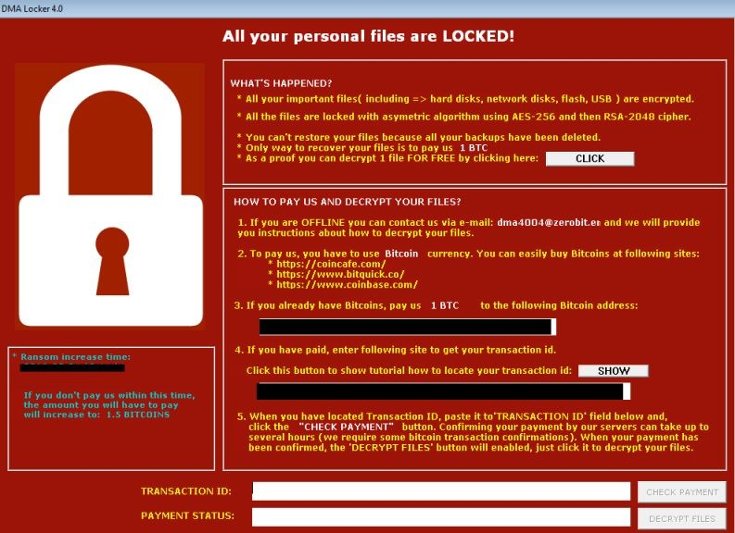
This is an example of...
What is malware/DDoS?
"Information that can be used to identify you" is...
What is Personally Identifiable Information?
What is allows people to share information and ask the “crowd”— anyone who accesses the site—for feedback, to help solve problems, find employment, or for funding?
 Decode the following message:
Decode the following message:
EYZZ SZ
What is free me?
Explain how the internet is used.
What is digital certificates can be purchased from Certificate Authorities (CAs), which identify trusted sites; they issue certificates that businesses, organizations, and individuals load to their websites?
Name 5 examples of Personally Identifiable Information (PII).
Answers vary.
"A form of malware that captures every keystroke and transmits it to whomever planted it" is known as...
What is keylogging software?
Cloud computing...
What is offers new ways for people to communicate, making collaboration easier and more efficient;
Storing documents in the “cloud” simply means they are stored on a computer server at a location different than where the owner of the files is located.