A secret word or combination of characters that you use to gain access to a computer, application, or website.
What is a password?
Your name, address, phone number, and date of birth are all examples of this type of information.
What is Personal Identifiable Information (or PII)?
A fraudulent email disguised to look like it's from a legitimate company, designed to trick you into revealing personal information.
What is a phishing email?
The general term for any software intentionally designed to cause damage to a computer, server, or network.
What is malware?
The art of manipulating people into giving up confidential information or performing actions.
What is social engineering?
A password like "123456" or "password" is considered this, because it's easy to guess.
What is a weak password?
The trail of data, posts, photos, and comments you leave behind online.
What is a digital footprint?
Phishing attacks that are sent via text message are known by this specific name.
What is smishing?
A type of malware that attaches itself to another program and spreads from computer to computer, often causing damage to data.
What is a computer virus?
You receive a recording of a voice saying: "Hi, this is John from the IT department. We're doing a system-wide password update and I need your current password to verify your account before we can proceed." This phone-based social engineering tactic is called this.
What is vishing (or voice phishing)?
This security method requires two different ways to prove your identity, like a password and a code sent to your phone.
What is Two-Factor Authentication (or Multi-Factor Authentication / 2FA / MFA)?
These small text files are stored on your computer by websites to track your activity and remember your preferences.
What are cookies?
This is the biggest red flag in this email that proves it's a phishing attempt.
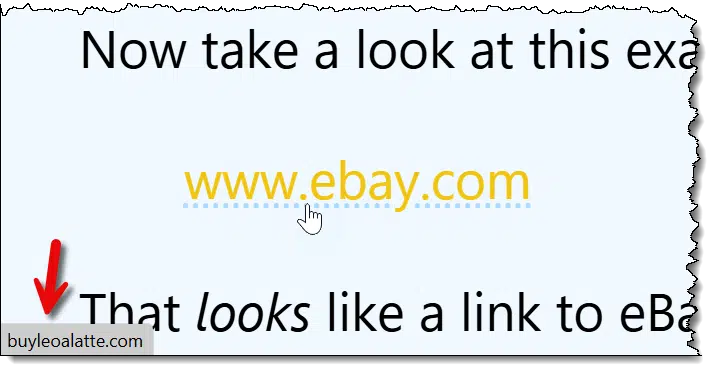
What is the mismatched link/URL?
This type of malware encrypts your files, making them inaccessible, and then demands a payment to get them back.
What is ransomware?
A social engineering tactic where an attacker invents a scenario, or this, to engage a victim in a way that increases the chance the victim will divulge information.
What is pretexting?
A digital tool that securely stores all your complex passwords in one encrypted place, so you only have to remember one master password.
What is a password manager?
A legal document on a website or app that explains what data it collects from users and how that data is managed and used.
What is a privacy policy?
A highly targeted phishing attack that is customized for a specific individual or organization, often using their name and other personal details to seem more convincing.
What is spear phishing?
Unlike a virus, this standalone piece of malware can replicate itself and spread across a network without needing to attach to a host program.
What is a worm?
Leaving a malware-infected USB drive in a public place like an office lobby, hoping an employee will pick it up and plug it into their computer out of curiosity.
What is baiting?
This method of proving you're not a robot is called this.
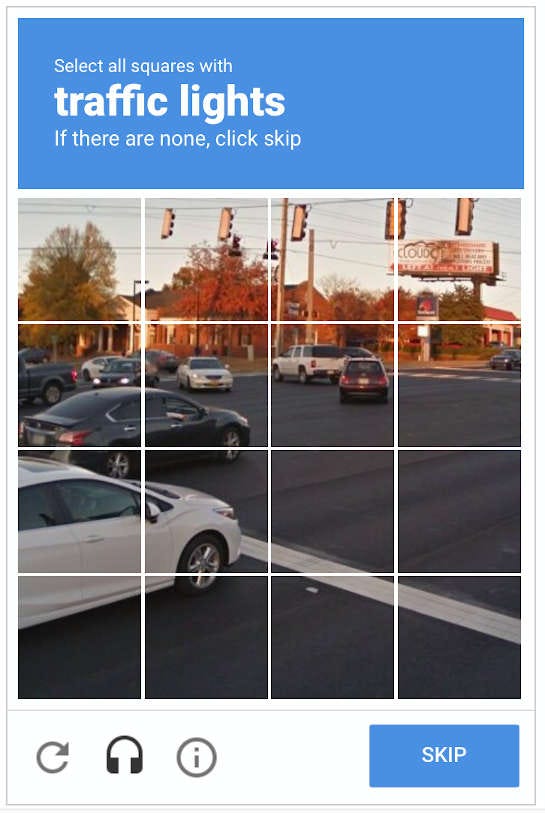
What is a CAPTCHA (or reCAPTCHA)?
The practice of companies collecting vast amounts of user information, often for targeted advertising or analysis.
What is data mining (or data harvesting)?
This type of phishing targets high-profile individuals like CEOs or other senior executives within a company.
What is whaling?
Malware disguised as legitimate software, which tricks users into installing it. It's named after a famous wooden gift from Greek mythology.
What is a Trojan horse (or Trojan)?
An attacker who follows an authorized person into a secure area by walking in right behind them before the door closes is performing this type of social engineering attack.
What is tailgating (or piggybacking)?