1010 (base 2) expressed as a base 10 value would be:
What is 10?
Which protocol is responsible for making sure every computer has an address?
What is Internet Protocol (IP)?
A linear search has this runtime.
What is linear?
Consider the following pseudocode:
a = 5
b = 3
c = a
a = 7
b = a + c
The values of a, b, and c after the program is run would be:
What are
a = 7; b = 12; c = 5
You receive a text stating that your Netflix account will be shut down unless you click the link and provide some information. This is likely...
What is a phishing attack?
This many bits would be needed to represent 32 unique values.
What is 5 bits?
What would be the fewest connections that would need to be cut before computer A could no longer communicate with computer D?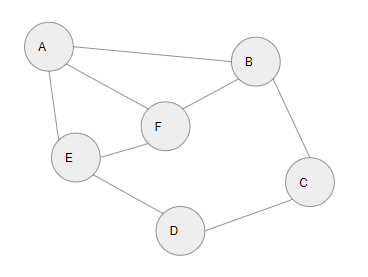
What is 2?
It would take this many comparisons to find the number 22 in this list using a linear search.
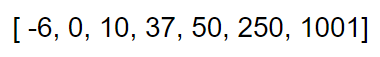
What is 7?
The result of the following:
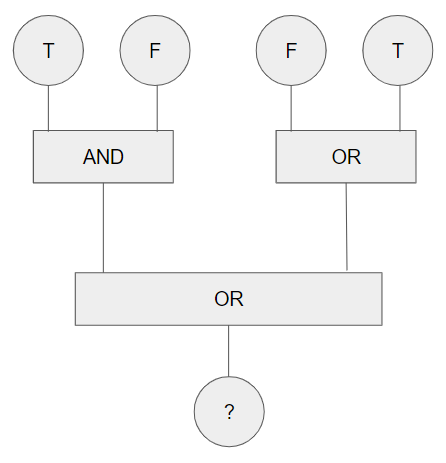
What is True (T)?
A person does not have access to the internet because of a physical disability. This situation contributes to...
What is the digital divide?
In ASCII, the '%' character is represented with the base 10 number 37. How is this character represented using binary?
What is 100101?
This protocol is responsible for making sure all packets successfully make it to their location and are in the correct order.
What is Transmission Control Protocol TCP?
It would take this many comparisons to find the value 50 using a binary search?
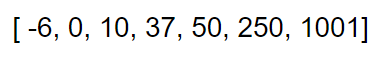
What is 3?
This is the total number of values that would be printed to the console.
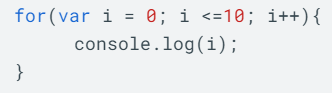
What is 11?
The lock in the left corner of your address bar informs you that your page is using this type of encryption.
What is Asymmetric Encryption?
Attempting to store 100 using 4 bits will result in this.
What is an overflow error?
This protocol is responsible for handling the get requests so that a user can request all the files necessary for viewing a web page.
What is Hypertext Transfer Protocol (HTTP)?
A computer on its own takes 30 seconds to complete a task. Four computers working in parallel can complete the same task in 10 seconds. What is the speedup time?
What is 3?
Consider the following function:
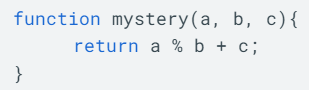 This value would be returned by the call:
This value would be returned by the call:
mystery(1, 2, 3)
What is 4?
You enter your username and password to access your bank account. A text is then sent to your cell phone with a code that must be entered before you are able to view your account. This situation is an example of what?
What is multi-factor authentication?
Anita took a video of her cat doing backflips and wants to text the video to her friend. Anita knows her friend is usually out hiking in places where the cell coverage is spotty. Anita decides to make the file as small as possible so that it doesn't take forever for her friend to download.
The type of compression Anita will be using is most likely this...
What is lossy compression?
An airline provides a premium 5g internet connection for those willing to pay a $25.00 fee. Those not willing to pay the fee will be able to use a free internet connection that offers less bandwidth. What would the person using the free internet connection likely experience?
The circles in the image represent places on a map that you would like to visit. Your goal is to find the most efficient way to begin at the location marked "Start" and visit each place without visiting the same place twice. If you used an algorithm, this would be the runtime.
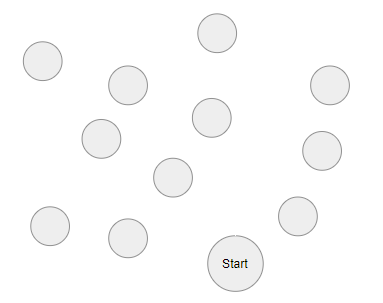
What is exponential?
Consider the following code and function call:
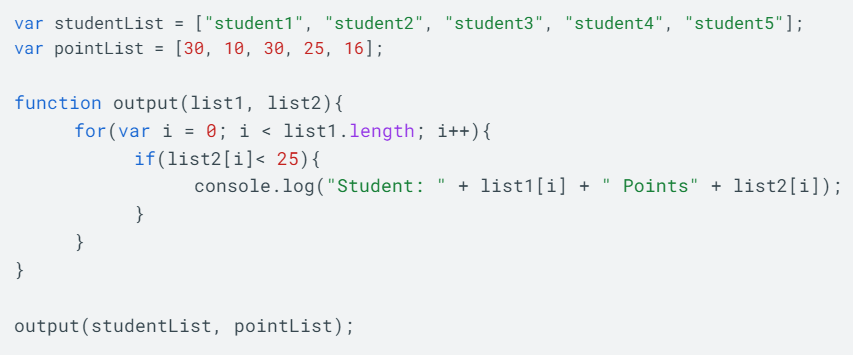
This will be the output:
What is
Student: student2 points10
Student: student5 points16
You entered http://www.amazon.com in your web browser, but are instead taken to an unknown site that sort of looks like http://www.amazon.com, but is asking you to enter your social security number.
Uh oh, this might be at play...
What is DNS spoofing?