Introduction (IaC)
In the context of cloud computing, what does a "Region" refer to?
Geographical area comprised of multiple zones?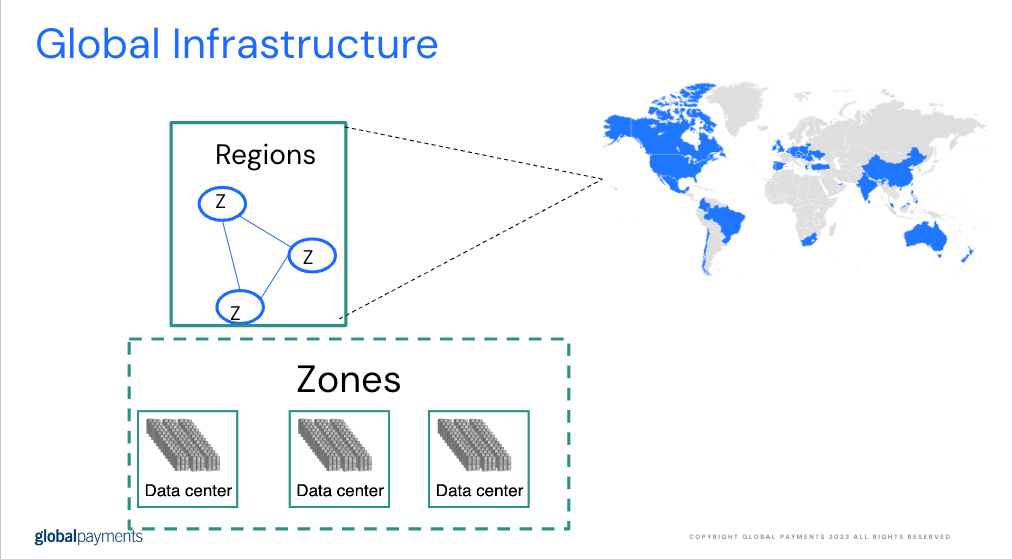 ?
?
The ability of a system to stay operational with minimal downtime.
High Availability
What is the term of automatically distributing traffic across multiple instances for high availability and fault tolerance?
Load Balancing
What are the three main storage options in the cloud?
block/disk storage, object storage, and file storage
What does "VPC" stand for in cloud computing?
Virtual Private Cloud
Which popular IaC tool uses a configuration language called HCL?
Terraform.
What does "IAM" stand for?
Identity and Access Management
What does "WAF" stand for in cloud security?
Web Application Firewall
How many Zones are typically present in a single Cloud region?
2 - 3 Zones.
This term refers to a time delay in data transmission and can affect application responsiveness.
Latency
Cloud Compute services such as Virtual Machines are examples of what type of service?
Unmanaged Services
You are needing to archive older documents to adhere to regulation requirements. You also need to ensure the contents of documents cannot be altered or changed in anyway. What storage type should you use?
Object storage
What is the purpose of a VPC in cloud computing?
Network Isolation, Security, and Controlling access
