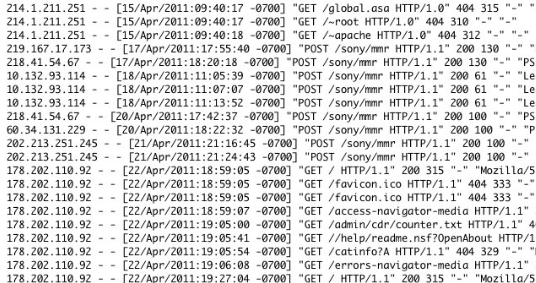
This is the kind of server in the log above
What is an HTTP server?
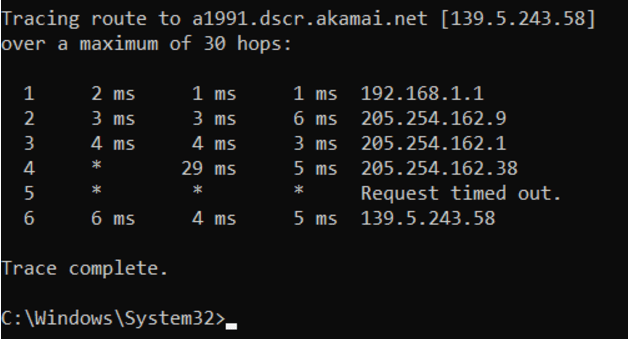
This is the pictured command
What is tracert? This is the Windows command
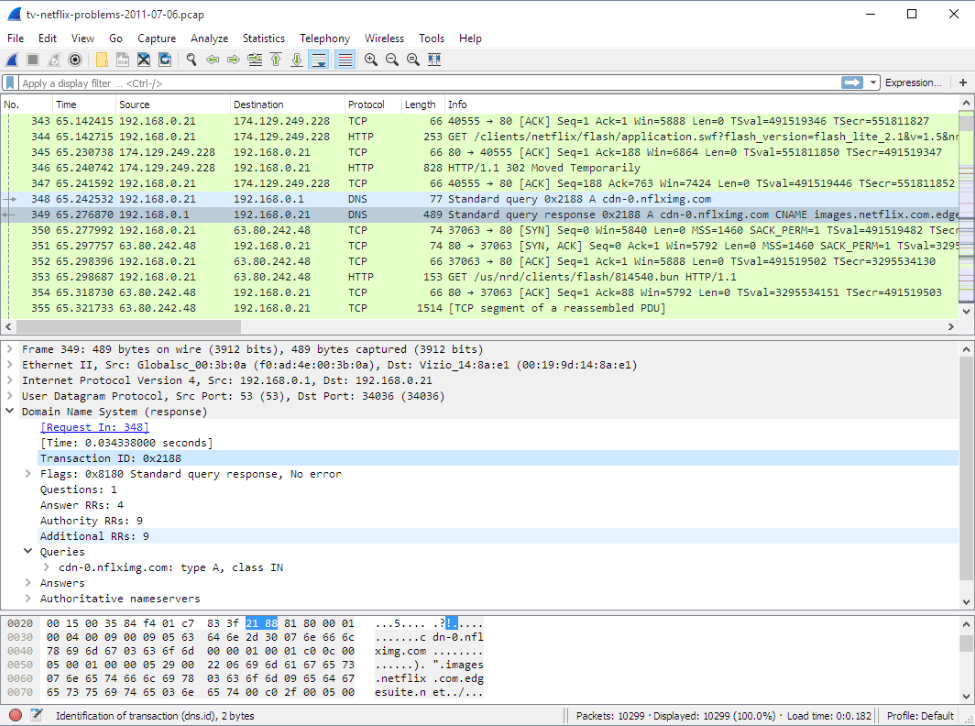 The app pictured above
The app pictured above
What is Wireshark? Packet capture tool
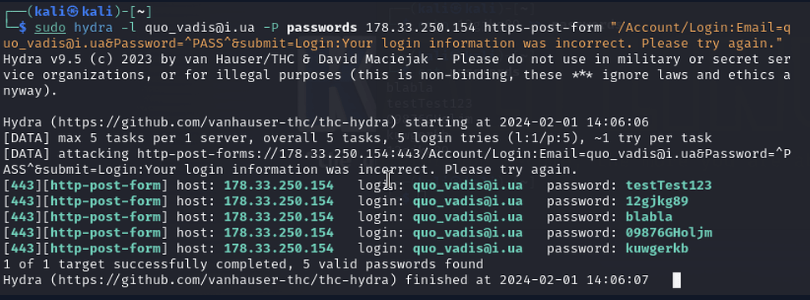 This is the kinds of attacks Hydra is performing above.
This is the kinds of attacks Hydra is performing above.
What is a Dictionary attack and/or Brute force password attack? Hydra is a password attack tool available in Linux
 It's the tool that looks like this!
It's the tool that looks like this!
