
The quantities, characters, or symbols on which operations are performed by a computer, being stored and transmitted in the form of electrical signals and recorded on magnetic, optical, or mechanical recording media.
What is Data?
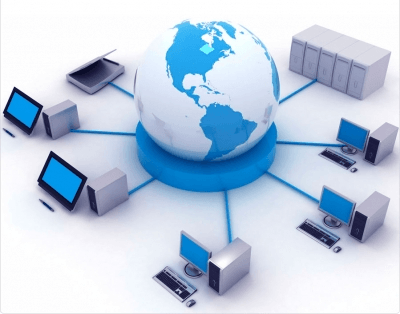
A group of interconnected (via cable and/or wireless) computers and peripherals that is capable of sharing software and hardware resources between many users.
Is bullying that takes place over digital devices. It can occur through SMS, Text, and apps, or online in social media, forums, or gaming where people can view, participate in, or share content. It also includes sending, posting, or sharing negative, harmful, false, or mean content about someone else.



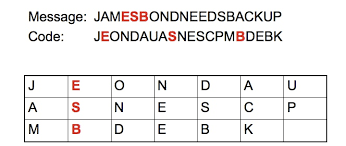
The enciphering and deciphering of messages in secret code or cipher. The computerized encoding and decoding of information. Is most often associated with scrambling plaintext (ordinary text, sometimes referred to as cleartext) into ciphertext (a process called encryption), then back again (known as decryption).
What is Cryptography or Encryption?

The use of personality, knowledge of human nature and social skills to steal passwords, keys, tokens or other credentials to gain access to systems.

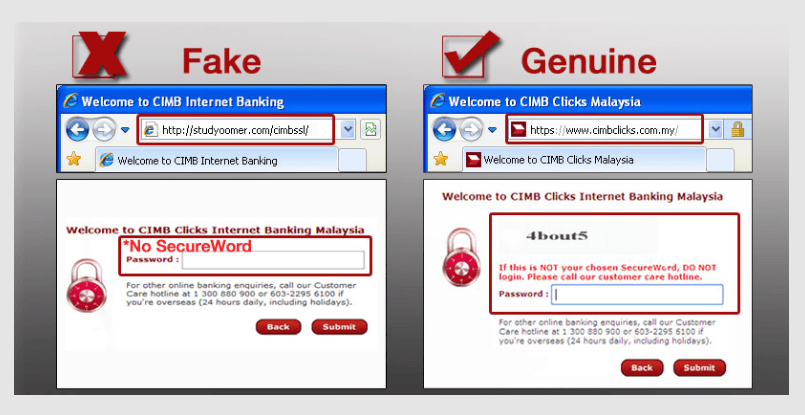
Attempting to trick people into revealing sensitive information, such as passwords and credit card numbers, often by using emails or fake websites that look like they are from trusted organizations.


Connecting with family and friends online can be fun and exciting, but it also comes with some risks. Please provide a risk to staying online?
What is / are ____?
Privacy, Permanency, Predators, Identity fraud, Trolling & Catfishing just to name a few.
Controls traffic within a network.
What is a Switch?
Are pieces of information that can be attached to a tweet, status, or photo on a social networking site that shows the physical location of where something had been posted.
What is geotagging?

What is to make discoveries?
What is to steal information?
What is to expose corruption?
What is to protect information?
Use at least 3 of the following with at least 8 characters denotes:
Numbers
Lower case letters
Upper case letters
Symbols (% # * & ! : { “ > |)

Is an environment, such as a program or operating system that does not physically exist, but is created within another environment. Does not have hardware, a power supply, or other resources that would allow it to run on its own. Essentially allows you to run a computer within your computer.

What is a Virtual Machine (VM)?


Your digital footprint is the mark that you leave behind when using the internet and can shape your online reputation. Your digital footprints can be positive or negative and shape how people see you now or in the future. These are ways to safeguard your digital citizenship.
What is / are _____?
Search yourself online, check privacy settings, think critically before you post, deactivate and delete old accounts, and make a positive footprint to name a few.
Is a previously unknown computer virus or other malware for which specific antivirus software signatures are not yet available. Traditionally, antivirus software relies upon signatures to identify malware.

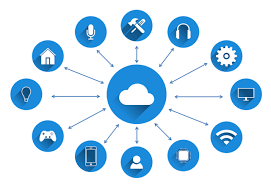
The interconnection via the Internet of computing devices embedded in everyday objects, enabling them to send and receive data.
What is the Internet of Things?
Coordinates a system’s resources so things perform and respond predictably for users. Allows users to configure the computer’s resources without making permanent changes to them. Manages the hardware/software resources so they are used efficiently by applications.

Software designed to block malware from entering protected networks. Screen incoming and outgoing traffic for anomalies and potential threats.


This should be standard security practice for everyone online today. This type of authentication forces anyone logging into an account to supply a code sent to an external device or use other 3rd party software.
What is multi-factor authentication?
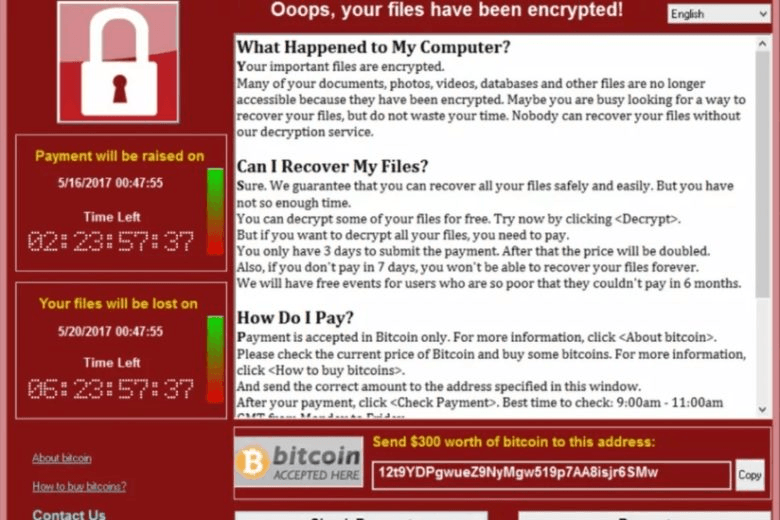
A type of malware that holds victims’ computer files hostage by locking access to them or encrypting them. It then demands a ransom if the victim wants his or her files back.
A piece of software designed to update a computer program in order to fix a software vulnerability or improve the program.
