Confidentiality
_____________
Availability
What is INTEGRITY?
What is a WEAK PASSWORD?
Viruses and worms are of this type of malware.
What is CIRCULATION?
This is abbreviated HTML.
What is HYPERTEXT MARKUP LANGUAGE?
This is abbreviated POP.
What is POST OFFICE PROTOCOL?
A flaw or weakness that allows a threat agent to bypass security.
What is a VULNERABILITY?
Trying every possible combination of letters, numbers and special characters to create candidate digests.
What is a BRUTE FORCE ATTACK?
Captures and stores each keystroke
What is a KEYLOGGER?
Two different protocols for receiving incoming emails.
What is POP3 and IMAP4?
What is a SCRIPT KIDDIE?
Authentication
Authorization
________________
What is ACCOUNTING?
Targetting the "big fish"
What is WHALING?
Software that is a cumulative package of all patches & feature updates.
What is a SERVICE PACK?
Another term for "poisoned ad attack"
What is MALVERTISING?
Highly skilled with enough gov't resources to breach almost any security defense. Considered the most deadly attacker.
What is a STATE-SPONSORED ATTACKER?
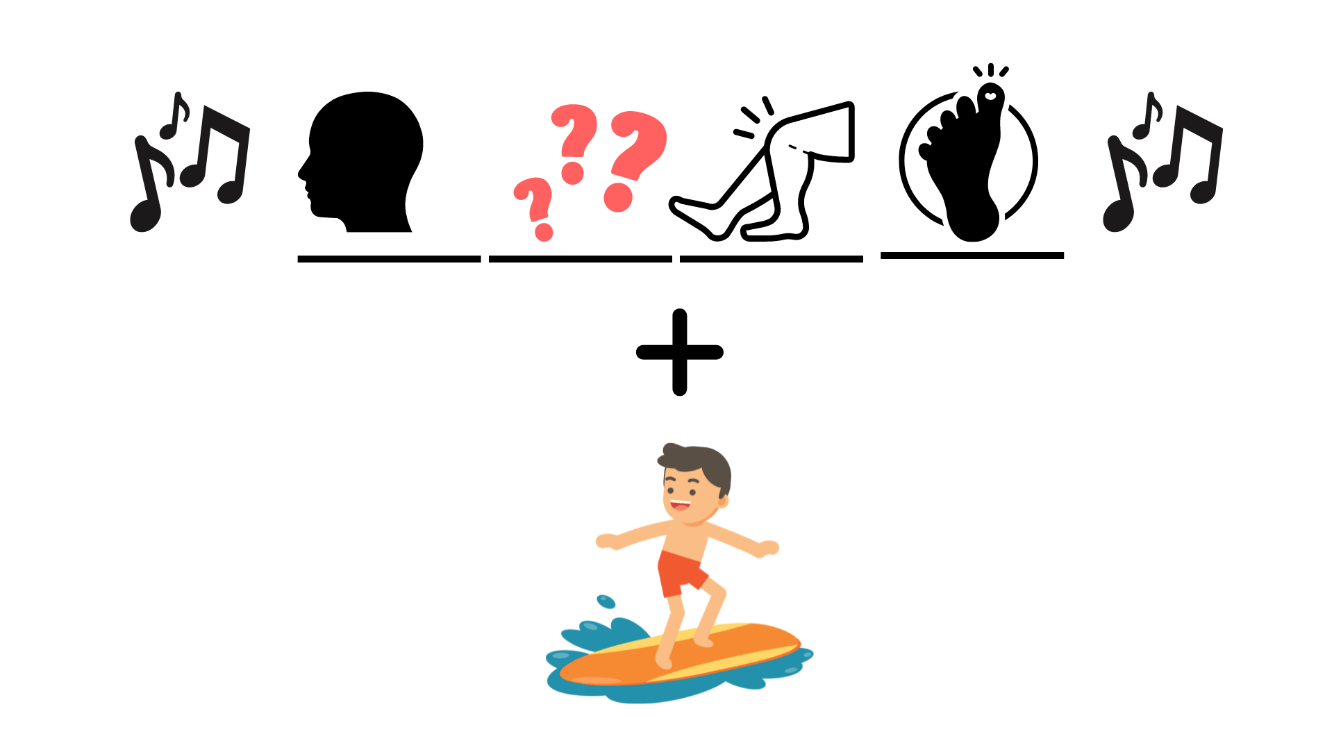
What is SHOULDER SURFING?