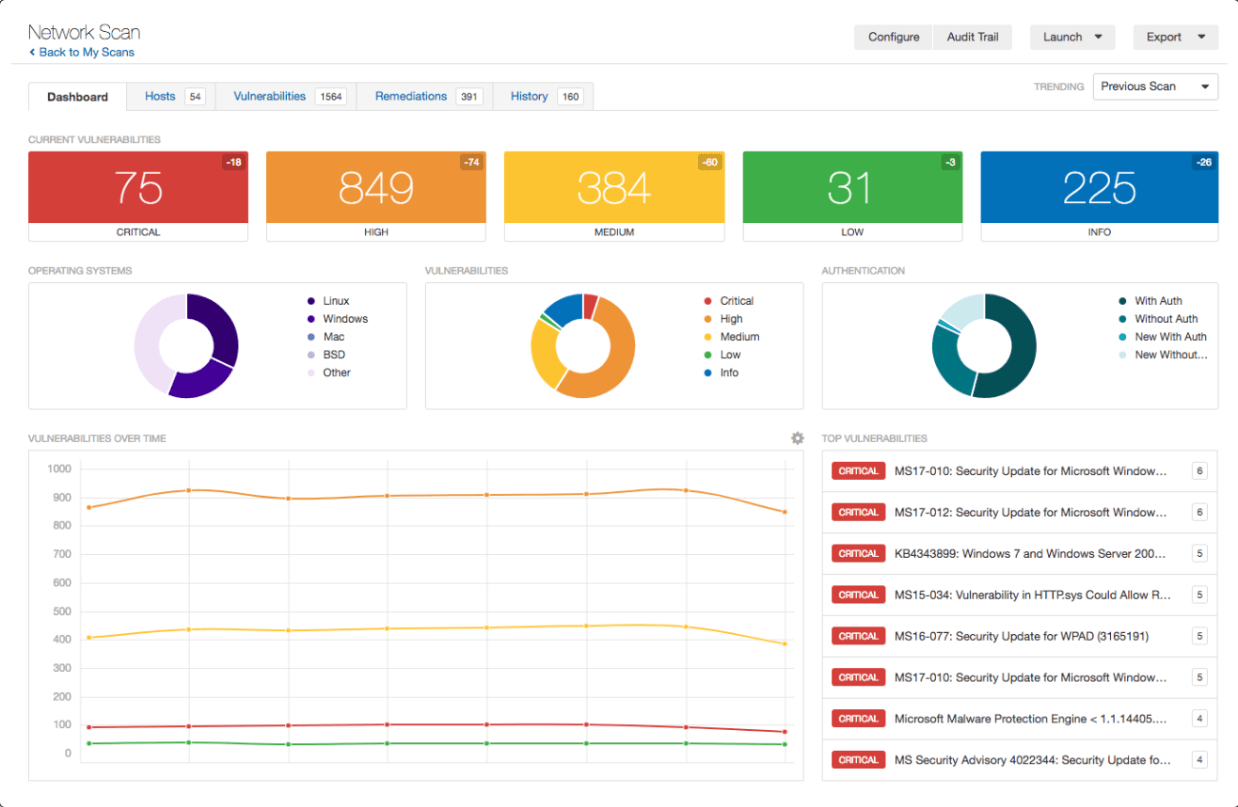
What is Tenable Nessus? Vulnerability scanner
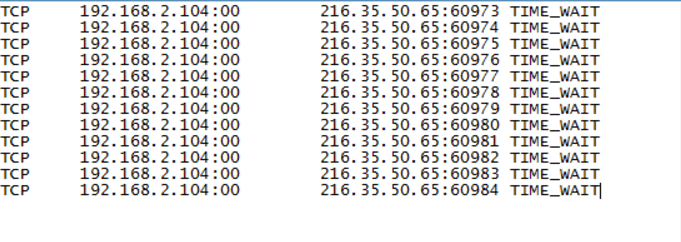 The most likely attack underway in the above log
The most likely attack underway in the above log
What is DoS or DDoS? Notice the contiguous sockets from the same IP
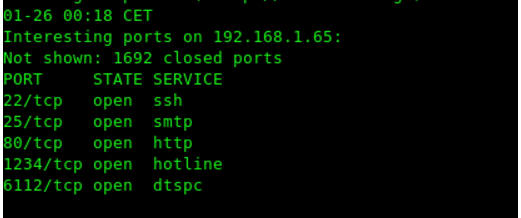 That's the name of the tool displayed
That's the name of the tool displayed
What is nmap?
