A less than one-year-old open-source artificial intelligence chat box.
What is ChatGPT?
Emails, phone calls, and texts.
What are forms of fraud and phishing?
A method to explore Google hacking.
What is Google Dorking?
This is a representation of information, including digital and non-digital formats, that represents facts, concepts, or instructions in a manner suitable for communication, interpretation, or processing by humans or by automatic means.
What is data?
These include major applications, general support systems, high impact programs, physical plants, mission critical systems, personnel, equipment, or a logically related group of systems that you want to protect.
What are assets?
The pigpen cipher is a geometric simple substitution cipher, which exchanges letters for symbols that are fragments of a grid.
What is Freemason Cipher?
The fraudulent practice of sending emails or other messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
What is phishing?
Privacy, accuracy, property, and accessibility.
What are the four major issues of information ethics in the information age?
This programming language makes use of the terms variables, loops, conditionals and functions, but it does not require compilation.
What is Phython?
This career field involves the practice of gathering, retaining, and analyzing computer-related data for investigative purposes in a manner that maintains the integrity of the data and the science is applied to the law.
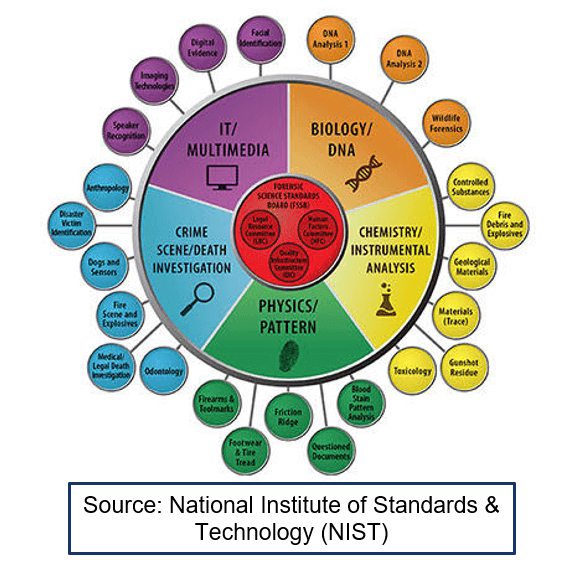
What is forensics?
Used by Julius Caesar around 58 BC, is a substitution cipher that shifts letters in a message to make it unreadable if intercepted. To decrypt, the receiver reverses the shift.
What is Caesar’s Secret Code?
A person or thing intended to deceive others, typically by unjustifiably claiming or being credited with accomplishments or qualities.
What is fraud?
This list represents certain principles.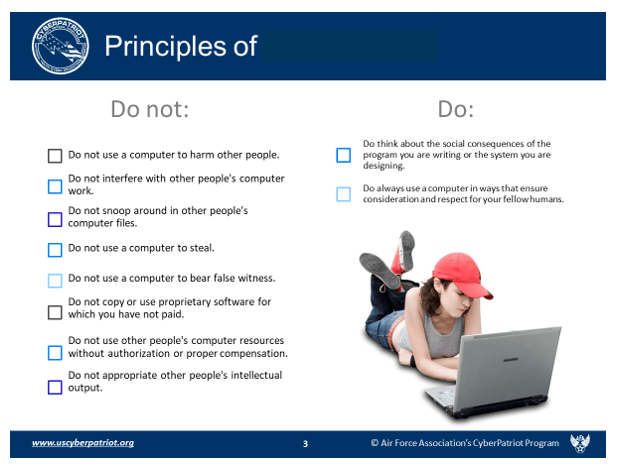
What are Cyber Ethics?
This command displays a list of files in the current open directory.
What is ls?
This term describes Information system(s) that are implemented with a collection of interconnected components. Such components may include routers, hubs, cabling, telecommunications controllers, key distribution centers, and technical control devices.
What is a network?
A code that allows computers to manipulate and store all types of information to and from computer memory.
What is Binary Code?
Hover over email and website addresses, verify with the named sender, and ask detailed questions if the phone is used as a bait method.
What are ways to detect and protect yourself from fraud and phishing?
This website uses advanced Google searches for internet connected devices.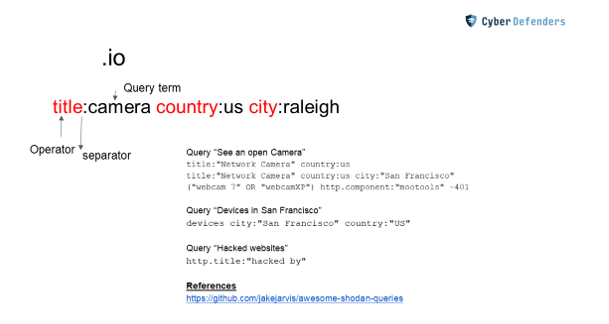
What is Shodan?
Knowledge of Python programming can be used to solve problems like these or related to these tools (name 2).
What are sorting through lists, analyzing finances, determining stocks to invest in, machine learning, artificial intelligence, data visualization, data collecting, data mining or data manipulating.
The goal of this project at the National Institute of Standards and Technology (NIST) is to establish a methodology for testing computer forensic software tools by development of general tool specifications, test procedures, etc.
What is Computer Forensic Tool Testing (CFTT)?
A Boolean logic operation that is widely used in cryptography as well as in generating parity bits for error checking and fault tolerance.
What is XOR? (eXclusive OR)
A method of encrypting or signing data with two different keys and making one of the keys available for anyone to use. The other key is known as the private key.
What is Public key cryptography?
This learning tool allows one to allows you to write and execute Python in their internet browser, without needing to configure.
What is Google Colab or Colaboratory?
These are several action steps (provide just three) of someone who wants to learn programming in ten years.
What are paying attention to details, working on projects, reading codes, collaborating on projects, talking with other programmers, joining github, working on well defined tasks and practicing repetition.
These are 3 concepts of physical security.
What are prevention, detection and recovery?