Which are the primary benefits of using IaC to manage cloud resources?
Efficiency, Consistency, Scalability? (Will also take Repeatability, Adaptability, and Automation) 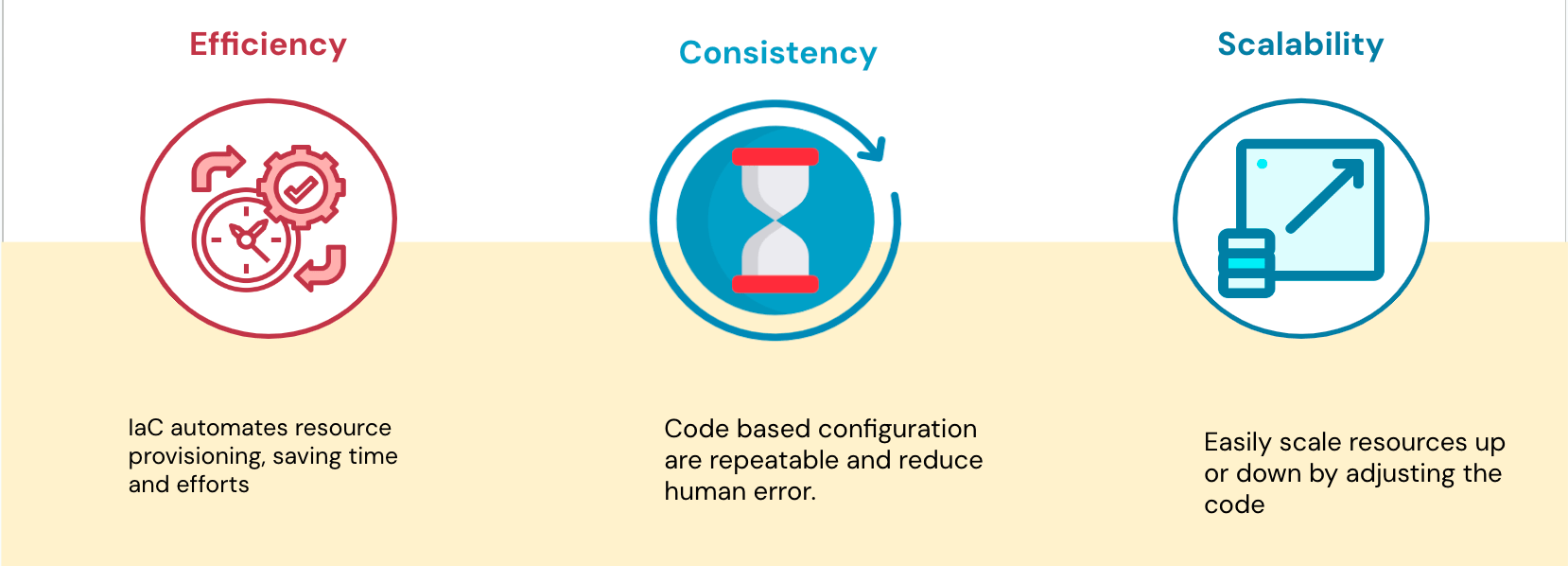
What is the fundamental principle of IAM in cloud security?
Principle of Least Privilege
A network engineer wants to protect their organization's web application from online threats. They start by establishing firewall rules at the network level. However, what is another tool that can be used to increase the security of the application?
WAF
What's the primary purpose of a data center in a cloud region?
A) Providing redundancy
B) Hosting virtual machines
C) Handling user requests
(A) Providing redundancy.
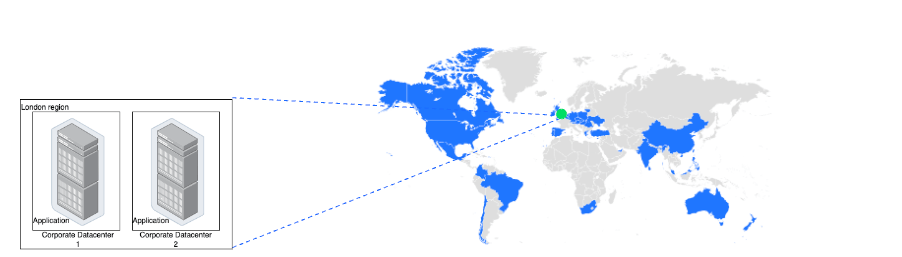
The system's ability to grow or expand its capacity to handle increased workloads.
Scalability
What type of cloud service allows you to run applications without managing the infrastructure?
Serverless Services
You're responsible for setting up a database for a high-demand application where consistent, high-speed performance is a top priority. Which disk storage option should you select to ensure a high level of Input/Output Operations Per Second (IOPS)?
Provisioned IOPS (Input/Output Operations Per Second).
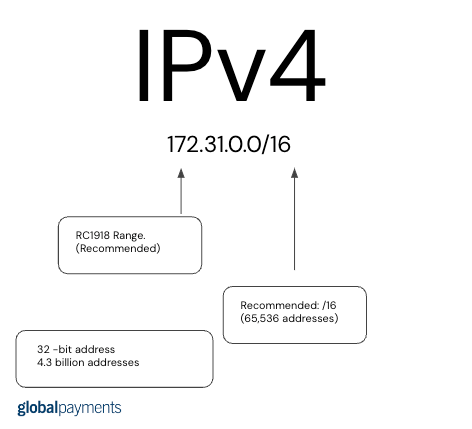
What IP Address type consist of public and private IP addresses.
