In cloud security, what is the core principle of Identity and Access Management (IAM) that ensures users and systems are granted only the minimum permissions needed to perform their tasks?
Principle of Least Privilege
In a cloud environment, what security mechanism enforces fine-grained control over which specific resources a user can interact with — for example, granting access to only certain virtual machines while restricting others?
Authorization
What does an IAM policy define?
Permission and access control rules
After configuring traditional firewall rules to control network traffic, what additional security layer should a cloud engineer implement to defend a web application against application-layer attacks such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities?
WAF
In Google Cloud, what is used to authenticate applications and services, allowing them to securely access Google Cloud resources?
Service Accounts
A company’s web infrastructure is intentionally flooded with excessive traffic, exhausting server resources and causing legitimate users to lose access. What type of cyberattack is most likely responsible for this denial of service?
DDoS Attack (Distributed Denial of Service)
In a cloud environment, you need to give different teams specific access to resources while maintaining security and governance. Which AWS IAM solution lets you assign precise permissions to enable collaboration across teams?
IAM Roles (AWS)
In a cloud environment, an attacker overwhelms a web application by generating a massive volume of seemingly legitimate HTTP or DNS requests, targeting the application layer until performance degrades and services become unavailable. What type of cyberattack does this describe?
Application Layer Attack (e.g., HTTP Flood or DNS Query Flood)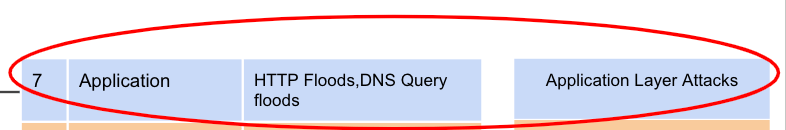
The following image contains an IAM policy for a network engineer.
TWO PART QUESTION:
1) Name the cloud platform where the policy originates.
2) Does the policy follow the principles of least privilege?
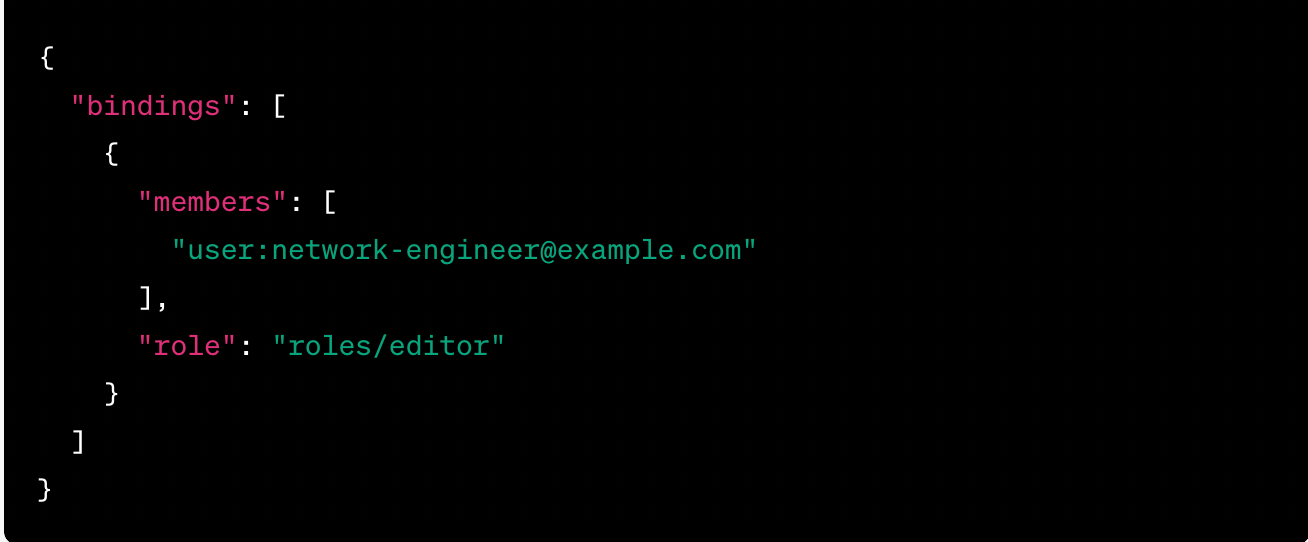
1) Google Cloud Platform (GCP)
2) Policy does not follow the principles of least privilege
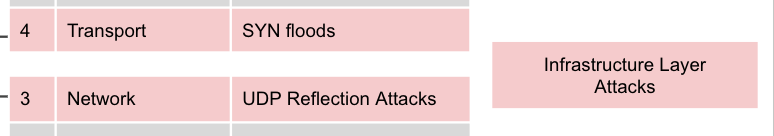
In a cloud environment, a hacker launches a massive flood of network traffic with the intention of overwhelming the network's capacity, causing it to become unresponsive. At what layer would this cyberattack occur?
Infrastructure layer or, Layer 3 & Layer 4 of the OSI model