Information about an individual, such as social security number, age, race, phone number(s), medical information, financial information, and biometric data such as fingerprint records and retina scans.
personally identifiable information (PII)
An example of public key encryption developed by Rivest, Shamir, and Adelman, the founders of __________ an American computer and network security company.
RSA Encryption
The process of encoding data to prevent unauthorized access, such as converting plaintext to ciphertext.

encryption
WHat am I? 
great white shark
A message appears in a browser window saying that the system is infected by malware. A link is provided to help install software to remove the malware.
Which course of action would be the most reasonable?
A. Click on the link. If the software offered is free, then it is safe to install.
B. Stop using the computer. Wipe the hard drive and reimage the computer.
C. Do not click on the link. Close the browser and run a trusted antivirus scan.
D. Stop using the browser. It is probably an unsafe browser and is now corrupt.
C. Do not click on the link. Close the browser and run a trusted antivirus scan.
The unauthorized access or retrieval of confidential or otherwise protected data.

data breach
A business or organization that issues a digital certificate verifying that a given public key is owned by the entity named on the certificate. Also the initials for the Golden State.
Certificate authority (CA)
A cipher in which each letter in an alphabet is replaced with a different character or symbol. Aka"Caesar cipher"
substitution cipher
what am i? ?

mako shark
Ali sends Barb a message using Barb's public key and no other encryption.
Which of the following is most likely to be accomplished
A third party with supercomputers will be unable to read Ali's message to Barb
Barb can reply to Ali using the same keys, and only Ali will be able to read the reply
If Ali sends the message publicly, most people other than Barb will be unable to read it
Barb can have greater confidence that it was Ali that sent the message and not an imposter
3. Ali sends the message publicly, most people other than Barb will be unable to read it
Small text-based bits of information about your browser that a web server saves.

cookies
Confirm your identity using knowledge known only to you or information interpreted by you
authenticate
A method for determining a solution to a problem by sequentially testing all possible solutions.

brute force
Popular show on Discovery channel about crab fishermen in the Bering Sea

Deadliest Catch
You are going on a trip to Japan in the next few months. You decide to check current airfare rates on a particular travel website without signing in. Two days later you decide to revisit the same site to purchase your tickets. Upon loading the page you see an advertisement for a tourist attraction in Japan.
Which of the following is LEAST likely to explain the targeted advertising?
A. The site accessed your browsing history in your web browser
B. The site accessed information about your last visit from a cookie
C. An advertiser has tracked you and identified you as a user interested in Japan
D. The site accessed information about your last visit from data on the web server
A. The site accessed your browsing history in your web browser
Practice of sending fraudulent emails that appear to be from legitimate companies with the intent to induce people to share sensitive information, such as passwords and credit card numbers.

phishing
A digital document used to verify the authenticity of a server or public key.

SSL certificate
The process of decoding the data, the reverse of the encryption process, making the data human-readable again.

decryption
This fish has an estimated lifespan of 250 years and possibly 500 years.

Greenland shark
Which of the following is not an important aspect of paired-key encryption?
The sender and receiver share keys to decrypt information
The public key has code to decrypt information from the sender
The public key has symmetric information for the sender and receiver
The sender and receiver must trust each other with the key they are sharing
3. The public key has symmetric information for the sender and receiver
Software intended to damage a computing system or to take partial control over its operation.

malware
decrypt this message: gj hfwjkzq zxnsl hmfy luy
be careful using chat gpt
Besides brute force, substitution ciphers can also be solved using this technique.
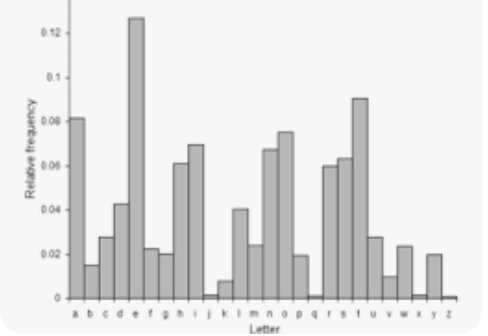
letter frequency
What fish is the primary source of caviar?

sturgeon
A message appears in a browser window saying that the system is infected by malware. A link is provided to help install software to remove the malware.
Which course of action would be the most reasonable?
Click on the link. If the software offered is free, then it is safe to install.
Stop using the computer. Wipe the hard drive and reimage the computer.
Do not click on the link. Close the browser and run a trusted antivirus scan.
Stop using the browser. It is probably an unsafe browser and is now corrupt.
3. Do not click on the link. Close the browser and run a trusted antivirus scan.
The use of a program to record every keystroke made by a computer user in order to gain fraudulent access to passwords and other confidential information.

keylogger
using my private key of 6037 and modulus of 20567, decrypt the message on schoology
"SSL certificate"
substitution ciphers are examples of __________ encryption, where the sender and receiver share a public key.
symmetric
A wireless access point that gives unauthorized access to secure networks.

rogue access point
Also called public-key encryption, an encryption method that uses two keys, a public key and a private key, belonging to one owner.
Asymmetric encryption