 The application pictured above
The application pictured above
What is InSSIDer? Wireless network detector
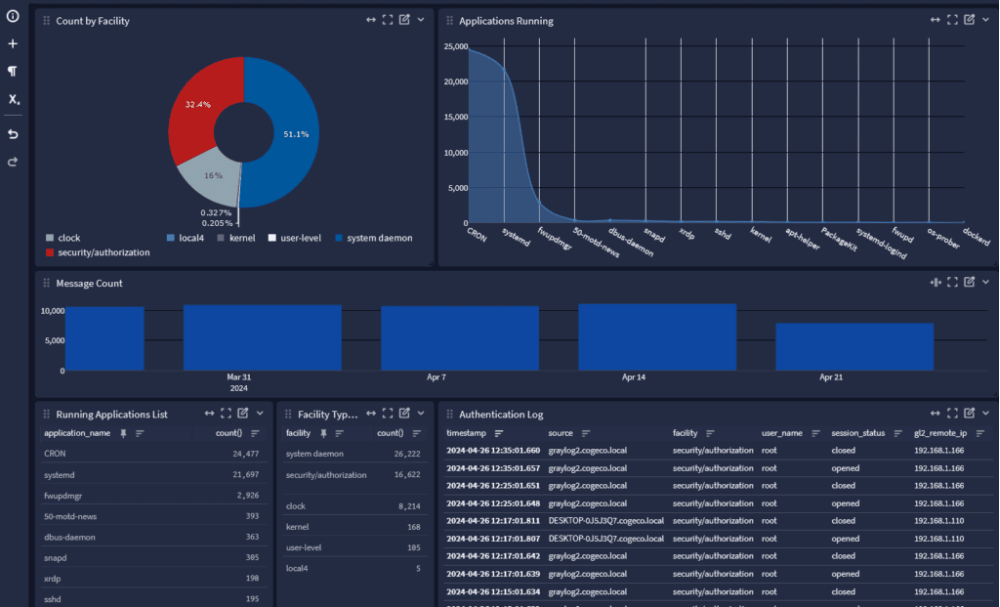 The pictured app
The pictured app
What is Graylog Open? SIEM/log aggregator
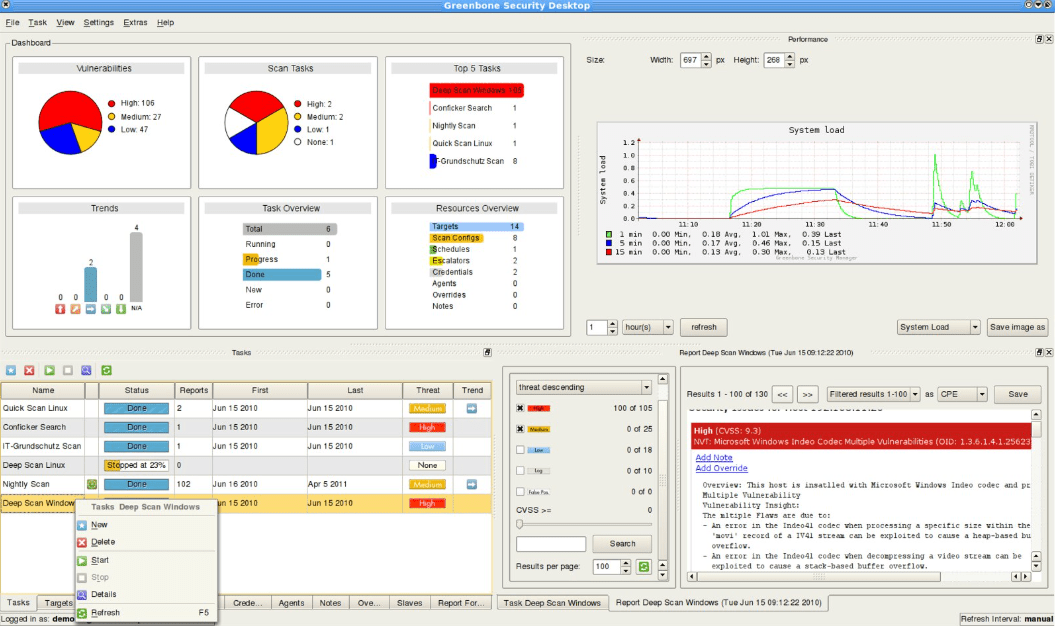
The app pictured
What is Greenbone Security OpenVAS? Vulnerability scanner
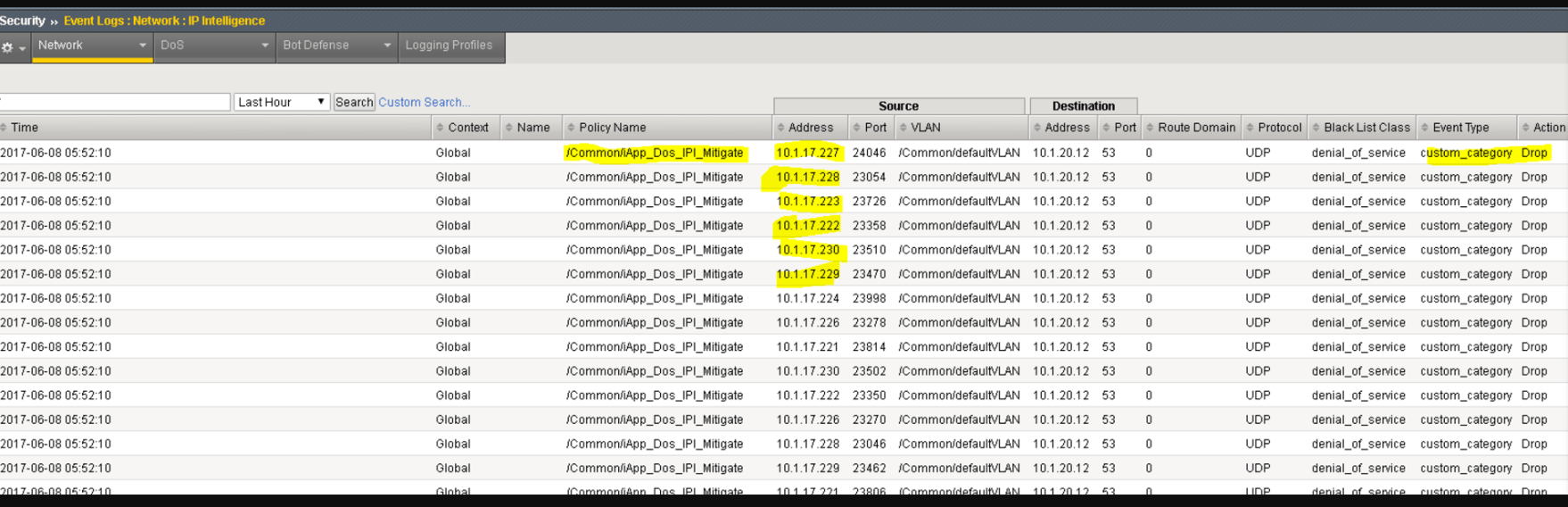
This IPS has been configured to do this to the highlighted connection
