Sequences, selections, and loops are all basic concepts in ___________ ______________.
What is Programming Logic
Where is Career Services located?
What is 108 Nestor Hall
The first programming language that most software developers learn is _______.
What is Java
The protection of computer systems and information from harm, theft, and unauthorized use.
What is Cyber Security
This is a formatting system for displaying material retrieved over the Internet. Using this you can markup tags specify document elements such as headings, paragraphs, and tables.
What is HTML
What is the difference between threat, vulnerability, and risk?
A threat exploits a vulnerability and can damage or destroy an asset. Vulnerability refers to a weakness in your hardware, software, or procedures and risk refers to the potential for lost, damaged, or destroyed assets.
Name three services provided by Career Services.
What are resume reviews, practice interviews, career exploration, job & internship search strategies, LinkedIn review, Career Success Plan, and Student Employment.
Name two common programming languages
What is C, C++, C#, Java, Python, Go, R Swift, PHP, or Ruby
What are the three types of basic control structures?
Sequence, Loops, and Selection
___________ Certification is the preferred qualifying credential for technical support and IT operational roles and will help you launch your IT career – it's about much more than PC repair.
What is CompTIA
Name two devices needed to make a network?
What are switches and routers?
The name of Career Services job board is _________.
What is Handshake
______ is widely used for developing desktop applications, web applications and web services. It is used in creating applications of Microsoft at a large scale.
What is C#
It refers to the safeguarding of data held in a digital environment or in ______ infrastructures for an organization. It employs a variety of _____ service providers, including AWS, Azure, Google, and others, to assure protection against a variety of threats.
What is Cloud Security
___________ ____________ __________is a process that produces software with the highest quality and lowest cost in the shortest time. It involves several distinct stages, including planning, design, building, testing, and deployment.
What is the Software Development Life Cycle.
What are the number of bits in a byte?
What is 8
How long can you work with Career Services after you graduate?
What is up to one year after graduation
Name three datatypes
What is String, boolean, integer, float, double, single, or money
A _________ ________ is responsible for keeping an organization's computer network up-to-date and operating as intended.
What is a Network Administrator
What are the steps to set up a firewall?
1. Secure your firewall, 2. Architect your firewall zones and IP addresses, 3. Configure access control lists, 4. Configure other firewall services, 5.Test your firewall configuration.
_______is the ideal foundational certification to get started on a career working with cutting-edge information technologies. It covers mobile, tablets, laptops, desktops and beyond. The exam verifies an individual can troubleshoot networking and security issues within operating systems such as Linux, Android, Windows and more.
What is the A+ Certification
What is the name of Career Services Director?
Who is Lenroy Jones
_________ ________ is a process for defining, detecting, and prioritizing vulnerabilities in computer systems, network infrastructure, applications, and other systems, as well as providing the necessary information to the organization to correct the flaws.
What is Vulnerability Assessment
___________ ___________ conceive of, design, and build computer programs. Some develop new applications for mobile or desktop use, while others build underlying operating systems.
What is a Software Developer
This is the implementation of the program's requirements and design.
What is Programming Logic
Name three I/O devices for a computer
What is a mouse, keyboard, monitor, printer, and or speaker.
Knowing work environments differ greatly, understand and demonstrate effective work habits, and act in the interest of the larger community and workplace. What is this NACE Competency?
What is Professionalism
______ is a sort of cybercrime in which the sender appears to be a legitimate entity such as PayPal, eBay, financial institutions, or friends and coworkers. They send an email, phone call, or text message to a target or target with a link to convince them to click on the link.
What is Phishing
These professionals administer, test, and implement computer databases, applying knowledge of database management systems. Coordinate changes to computer databases. May plan, coordinate, and implement security measures to safeguard computer databases.
What is a Database Administrator
__________ _________ Is a method of identifying vulnerabilities in a network, system, application, or other systems in order to prevent attackers from exploiting them. It is most commonly used to supplement a web application firewall in the context of web application security (WAF).
What is Penetration Testing
_______ ________ _______refers to a group of software development methodologies based on iterative development, where requirements and solutions evolve through collaboration between self-organizing cross-functional teams.