IPv4
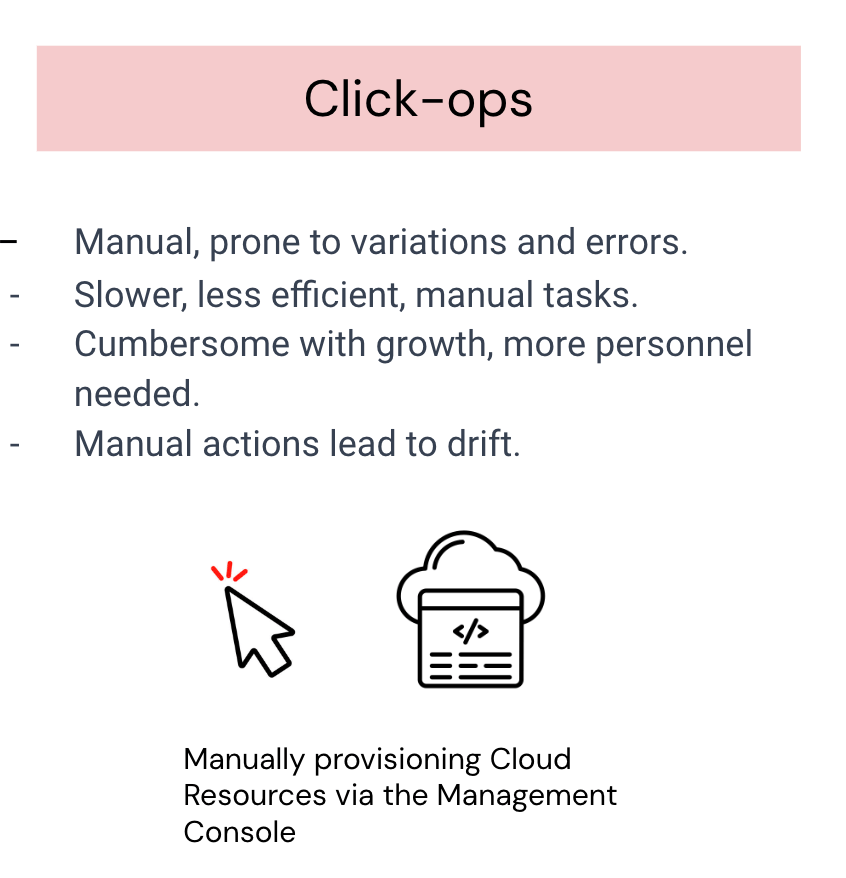
What is the term use to describe manually provisioning Cloud Resources? It is slow, ineffective, and prone to error. We normally want to avoid this process.
Click-ops
What does an IAM policy define?
Permission and access control rules
A website experiences a sudden, massive influx of traffic, overwhelming its servers and causing the site to become slow or unresponsive. This traffic is coming from a vast number of different sources and appears to be a coordinated attack. What type of attack is this most likely indicative of?
DDoS (Distributed Denial of Service) attack.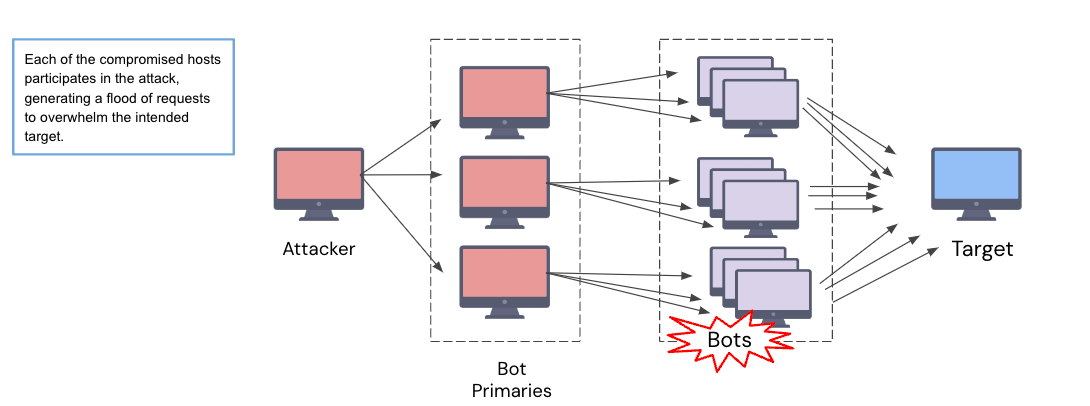
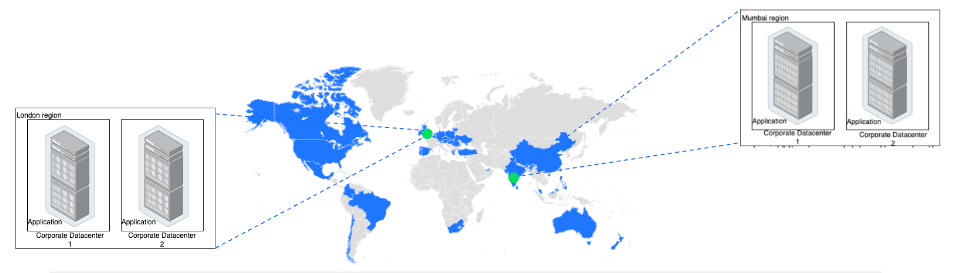
When would you consider choosing a multi-region setup over a single-region setup?