What is drop? This is due to previous DDoS attempts from the IP address
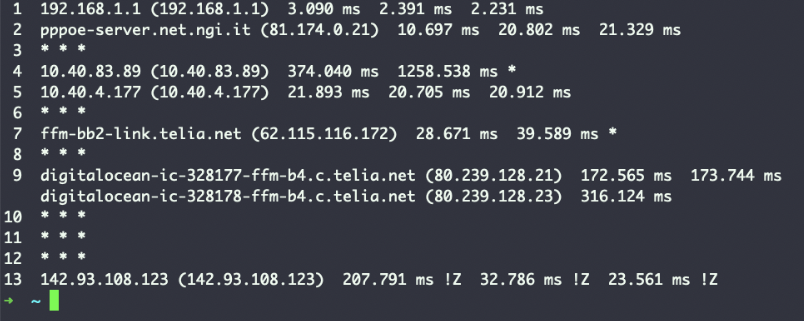 The command pictured above.
The command pictured above.
What is traceroute? This is the Linux command
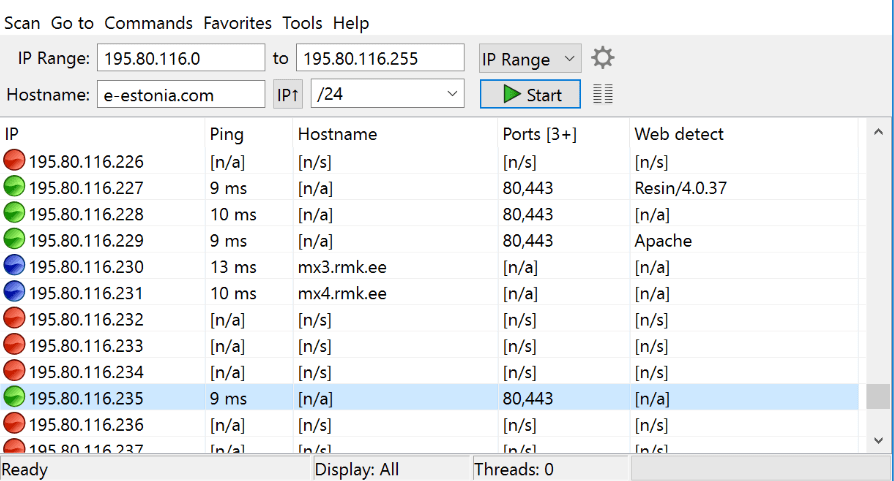 The application pictured above.
The application pictured above.
What is AngryIPScanner? Think of it as a very light version of nmap
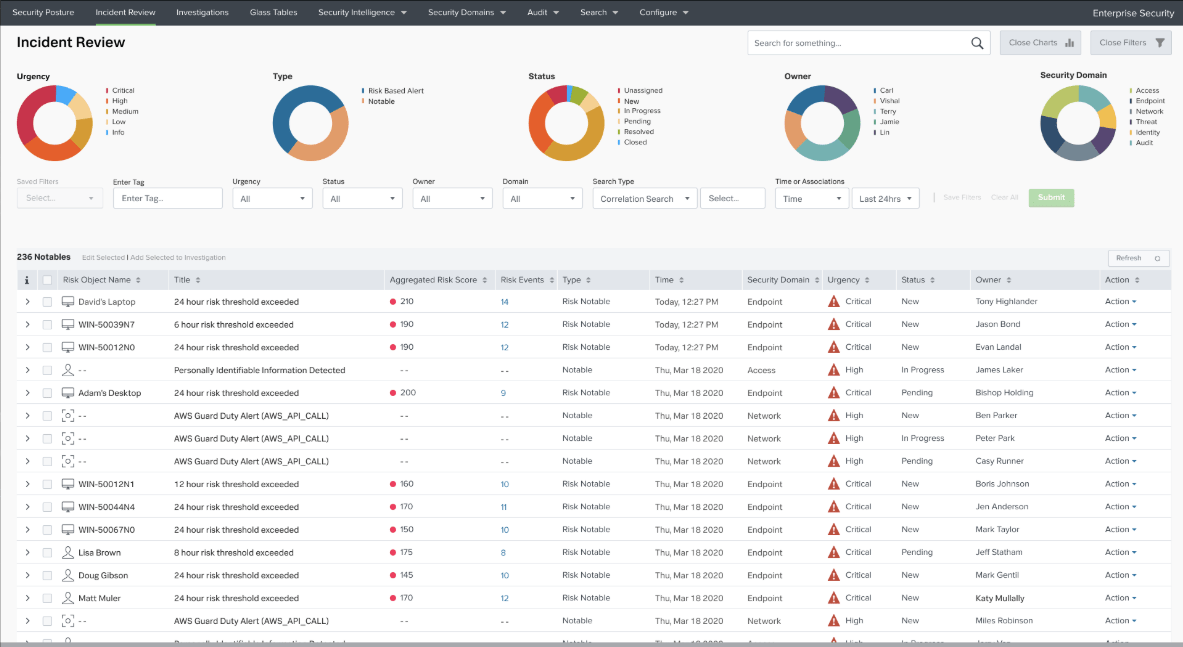 The app pictured above
The app pictured above
What is Splunk (SIEM)?
