Network Address Translation is a network service that converts an internal public number to a number for a private network.
True...Sike!!! False!!!!
What is a de facto standard?
One that is generally accepted over time & adopted for use
Port 23 is used by?
telnet
What is the difference between a Smurf attack and Ping of Death attack???
How many bits are in IPv6?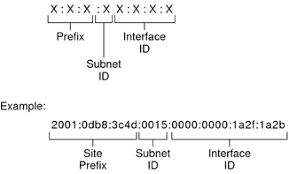
128
A global unicast address is a public IPv6.
True..
What is an octet?
The four individual sections of an IP address
Port 23 uses UDP or TCP?
TCP
What is a SYN flood?
Hackers exploiting a vulnerability in the three-way handshake by not closing the handshake.
What is TCP/IP?
a de facto standard for networking
True or False
DoS are hacks against the availability of data. DoS attacks do steal and destroy data.
False!!!!!!
What is a Classless Internet Domain Resolution (CIDR)?
A way to represent IP addresses in compressed form
What port number is UDP?
67/68
These pieces of software that are designed to be spread from one computer to another.
Virus
A connectionless protocol that has less information that needs to be sent with data.

A subnet mask can be expressed in 2 or more ways.
False
The process of comparing two binary digits & creating a value based on the comparison
ANDing
What port number is used for SSH
22
a malicious traffic overload that occurs when attackers overflood a website with traffic.
DoS Attack
Which of these is an example of IPv4?
172.16.254.1
2001:0DB8:AC10:FE01
172.16.254.1
If the source IP isn't faked, or spoofed, the IP can be blocked in the firewall.
True!!!!!!!!!
Physical addresses embedded into the hardware of network cards
Media Access Control (MAC)
443
HTTPS
Q. A network administrator needs to ensure the company’s network is protected against smurf attacks. What should the network administrator do?
A. Install flood guards.
B. Use salting techniques.
C. Verify border routers block directed broadcasts.
D. Ensure protocols use timestamps and sequence numbers.
C
IPv5 is only used in countries on the southern hemisphere.
NO.... It was just an experiment