This 4 letter acronym is used as a shorthand for our very own cyber security team in Australia
What is the ASCS (Australian Cyber Security Centre)?
This network type connects computers and other devices in a small geographical area, such as a home or school
What is a LAN?
This type of threat is made from The Bad Guys(tm).
What is a Deliberate threat?
This Victorian law caters specifically for Victorian government agencies and contains 10 Information Privacy Principles (IPPs)
What is the Privacy and Data Protection Act 2014 (Vic)?
I want to show how my code works, but so a non-nerd can (almost) understand it. This type of code is perfect for that.
What is pseudocode?
This core strategy from the Essential Eight involves applying updates to software to fix known vulnerabilities
Patch Applications
The network hardware that connects wired devices to each other on a single LAN.
What is a Switch?
This component of the CIA triad refers to ensuring that only authorised individuals can access data
What is Confidentiality?
Failing to comply with privacy legislation and guidelines can lead to fines, lawsuits, and this type of widespread public consequence.
(Please don't leave any bad google reviews...)
What is Reputational Damage.
This digital system feature refers to the specific benefit the system delivers, such as providing a quick, easy, and secure item checkout.
(If it doesn't help someone; why make it?)
What is a Capabality?
This is the Essential Eight strategy related to copying and securely storing data to guard against possible data loss
What are Regular Backups?
This small, private network connects personal devices like wearables and smartphones in a very small geographical area using technologies like Wi-Fi and Bluetooth.
What is a WPAN?
This type of attack is used to flood a network from either a single device or a whole network of them, shutting down the service, giving by a 3 (or 4) letter acroym.
What is a DoS (or DDoS) attack?
[Distributed Denial of Service]
This specific APP (number!) dictates that collected information should only be used and disclosed for the purpose stated when it was originally gathered.
(I wont share your survey data with ad makers, I promise...)
What is APP6
This functional design tool identifies the data to be used including variable name, type, scope and description.
Nope, not a thesaurus!
What is a Data Dictionary
The ISM networking guidelines recommend limiting this physical characteristic of wireless signals to reduce network exposure
What is a Wireless Footprint?
The technology that allows off-site personnel to access a remote network securely by creating a private tunnel using strong encryption keys
(This question is sponsored by....)
What is a VPN?
This type of encryption uses the same key for both encrypting the plain-text and decrypting the cipher-text
What is Symmetric encryption?
This is automatically owned by the person who created it under the Copyright Act 1968 (Cth), covering literary, dramatic, musical, and artistic works.
(Yes, even your own solutions you just developed!)
What is Intellectual Property (IP)?
This ideation tool is used to understand a users perspective and how they feel.
No, you don't need to be an empath to use it!
What is empathy mapping?
This ISM strategy ensures that networks are divided into smaller sections to limit access and contain the effects of a breach.
(Please quarantine the infected away from my network!)
What is Segmentation & Segregation?
This piece of network hardware acts as a translator, converting data signals into light impulses, analogue sound waves, or radio waves depending on the connection type.
What is a Modem?
This three letter acronym is a type of system that monitors all network traffic to detect intrusions and then alerts relevant parties, but does not actively stop the threat.
What is an IDS (Intrusion Detection System)
This core principle is covered in:
- The Privacy Act (1988) - APP11
- The Health Records Act (2001) - IPP4
- The Privacy & Data Protection Act (2014) - HPP4
Can the data be breached in any way?
What is Data Security?
(Or any synonym relating to securing data from breach, loss, damage and/or access)
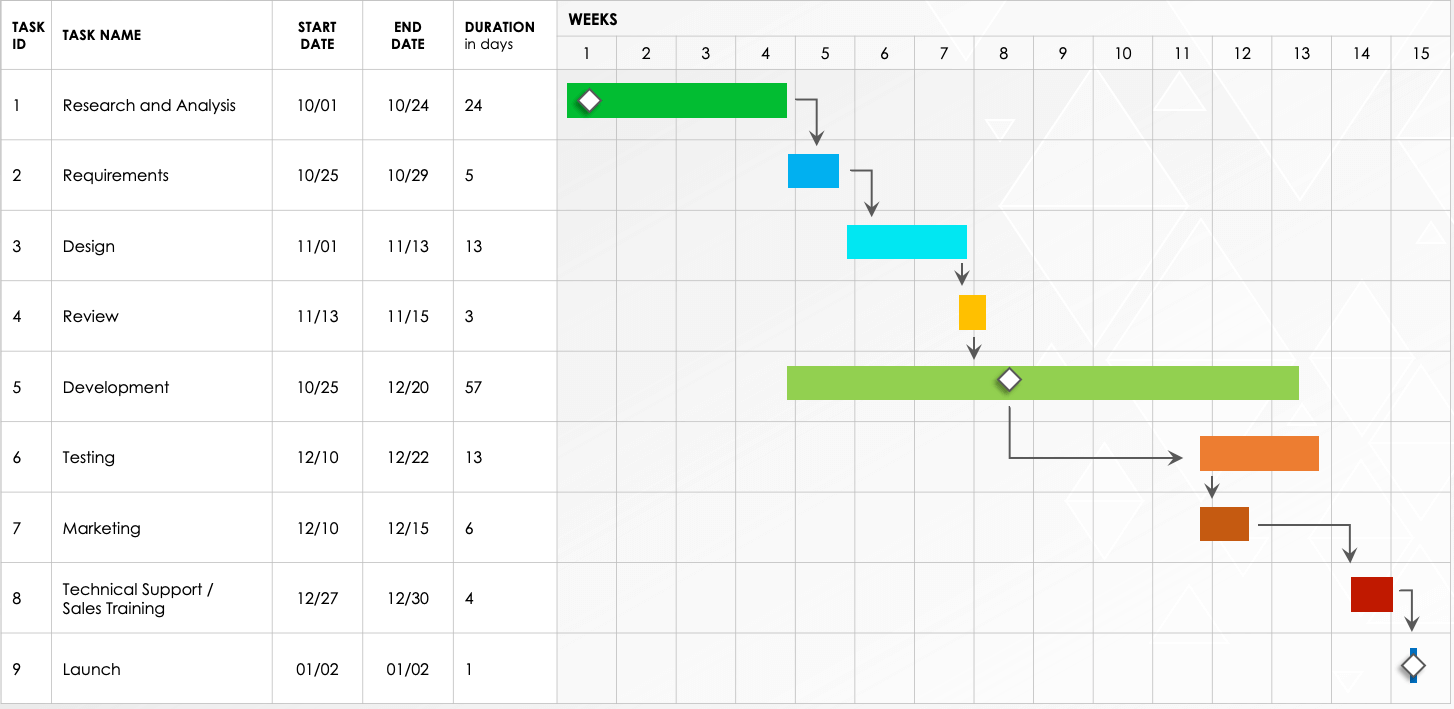
Within a Gantt chart order is important;
This term is used to describe the relationships the arrows given between tasks.
What is a dependency?