High availability is needed
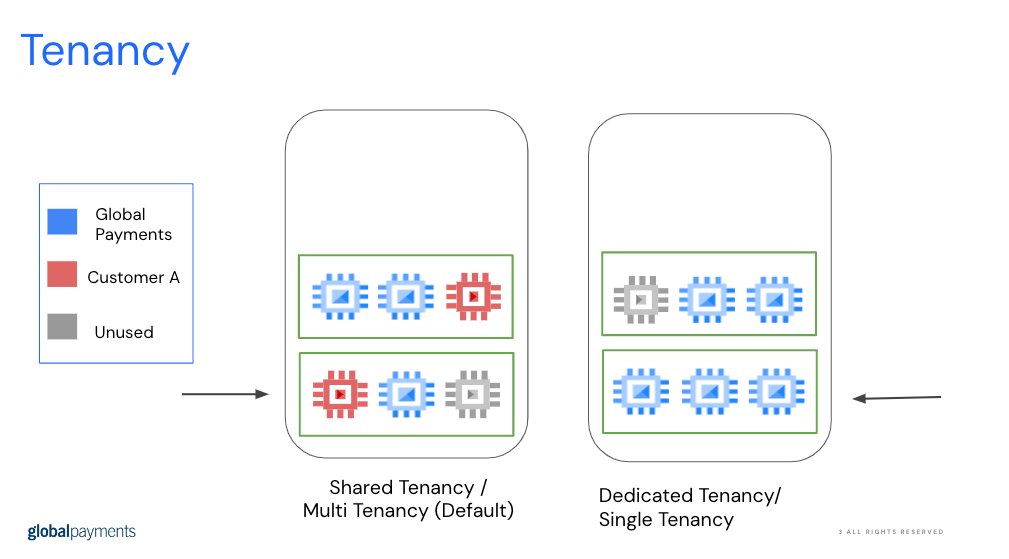
What is the Tenancy model needed for a organization that requires strict isolation and security requirements?
Single or Dedicated tenancy
What Virtual Machine Type can be used for things like web hosting, small databases, testing environments, and a versatile range of applications?
General purpose
In the cloud, what storage option is best for frequently accessed data that requires low latency?
Disk/Block Storage
This is a stateless security feature in AWS that allows you to define rules that either allow or deny traffic from and to subnets.
Network Access Control Lists (NACLs)
What is the command that will allow you to preview the changes that Terraform will make to your infrastructure?
.
`terraform plan` command
Frequently, the terms Authentication and Authorization are erroneously interchanged. Which of these terms allows an individual to execute requests within the cloud or access particular cloud resources?"
