The claim of who you are
What is Identification
Mechanism that allows subjects to authenticate only once without repetitive challenges
What is Single Sign On (SSO)
Authentication protocol that requires a username and password
What is Password Authentication Protocol (PAP)
Essentially described as password complex
What is entropy
The concept that risk can never be zero. The remaining risk after risk management solutions have been applied.
What is residual risk
A bogus system that appears to be a production server which can be used to learn the hacking techniques and methods that hackers might employ against your network.
What is a honeypot
the three A's in the AAA triad model
What is Authentication, Authorization, and Accounting
An implied access control relationship between two entities when both trust a shared intermediary entity
What is transitive trust
A authentication protocol that features a challenge response 3-way handshake
What is Challenge Handshake Authentication Protocol (CHAP)
Minimum password lifetime
Maximum password lifetime
Password History
{these prevent what}
What prevents password reuse
An alternate location with established power, HVAC, and network connectivity to the building often with established network backbone and rack system
What is a "warm site"
smashing the equipment and media so its no longer usable
What is the data destruction technique known as "Pulverizing"
Is an example of "somewhere you are"
What is GPS (possibly others)
Nondiscretionary method for info access. Objects are assigned security labels. Subjects are assigned clearance levels.
What is Mandatory Access Control (MAC)
A Cisco proprietary authentication protocol designed to be used with WEP
What is Lightweight EAP (LEAP)
An internet/web access control ,XML-based open internet standard, that supports cloud-based identity management, centralized SSO authentication, and XML cookie-based authorization
What is Security Assertion Markup Language (SAML)
The proactive, automated checking of system state or system security posture
What is Continuous monitoring
detects potential data breaches/data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data while in use, in motion, and at rest.
What is Data Loss Prevention (DLP)
Google Authenticator providing data chunks for authentication
What is a software-based token
Creator / owner decides access. Allows users to share information dynamically with other users. More flexibility with controlling access.
What is Discretionary Access Control (DAC)
A networking protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use a network service. Replaced by Diameter.
What is Remote Authentication Dial-In User Service (RADIUS)
Basically SAML combined with OAUTH
What is OpenID Connect?
The maximum expected period of time for which data will be lost in the case of a disaster
What is Recovery point objective (RPO)
technology supports threat detection, compliance and security incident management through the collection and analysis (both near real time and historical) of security events, as well as a wide variety of other event and contextual data sources.
What is Security information and event management (SIEM)
Authentication tokens that have been synchronized to an authentication server such as Time-based One Time Password (TOTP) devices
What is a "Synchronous" token
An access control mechanism determines access by matching the current value of subject attributes, object attributes, environment conditions, and a set policy
What is Attribute-based access control (ABAC)
A IEEE Standard for port-based Network Access Control (PNAC) providing an authentication mechanism for devices wishing to attach to a LAN or WLAN
What is IEEE 802.1X
Formula that describes the number of possible password combinations
What is Number of Possible Combinations = SL
average time a repairable component operates before it will likely experience failure again
What is Mean Time Between Failures (MTBF)
is a tool (hardware or software) used to capture and analyze signals and data traffic over a communication channel. Such a channel varies from a local computer bus to a satellite link, that provides a means of communication using a standard communication protocol (networked or point-to-point)
What is a Protocol Analyzer
The point at which the FRR equals the FAR in Biometrics statistics.
What is Crossover Error Rate (CER)
A Windows authentication protocol that uses MD5 enciphering but lacks mutual authentication
What is NTLMv2
An enterprise authentication protocol diagramed below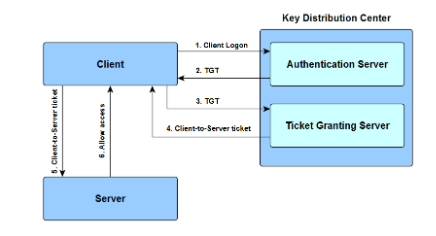
What is Kerberos
Formula that describes password entropy
What is Entropy = log2(Number of Possible Combinations)
The 6 steps to a risk assessment (in order)
What are...
1. Inventory
2. Threat Assessment
3. BIA
4. Likelihood
5. Prioritize
6. Risk Mitigation
Continuous monitoring can be challenging due to encryption. This technology makes SSL/TLS traffic decryption possible by installing X.509 digital certificates on the client node to avoid unsecure channel errors.
What is SSL (TLS) Decryptors