This is the risk of reusing passwords.
[A] What is sharing passwords with friends on Netflix, and them trying it on another type of site to login as you?
[B] What is compromised accounts that allow known passwords to be sold on the Dark Web for use against other accounts?
[C] What is having a lot of open sessions on your browser, which someone could shoulder-surf?
[B] What is compromised accounts that allow known passwords to be sold on the Dark Web for use against other accounts?
(Half-credit for [A])
One day, the customer database of one of the online stores Mark has an account at suffers a leak (apparently it was kept unencrypted on an open-access server). No credit card information is stolen, but e-mail addresses, names, and passwords are. At first glance, there seems no particular reason to worry. Such leaks happen [...]
But the cybercriminals who ransacked the database decide to try their luck — maybe someone on the list uses the same password for their e-mail account? They strike gold: Mark uses the same password everywhere, handing the cybercriminals access to his e-mail on a platter. There, they find not only photos that Mark sent to Lucy, but messages from Amazon, eBay, and other companies. Surely Mark doesn’t use the same password for these accounts too? They try logging in to his Amazon account, and presto: same password again.
https://www.kaspersky.com/blog/never-reuse-passwords-story/24808/
This is a common technique phishers use to get the target to reply with their information.
[A] What is RSVPing?
[B] What is gambling?
[C] What is pressuring?
[D] What is eavesdropping?
[C] What is pressuring?
Phishing is a type of attack that uses email or a messaging service to fool you into taking an action you should not take, such as clicking on a malicious link, sharing your password, or opening an infected email attachment. Attackers work hard to make these messages convincing and tap your emotional triggers, such as urgency or curiosity.
This is considered bad practice for dealing with ransomware.
[A] What is paying the ransom to return services?
[B] What is tracing the attack?
[A] What is paying the ransom to return services?
https://www.cisa.gov/sites/default/files/publications/CISA_MS-ISAC_Ransomware%20Guide_S508C.pdf
Paying the ransomware hackers only makes it worse
There are two very basic reasons why it’s never a good idea to pay the ransom:
- There’s no guarantee you’ll get your data back.
- Paying the ransom only supports the business of ransomware.
At the 2018 DEF CON hacking convention in Las Vegas, this aged kid hacked replica of the Florida Secretary of State's website within 15 minutes, altering vote count reports on the site.
[A] What is 6 years old?
[B] What is 11 years old?
[C] What is 13 years old?
[D] What is 15 years old?
This is a way for hackers to better guess answers to your password hints and/or password.