Authorization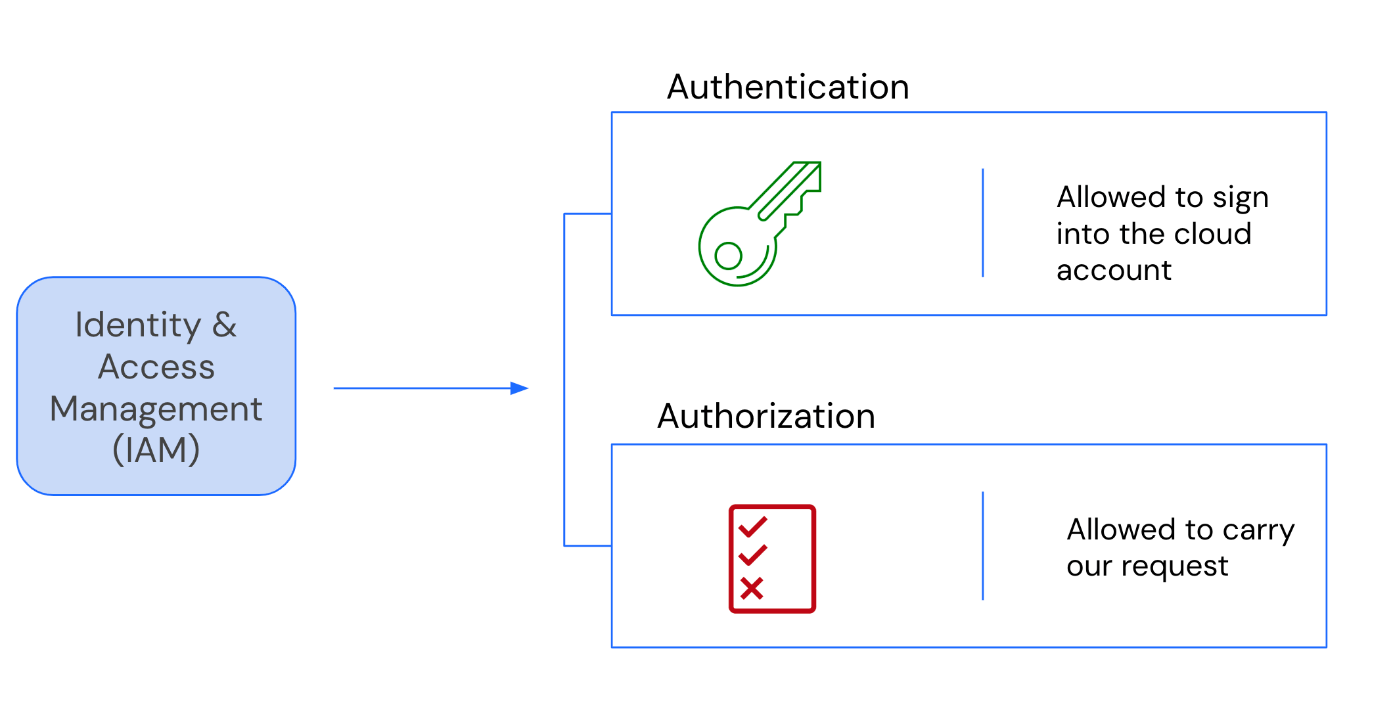
What measure can be used to mitigate DDoS attaches in cloud environments?
Traffic filtering, implementing firewall rules, using WAF (etc)
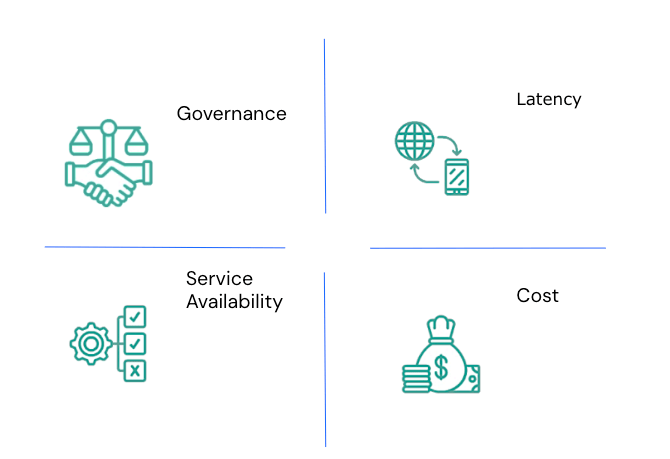
Name two factors to consider when selecting the optimal region for your cloud resources.
Governance, Latency, Service Availability, or Cost.
An E-commerce website preparing for a flash sale event. As customer traffic surges, the website automatically adds more server resources to handle the increased demand. When the sale ends, it scales down to save costs.
Elasticity
What Virtual Machine Type is use as High-performance processors? Use cases include scientific simulations, and batch processing.
Compute Optimized
You have multiple instances in different subnets that need to share the application data. What storage method would you use?