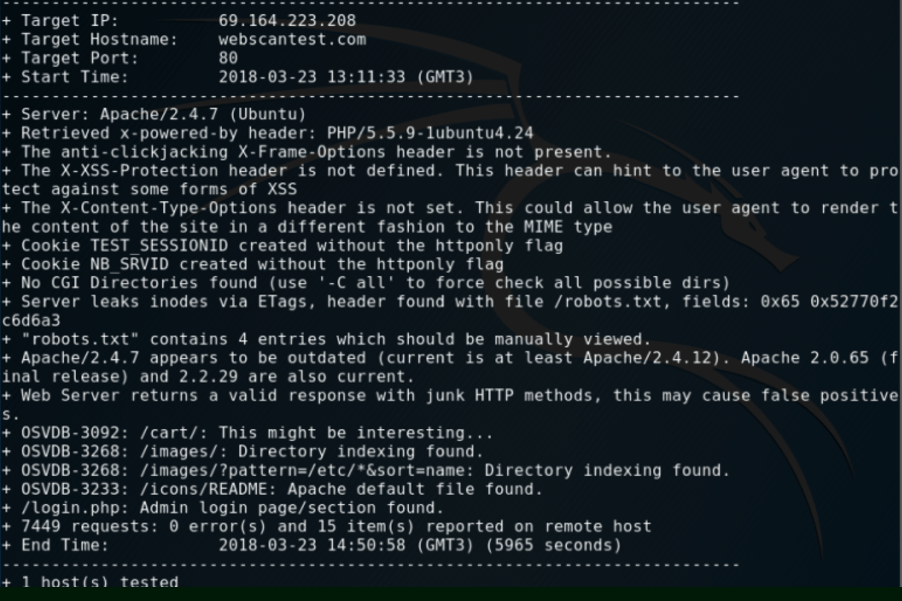
The name of this tool
What is Nikto? Vulnerability scanner
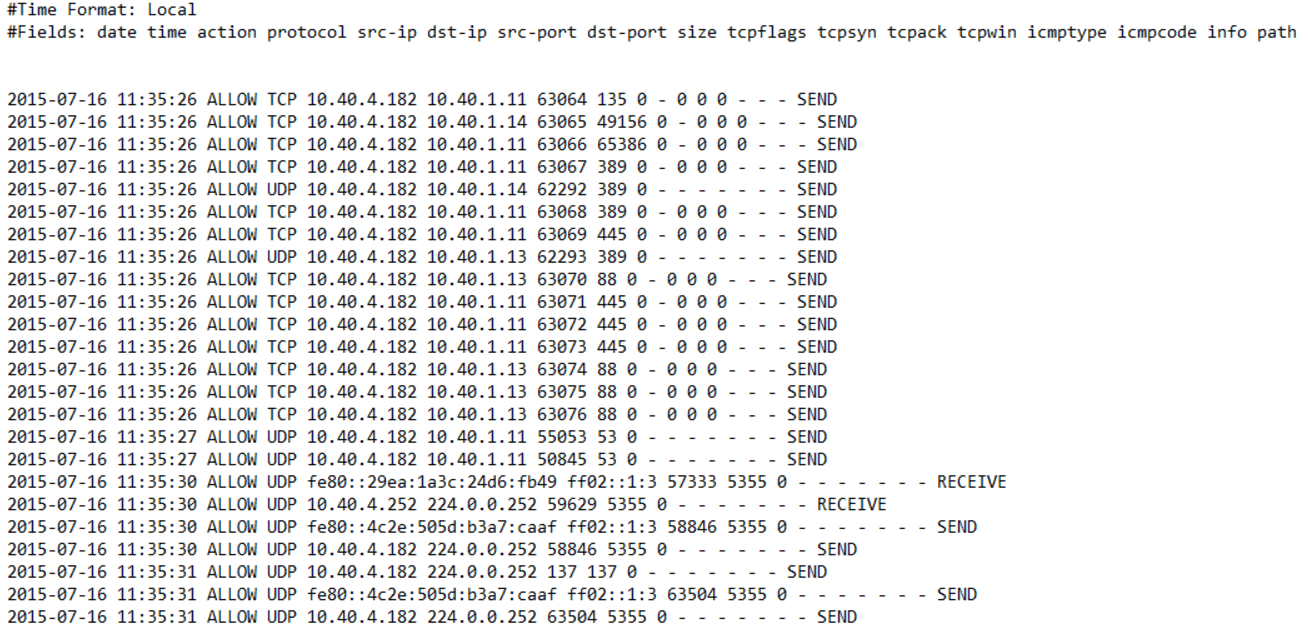 This device/application produced this log file
This device/application produced this log file
What is a Firewall?