What is Agile Software Development
Proactively develop one’s career through continual personal and professional learning, awareness of one’s strengths and weaknesses, navigation of career opportunities, and networking to build relationships within and without one’s organization. What is this NACE Competency?
What is Career & Self-Development
What is Paas?
What is Platform as a service
What is laas?
What is Infrastructure as a service
What is Saas?
What is Software as a service
________ serves as a barrier between a LAN and the Internet. It allows private resources to remain private while reducing security threats. It manages both inbound and outbound network traffic.
What is a Firewall
What is the name of the Career Services program that allows you to meet with professionals in your career field of interest?
What is Exploration Programs
What does DRY Stand for?
What is Don't Repeat Yourself
When going from onsite computing to cloud computing enterprises have 3 options. Which cloud model is unnamed in this image?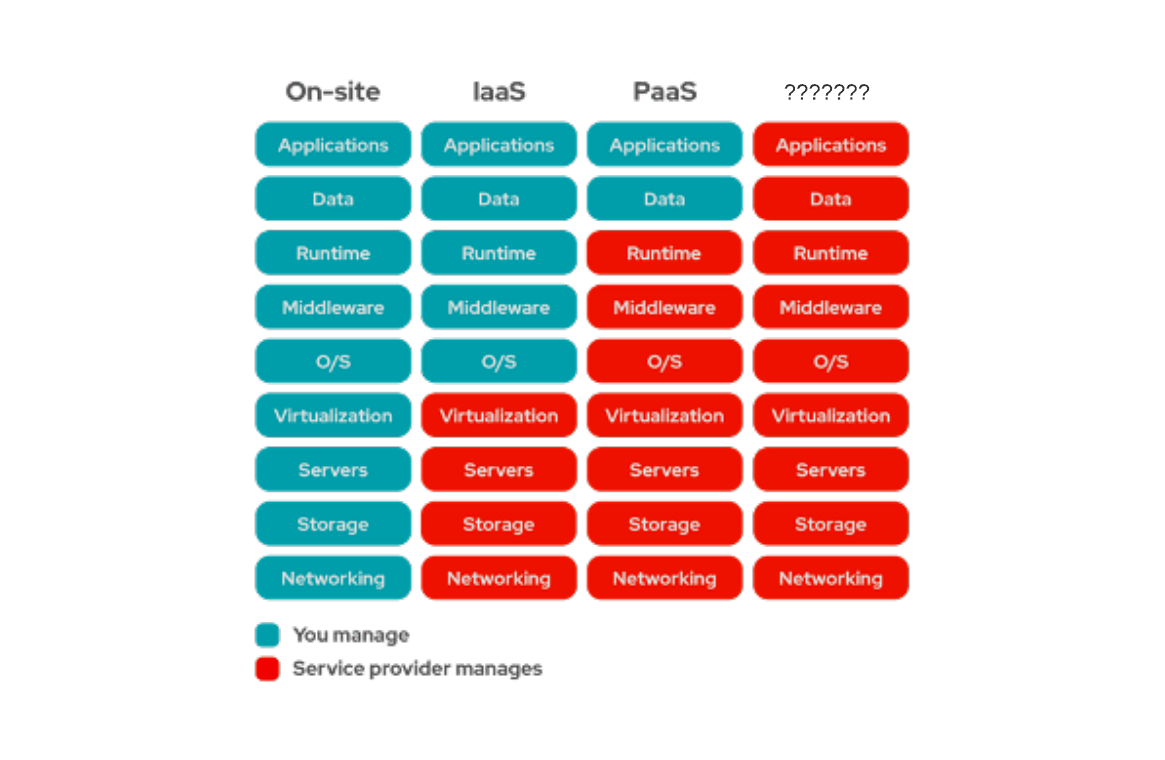
This is an authorized attempt to gain unauthorized access to a computer system, application, or data. This involves duplicating strategies and actions of malicious attackers. This practice helps to identify security vulnerabilities which can then be resolved.
What is Ethical Hacking