File storage
As a cloud engineer you are looking to manage both the ingress and egress traffic of your entire GCP Network. What networking feature are you most likely to use?
firewall rules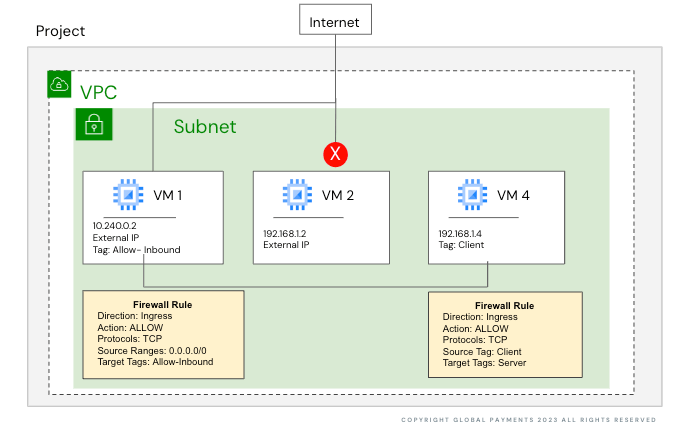
You have updated your terraform code, and previewed the changes. What should you now do to update your your cloud infrastructure?
`terraform apply` command
What in GCP is used to authenticate applications and services to access google cloud resources?
services account
In a cloud environment, a hacker attempts to overload a specific web application with a high volume of fake requests, causing it to slow down and eventually crash. What type of cyberattack does this scenario represent?
What is an Application Layer Attack, or HTTP Floods/DNS Query Attacks
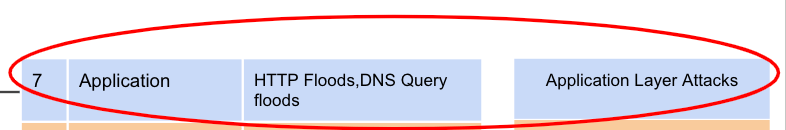
Explain why it's important to understand the global infrastructure of a cloud provider before deploying resources.
Optimize performance and costs.
An e-commerce website that has distributed servers globally. In case one of its data centers faces an unexpected power outage or hardware failure, traffic is automatically rerouted to other data centers, ensuring that customers can continue shopping without disruptions.
Fault Tolerance
In serverless computing, what do you typically need to add? By adding this, one will not have to worry about managing infrastructure.
Your code
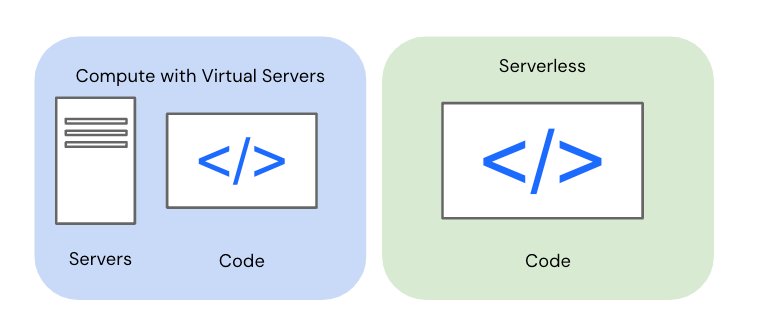
You have a application that is hosted on a VM. The application is generating data that is being stored on a disk/volume. Someone without your knowledge stops the VM, resulting in all the data being lost. Why was the data lost?
The VM was using an ephemeral storage volumes. Ephemeral storage does not persist beyond the life of the instance.
How many total IP address does your network receive if the CIDR WITH A "/16"
65,536 total IP addresses
You've been managing your infrastructure using Terraform. However, as your team grows, you want to ensure secure and collaborative state management. Which Terraform concept is best suited for this, offering a centralized location to store the state of your infrastructure?
Terraform State File
You need to ensure that different teams have varying levels of access to resources across your cloud environment, what IAM solution allows you to grant precise permissions, facilitating seamless collaboration between your teams while maintaining security and governance?
IAM Roles (AWS)
In a cloud environment, a hacker launches a massive flood of network traffic with the intention of overwhelming the network's capacity, causing it to become unresponsive. At what layer would this cyberattack occur?
Infrastructure layer or, Layer 3 & Layer 4 of the OSI model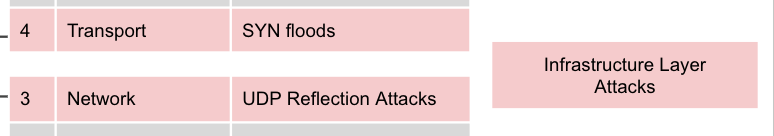
A customer is trying to access a file that is stored in a different part of the world. They are experiencing extremely slow download speeds. What technique can the architect implement to improve the customer experience?
Caching
How does "Durability" differ from "Redundancy" in cloud services?
