Object-Oriented Programming
Computer Organization
Software Lifecycle
Networks
surprise :)
100
A class acquires the properties and methods of a parent class
What is INHERITANCE
100
Fetch, Decode, Execute, Store, is part of the
What is MACHINE INSTRUCTION CYCLE
100
The third stage of the software lifecycle where production/coding happens
What is IMPLEMENTATION
100
The Number of Levels in the Open Systems Interconnection Model
What is 7
100
A wifi network where each PC or terminal connects to the server which is confined to a relatively small geographic area is called a
What is LOCAL AREA NETWORK (LAN)
200
A programming language’s ability to handle different implementations of the same method name
What is POLYMORPHISM
200
This kind of primary memory stores programs permanently and cannot be modified
What is READ ONLY MEMORY (ROM)
200
Three methods of data collection are:
What is QUESTIONNAIRES, INTERVIEWS, BACKGROUND RESEARCH, OBSERVING PEOPLE WITH CURRENT SYSTEM, ETC
200
in this network topology, each node is connected to a central server or computer via a single cable using a hub. Congestion can be an issue. Nodes can be connected or disconnected without disrupting other nodes
What is STAR TOPOLOGY
200
The Fundamental Operations are:
What is ADD, COMPARE, STORE, RETRIEVE
300
Protects/hides data within a given structure
What is ENCAPSULATION
300
this type of memory sits between main memory and the processor. Holds commonly or recently used data or instructions for quick access
What is CACHE
300
Taking the problem and break it into smaller and more manageable components is called using a
What is MODULAR DESIGN
300
Data integrity is ensured using
What is PARITY CHECKING, SUM CHECKS
300
Draw and label a CPU
What is CORRECT DIAGRAM 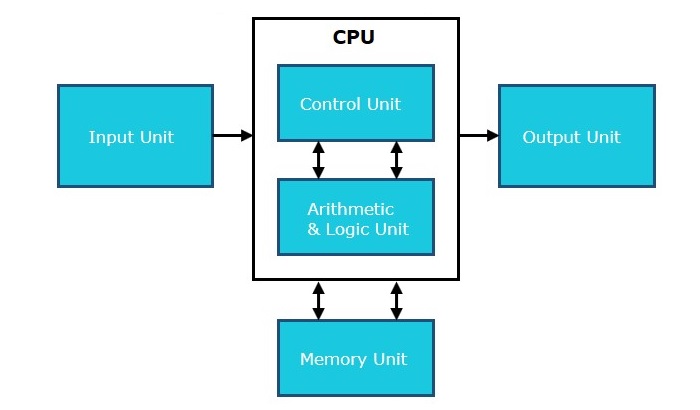
400
A variable belongs to a class not the instantiation
What is STATIC
400
The number 678 (base 10) in hexadecimal and binary!
What is
HEX: 2A6
BINARY: 0010 1010 0110
400
The three types of test data (used in the implementation: testing phase) are called
What is NORMAL, ABNORMAL AND EXTREME DATA
400
Require login, encrypt data, grant permissions based on user type, use a firewall, virus checking software, are all ways to ensure
What is DATA SECURITY
400
The levels of computer language are
What is MACHINE CODE, ASSEMBLY, HIGH LEVEL
500
A "has a" relationship represented by a diamond in a UML diagram
What is AGGREGATION
500
A logic gate diagram for A AND NOT(B OR C )
What is CORRECT DIAGRAM
500
Setting aside old system and put in new system immediately is called a
What is DIRECT CHANGEOVER
500
The most secure, good quality, yet expensive method of transmission media is called
What is FIBRE OPTICS
500
Areas of storage accessible by a unique name, or identifier are
What is VARIABLES