This person hosts Crash Course's Media Literacy series.

Who is Jay Smooth?
This what we call the trail of data created by online activities, including social media, internet searches, and website visits.
What is a digital footprint (sometimes referred to as a digital tattoo)?
Properly citing sources, using quotation marks for direct quotes, and paraphrasing while crediting the original author(s) prevent essay writers from committing this "academic crime."
What is plagiarism?
This current long-running animated TV series, first aired in 1989, follows this cartoon family in the fictional town of Springfield.

What is the Simpsons?
Steve Jobs is the co-founder of this historic computing company that would go on to invent the iPhone.

What is Apple?
Media is the plural form of this term.
What is medium?
In the future, these people will likely attempt to review your social media to determine if you belong in their organizations.
Who are future employers or college admissions officers?
This provides the creator with exclusive rights to reproduce, distribute, display, and perform their work.

What is copyright?
This 1977 science fiction film directed by George Lucas became a cultural phenomenon and launched a movie franchise.
What is Star Wars (IV: A New Hope)
Launched in 2004, this social media platform was originally created by Mark Zuckerberg and his college roommates?
What is Facebook?
For every conscious reaction and response you have to media, this human organ is also subconsciously reacting and responding.
What is the brain?
Full names, addresses, phone numbers, and social security numbers are all considered this.

What is personal information?
The APA (American Psychological Association), MLA (Modern Language Association), Chicago/Turabian provide these for academic writers.
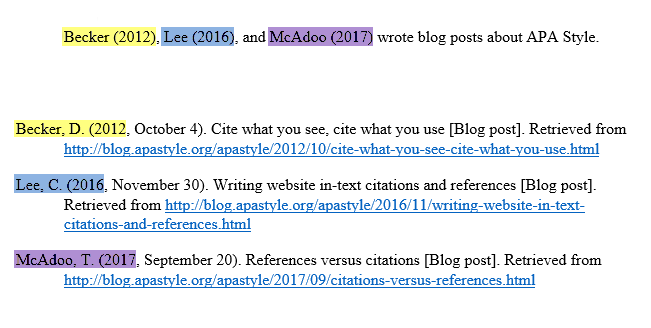
What are citation styles?
This famous music festival held in 1969 became synonymous with the counterculture movement and featured performances by Jimi Hendrix and Janis Joplin?

What is Woodstock?
In 1981, this U.S. President survived an assassination attempt by a would-be assassin named John Hinckley Jr.

Who is Ronald Reagan?
Cultural defensiveness, political defensiveness, and moral defensiveness are all forms of this type of "protection."
What is protectionism?
The use of strong, unique passwords, enabling two-factor authentication, and regularly reviewing and updating privacy settings can prevent uninvited outsiders from doing this.

What is getting hacked (similes are acceptable)?
Websites that lack authorship, contain biased content, cite outdated information, and lack citations are signs of this.
What are being an unreliable source?
This late artist, often referred to as the "King of Pop," was a dominant figure in the music industry during the late 20th century.
Who is Michael Jackson?
She was the first woman to be named to the US Supreme Court?

Who is Sandra Day O'Connor?
This is what we call it when we can’t exactly recall the details of an event, and our brains will just fill in the blanks with something that makes sense.
What is false memory?
These features allow users to control who can see their posts, limiting the audience and potential impact.

What are privacy settings?
A primary source is created at the time of the event, while this type of source interprets or analyzes primary sources.
What is secondary?
This 1980s technology became a popular format for music storage. It replaced replacing cassette tapes and vinyl records. Some cars still play these to this day.
What are compact discs (CDs)?
The fall of this country in 1991 marked the end of the Cold War.

What is the Soviet Union?