[A] What is the I Ching?
[B] What is the Dark Web?
[C] What is OSINT?
[C] What is OSINT? (Open-Source Intelligence)
[W]ith the constant dissemination of personal information on social media or through social engineering, the answers to these prompts are easy to find, making it easy for attackers to breach [...] user’s accounts.
https://auth0.com/blog/dont-pass-on-the-new-nist-password-guidelines/
A targeted attack on a particular person or organization.
[A] What is spear phishing?
[B] What is advanced tactical approach?
[C] What are Russian hackers?
[D] What is gold phishing?
[A] What is spear phishing?
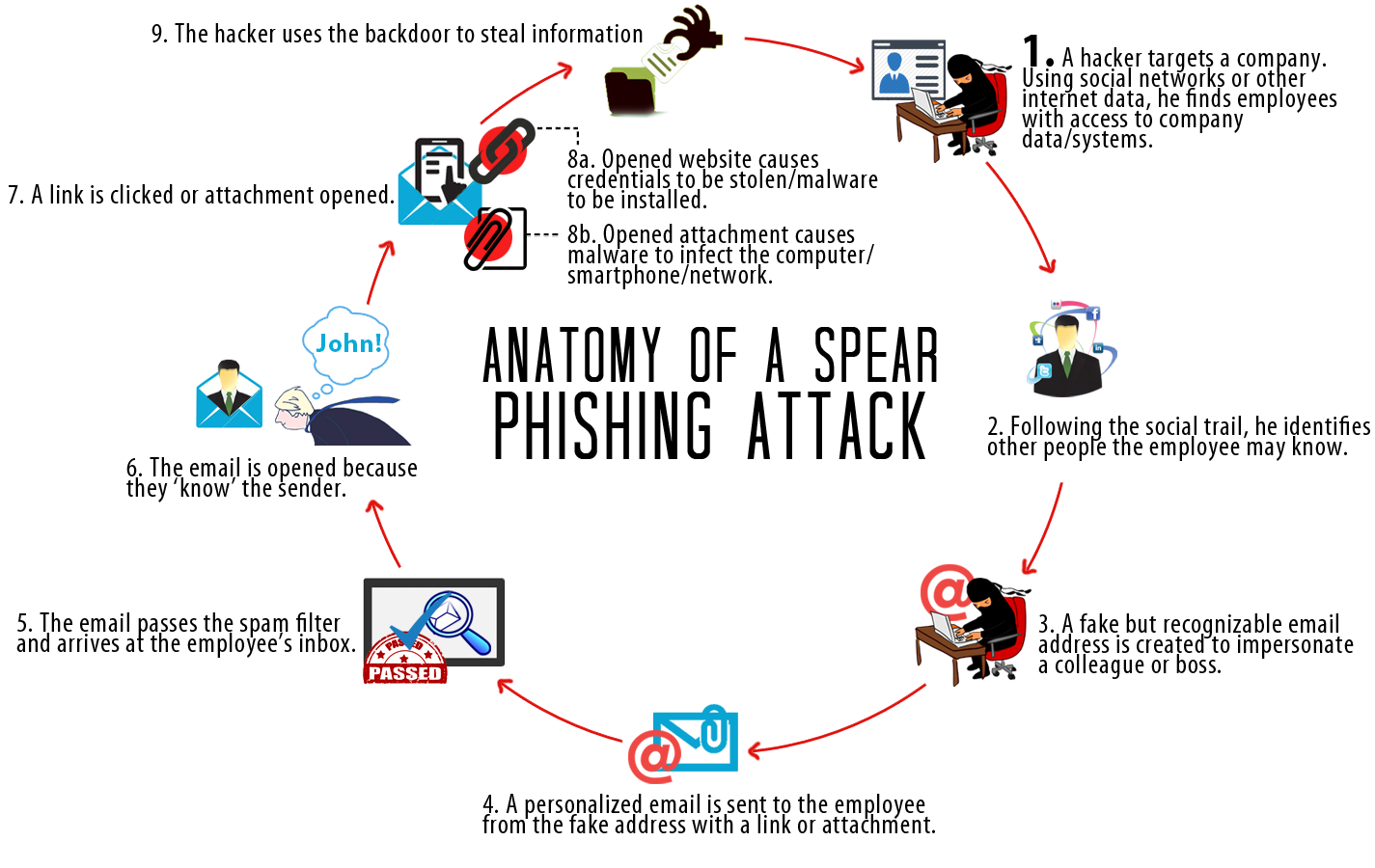
Ransomware is bad for business, but has not caused any deaths.
[A] What is True?
[B] What is False?
[B] What is False?
The patient, identified only as a woman who needed urgent medical care, died after being re-routed to a hospital [in Sept 2020] in the city of Wuppertal, more than 30 km away from her initial intended destination, the Duesseldorf University Hospital.
The SolarWinds attack was attributed to be from this Nation-State's threat actors.
[A] Who are N. Korean threat actors?
[B] Who are Iranian threat actors?
[C] Who are Russian threat actors?
[D] Who are Chinese threat actors?
[C] Who are Russian threat actors?
https://www.csoonline.com/article/3613571/the-solarwinds-hack-timeline-who-knew-what-and-when.html
Of the two, this is most important for stronger passwords.
[A] What is length?
[B] What is complexity?
A phishing attempt using text messages in order to get you to click on malicious links and/or share personal data.
[A] What is spamming?
[B] What is smishing?
[C] What is vishing?
[D] What are bots?
[B] What is smishing? (SMS phishing)

The best practice for where to store backups in order to recover more quickly without losing data from ransomware.
[A] What are external Hard Drives?
[B] What is offline storage?
[C] What is save to Hard Drives?
He was hacked by the Crown Prince of Saudi Arabia via a WhatsApp message.
[A] Donald Trump
[B] Barack Obama
[C] Jeff Bezos
[D] Elon Musk
This is the strongest password of these options:
[A] What is "Monkeymonkeymonkey" ?
[B] What is "m0nkey!" ?
[C] What is "IamAmonkey?" ?
[D] What is "Monkeymonkeymonkey?" ?
[C] What is "IamAmonkey?" ? 4.22mins
*Times are 'time to crack' estimates.
https://www.my1login.com/resources/password-strength-test/
What is "Monkeymonkeymonkey" ? .17secs
"m0nkey!" ? .01sec
"Monkeymonkeymonkey?" ? 14.69secs
A sophisticated, sustained cyberattack in which an intruder establishes an undetected presence in a network in order to steal sensitive data over a prolonged period of time. [It] is carefully planned and designed to infiltrate a specific organization, evade existing security measures and fly under the radar.
[A] What is Spyware?
[B] What is GDP?
[C] What is Whaling?
[D] What is APT?