Highest level of a user account for the most control over a computer
What is an ADMINISTRATOR ACCOUNT?
A list of senders from whom the user dos not want to receive any email.
What is BLACKLIST?
The controller of hundreds or thousands of zombie computers.
What is a BOT HERDER?
A law enacted to fight corporate fraud and corruption.
What is SARBOX?
(Sarbanes-Oxley Act)
A false warning intended to track a user into performing an action that will compromise security
What is a HOAX?
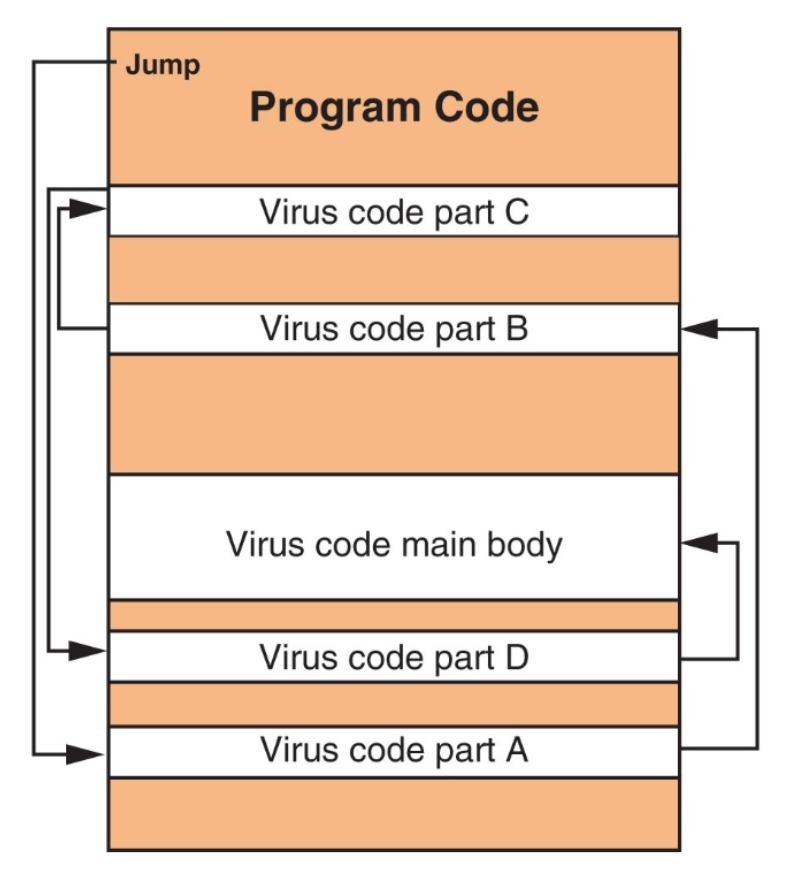
What is a SPLIT INFECTION?
Larger than a cookie - a Flash cookie.
What is an LSO?
(Locally shared object)
This mode is when the entire screen is temporarily dimmed & a UAC dialog box appears.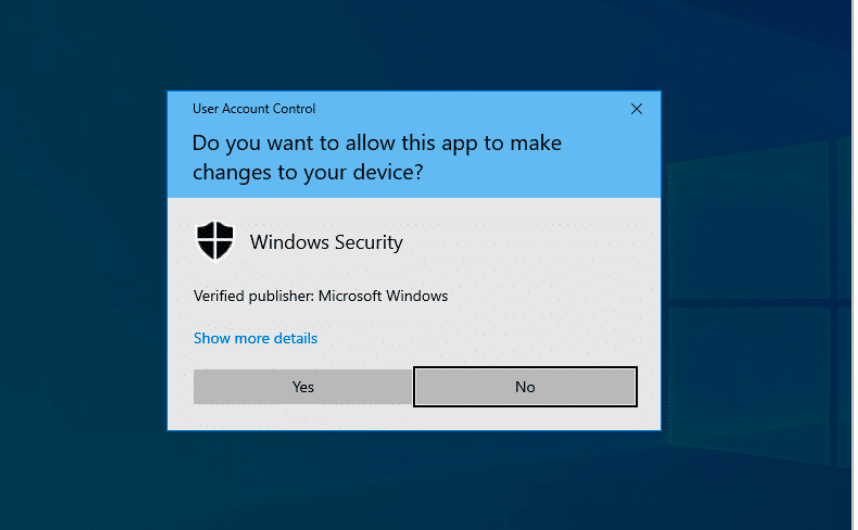
What is SECURE DESKTOP MODE?