AES stands for this.
What is Advanced Encryption Standard?
AES is one of these two: Symmetric or Asymmetric
What is Symmetric?
These are the OSI model layers, going from bottom to top.
What are the physical, datalink, network, transport, session, presentation, and application layers?
An attack that tries every possible key to break a ciphertext.
What is the brute force attack?
This tool is used to scan for open ports on a server.
What is nmap?
The organization that standardized AES.
What is NIST?
The row operation SubBytes
What is substitution?
This is the modern way to allocate network addresses.
What is CIDR?
An attack where the attacker has the least amount of information to work with.
What is the ciphertext-only attack?
This is what RBAC stands for.
What is Role-Based Access Control?
A matrix used as part of a block cipher to perform substitution.
What is an S-Box?
The Proof for why AES is secure.
What is Computational proof?
This provides an option for automatic IP address assignment without a DHCP server.
This cipher is easy to break as it leaves a lot of the structure from the plaintext language.
What is the playfaire cipher?
This tool is used to get information on and exploit SQL databases.
What is sqlmap?
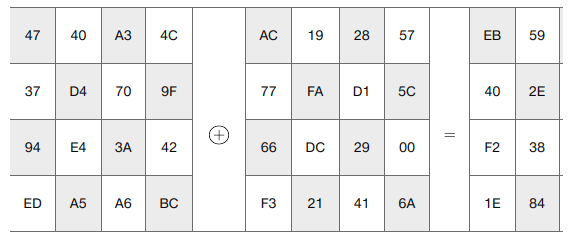
What is Forward Add Round Key Transformation?
These are the four operations for each round of AES.
What are SubBytes, ShiftRows, MixColumns, and Add round key?
These are the 4 steps of obtaining an IP address through DHCP.
What are discover, offer, request, and acknowledge?
The One-Time Pad is theoretically unbreakable, but it's not practical because of this.
What is human negligence?
This Windows tool is used to manage policies across an enterprise network.
What is the Group Policy Management Console?
The number of rounds needed for AES 128, 192, and 256 bit keys respectively.
What are 10, 12, and 14?
There are these many operations in the last round of AES.
What is three?
This is what CSMA does.
What is listening to see if other devices are transmitting?
This AT&T engineer made the ultimate defense against cryptanalysis.
Who is Gilbert Vernam?
This Windows tool is used to backup and restore files, folders, partitions, and disks.
What is AOMEI Backupper?