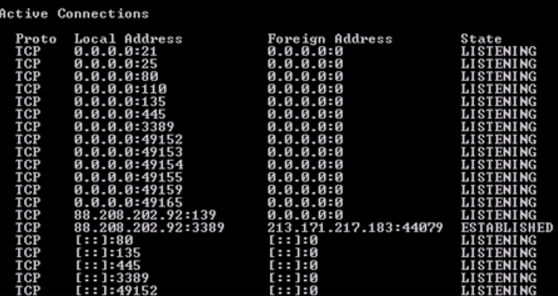 The pictured command
The pictured command
What is netstat?
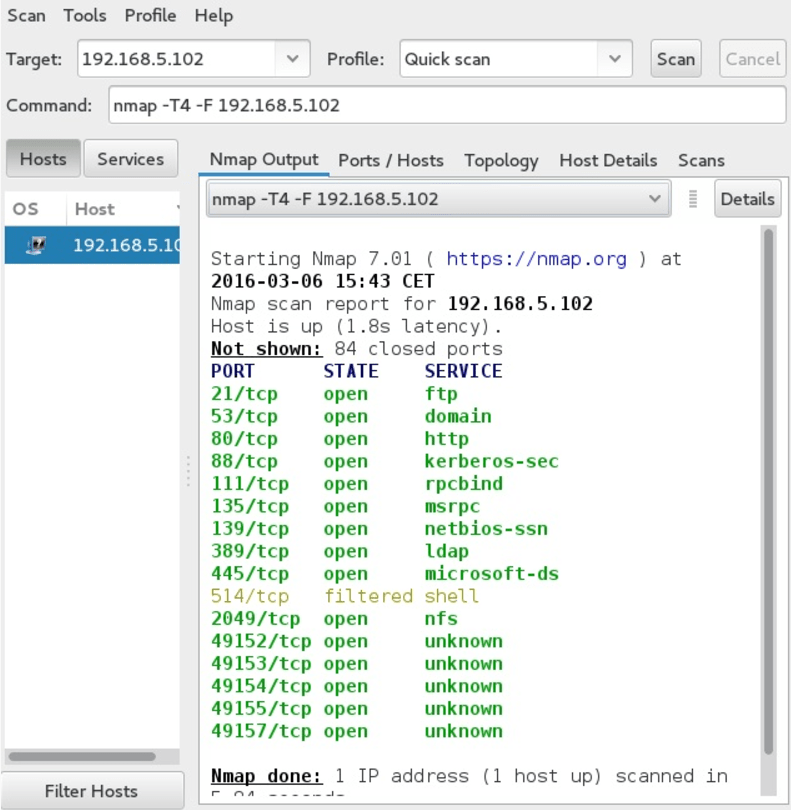 The app pictured above
The app pictured above
What is Zenmap? GUI version of nmap for Windows/Mac
 The app pictured above
The app pictured above
What is Splunk Phantom (SOAR)?
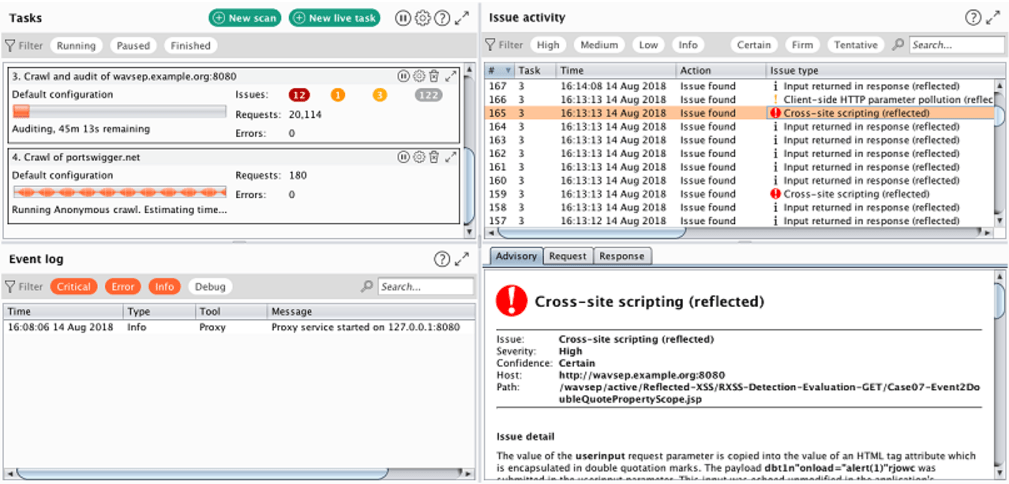
The pictured app
What is Burp Suite? Web app vulnerability scanner
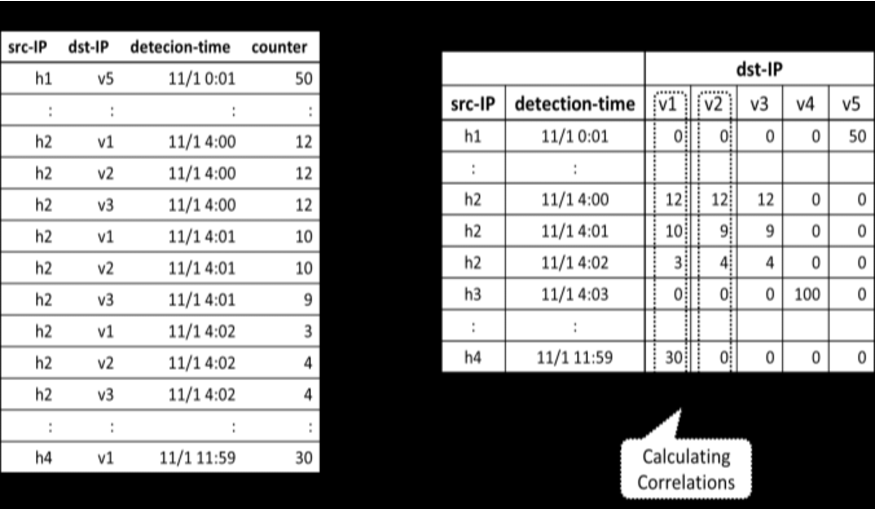 The appliance that generated this table
The appliance that generated this table
What is an Intrusion Detection System IDS? This is a counter log that is correlating actions from remote hosts to the local hosts they are attempting to intrude.