[D] What is APT? (Advanced Persistent Threat)
https://www.crowdstrike.com/cybersecurity-101/advanced-persistent-threat-apt/
The goals of APTs fall into four general categories:
- Cyber Espionage, including theft of intellectual property or state secrets
- eCrime for financial gain
- Hacktivism
- Destruction
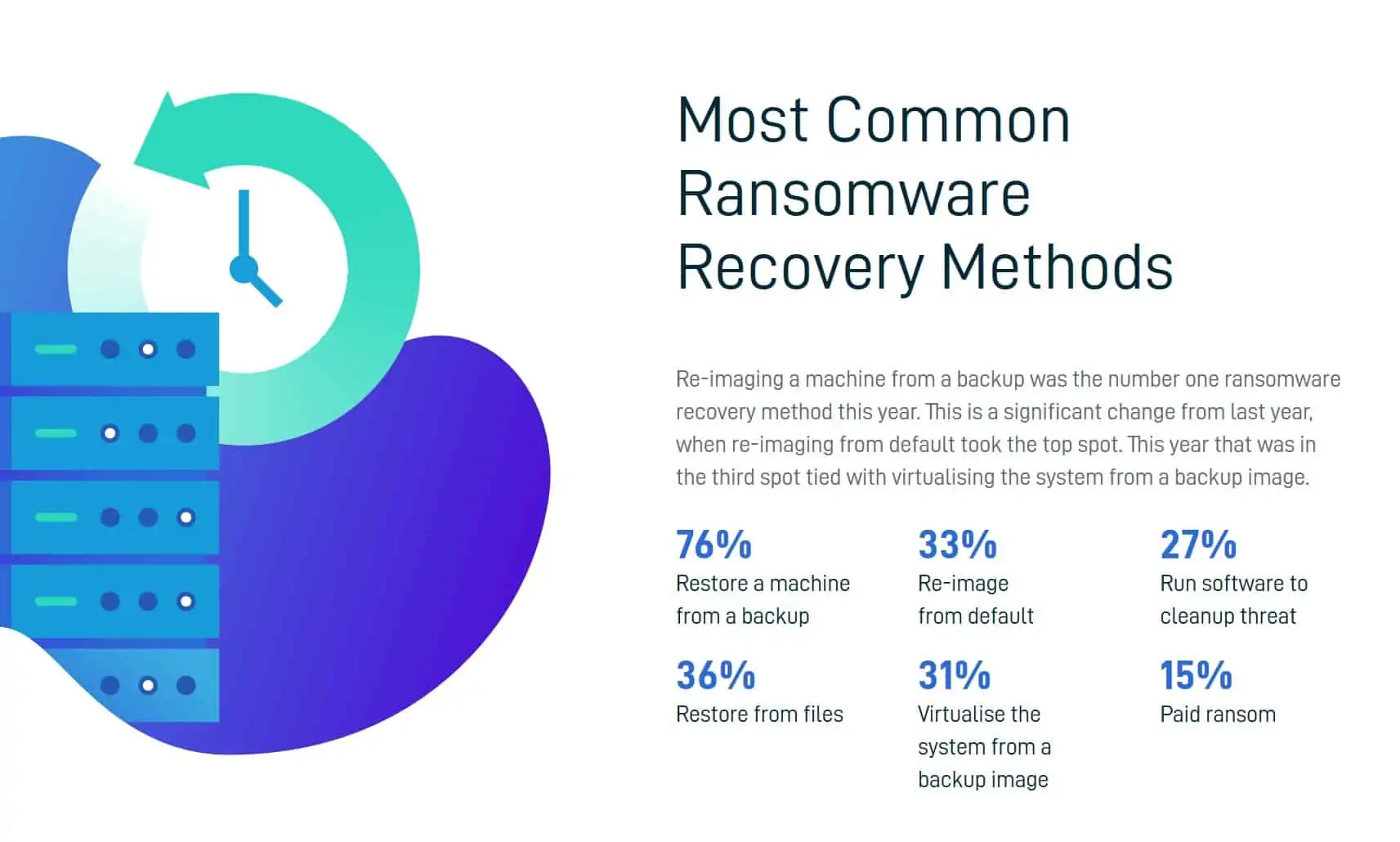
The most common recovery method for ransomware in the last year.
[A] What is restore from files?
[B] What is virtualize the system from a backup image?
[C] What is restore a machine from a backup?
[D] What is paid the ransom?
[C] What is restore a machine from a backup?
https://www.comparitech.com/antivirus/ransomware-statistics/
This was how ransomware got into the Colonial Pipeline's network.
[A] What is a Virtual Private Network?
[B] Who is a contractor working for a nation-state?
[C] What is an unpatched system?
[D] What is an email attachment?
[A] What is a Virtual Private Network?
[T]he company believes that the criminal hackers infiltrated Colonial’s computers through an old virtual private network, commonly known as a V.P.N., “that was not intended to be in use.” He added, “We are still trying to determine how the attackers gained the needed credentials to exploit it.”
https://www.nytimes.com/2021/06/08/business/colonial-pipeline-hack.html