Durability- Ability to recover from failures.
Redundancy- means having extra copies of data resources.
What are three use case for Memory optimized instances?
In-memory databases, real-time big data analytics, and memory-intensive applications that require fast data retrieval.
What kind of data is typically stored in NoSQL database?
unstructured or semi-structured data
You select IPv6 for your network IP addresses. Since IPv6 addresses are global what method could you use to control egress traffic of your network? (AWS or GCP)
Option 1:
Create security groups for your instances, and define egress rules that allow or deny traffic based on the source IPv6 addresses, destination ports, and protocols.
Option 2:
Create network ACLs for your subnets, and define rules to allow or deny egress traffic.
Option 3:
AWS provides egress-only Internet gateways to allow outbound IPv6 traffic from your instances to the internet while preventing unsolicited incoming traffic.
Option 4:
In GCP, you can create firewall rules that control egress traffic. Define firewall rules based on source and destination IP addresses, as well as protocols and ports. These rules can control egress traffic at the VM instance level.
Option 5:
GCP provides Organization Policy constraints that let you control egress at the organizational level. You can set constraints on projects to restrict their egress traffic according to your organization's policies.
You're architecting a new Terraform project for a large organization. You need to decide where to store the state file to ensure security, collaboration, and high availability. What are the best places or mechanisms to store Terraform state files that align with these requirements?
Object Storage Services/Resource
(AWS S3, GCP Buckets, Azure Blob Storage)
The following image contains an IAM policy for a network engineer.
TWO PART QUESTION:
1) Name the cloud platform where the policy originates.
2) Does the policy follow the principles of least privilege?
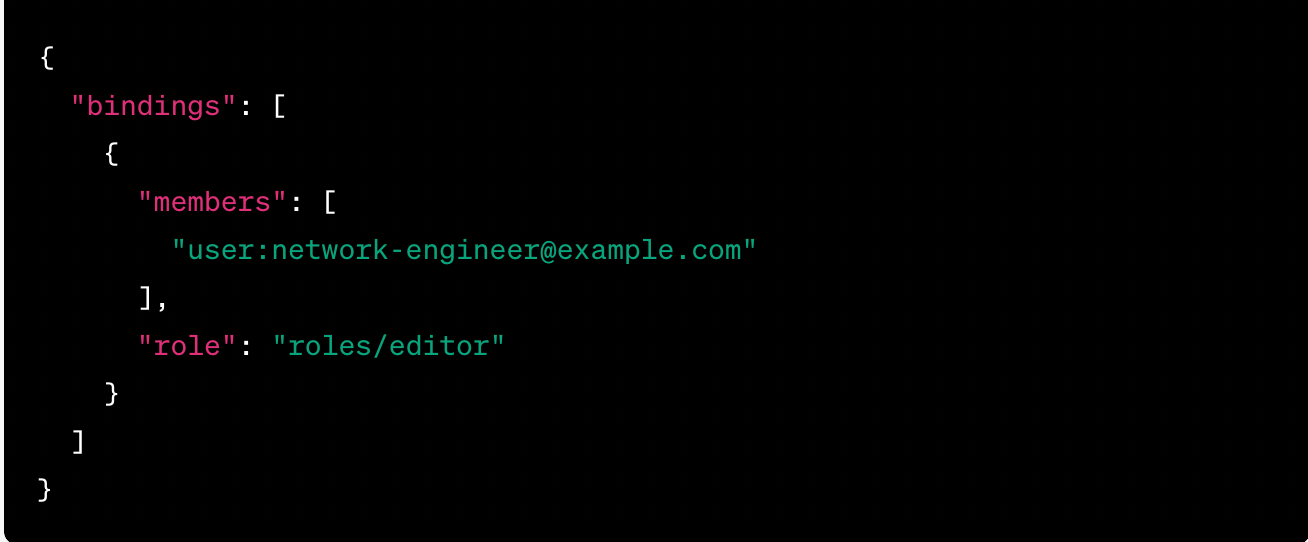
1) Google Cloud Platform (GCP)
2) Policy does not follow the principles of least privilege
A perpetrator sends a large number of UDP packets to multiple servers using a fake IP address, where these servers reply to the spoofed address, overwhelming the victim with unsolicited traffic. In which layer of the OSI model does this attack primarily occur?
Hint: Specify the exact layer.
Layer 3 or the Network layer