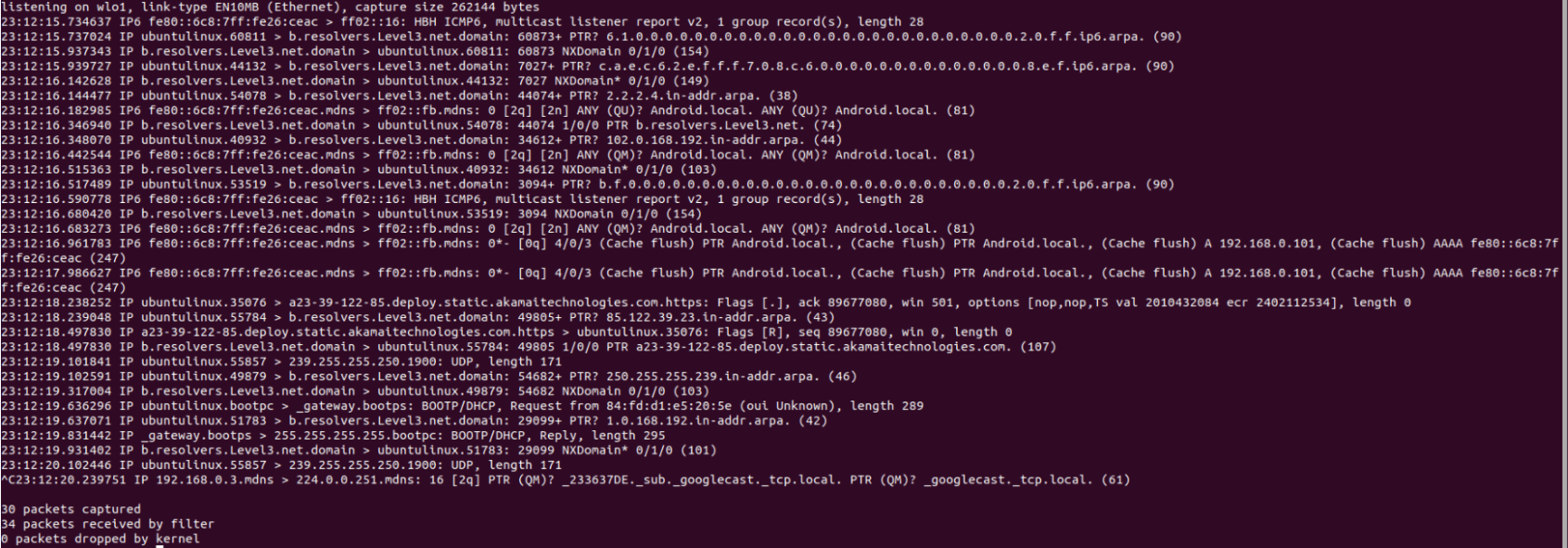
The command pictured above
What is tcpdump?
