What is an IP Address? What is the purpose?
A number assigned to any item that is connected to the Internet. IP addresses provide a unique number for identifying devices that send and receive information on the Internet
What do we call software designed to harm, exploit, or disrupt a system?
What is Malware?
What is the time elapsed between the transmission and the receipt of a request.
Latency
Defined as the website names that use words and letters to describe them
Domain names
What is a difference between Analog and Digital Data?
Analog Data= smooth data
Digital Data= Choppy copy
What is one simple practice that greatly increases account security?
Strong and unique Passwords
What is a Packet?
Small chunks of information that have been carefully formed from larger chunks of information. How information is sent over the internet. The internet traffic process in which information is broken into smaller packets that are sent along different routes, and reassembled at their destination
What kind of cyber attack tricks people into giving away sensitive information through fake emails or messages?
Phishing.
One is the massive network of physical connections like cables and routers, and the other is the system of webpages that lives on top of that network.
What is the difference between the Internet and the World Wide Web?
What’s the function of the DNS (Domain Name Service)?
Translating the site name in text format to a numeric IP address
Which value is greater: 135 or 10000111?
135= 10000111
What process scrambles data so it can only be read with a key?
Encryption
What is a computer network?
A computer network is any group of interconnected computing devices capable of sending or receiving data.
What type of attack overwhelms a website or server with excessive traffic, causing it to crash?
A Distributed Denial of Service (DDoS) attack.
Which of the following is true of how the Internet has responded to the increasing number of devices now using the network?
Moore's Law- The protocols of the Internet were designed to SCALE as new devices are added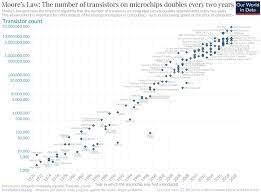
Which part of a domain name is the top-level domain (TLD)?
The far right side of the domain name
8 bits is enough to represent 256 different numbers. How many total bits do you need to represent 513 different numbers
10 bits
What security method requires two or more ways to verify a user’s identity?
Multi-Factor Authentication (MFA)
What is Fault Tolerance?
The Internet having a lot of redundancy and duplication built into it makes it have this trait
What attack relies on manipulating people rather than breaking technical systems?
Social engineering.
What is a measure of bit rate - the amount of data (measured in bits) that can be sent in a fixed amount of time?
What is Bandwidth
What does URL stand for?
Uniform Resource Locator
What is the difference between lossy vs lossless compression?
Lossy: Compression that removes data that can’t be returned to its original format
Lossless: Compression that removes data that can be returned to its original format
What security tool monitors and controls incoming and outgoing network traffic to block threats?
A firewall.
How does HTTP represent a level of abstraction?
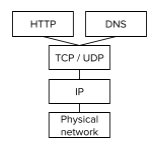 HTTP is built on top of TCP/IP and other layers of protocols. At this higher level, we do not need to know how the lower levels work exactly.
HTTP is built on top of TCP/IP and other layers of protocols. At this higher level, we do not need to know how the lower levels work exactly.
Q: What type of malware locks or encrypts a user’s files and demands payment to restore access?
Ransomware
What is difference between TCP and UDP?
Transmission Control Protocol (TCP)- quality
User Datagram Protocol (UDP)- speed
What’s the syntax of second-level domains?
In ASCII, the uppercase letter "G" is represented by the decimal (base 10) value 71. What would be the letter Q written in the decimal (base 10) value?
81= 01010001
In public-key cryptography, what key is shared openly and what key must remain secret?
The public key is shared; the private key remains secret.