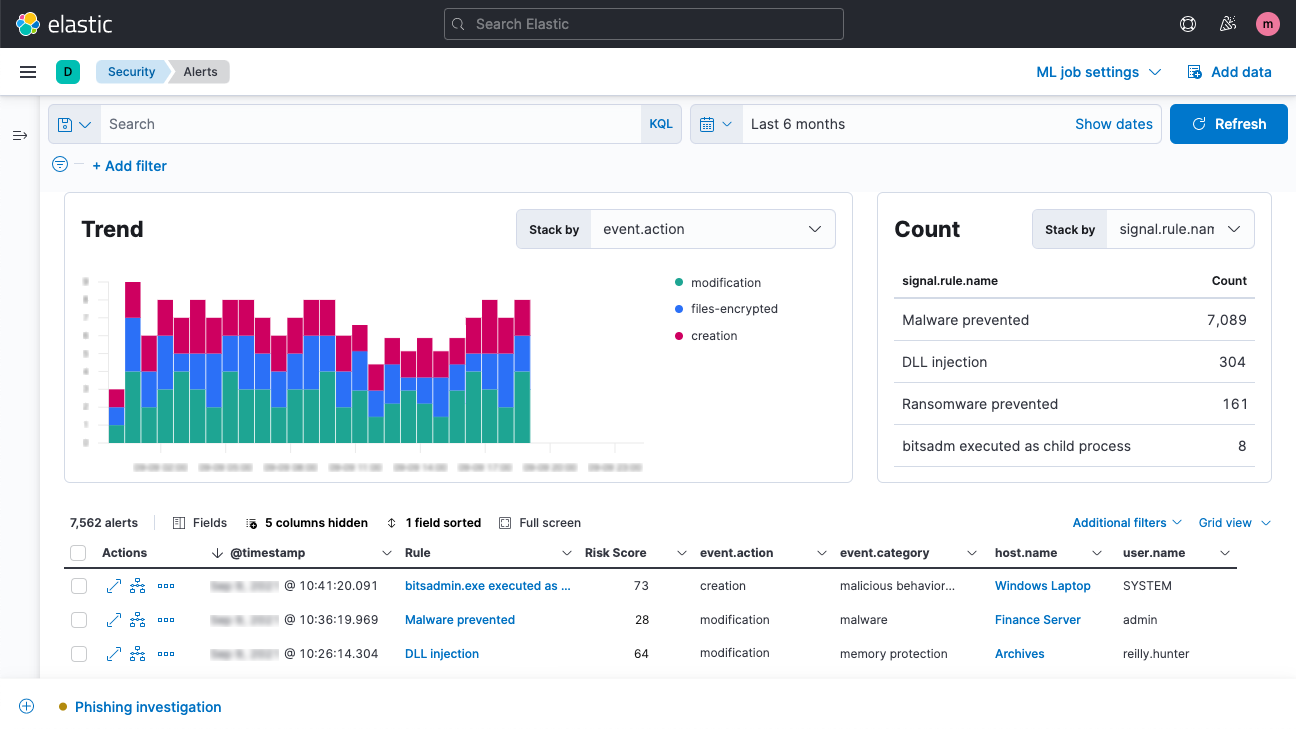 The app pictured above
The app pictured above
What is Elastic or ELK (SIEM)?
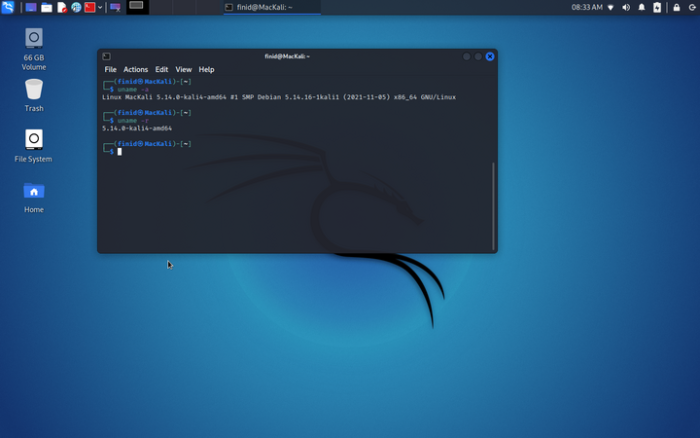 The OS pictured above (Distribution specific)
The OS pictured above (Distribution specific)
What is Kali Linux?
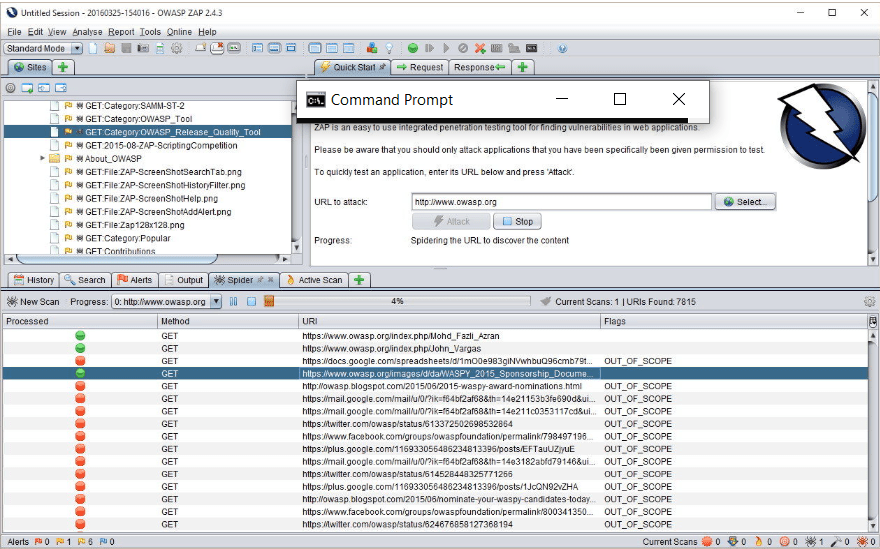 The name of this application
The name of this application
What is OWASP ZAP (ZED Attack Proxy)? Web app attack platform