This category of risk occurs when user input is included directly in a query or command to an interpreter without proper validation or escaping.
What is injection?
NOT FOUND plus OK
What is 604?
404 + 200
Without this control, attackers can send thousands of requests per second and overwhelm an API.
What is rate limiting?
At least one thing is wrong with this GUI Tony Stark uses to hack government systems.
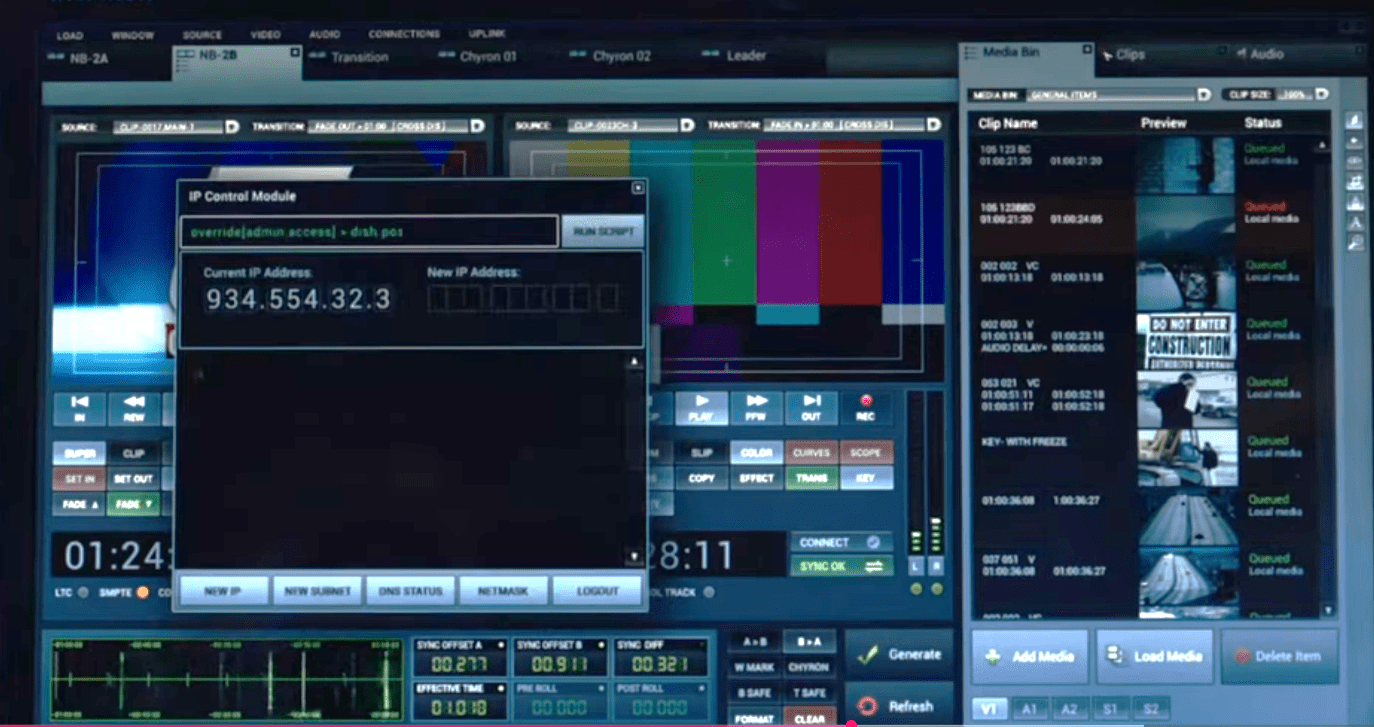
What is the an invalid IP address?
Honestly, there are probably a lot.
Its not DNS
There is no way its DNS
_______
What is "It was DNS"
The function of the `git init` command
What is set up a new tracked repository?
To reduce risk from OWASP #6: Vulnerable and Outdated Components, OWASP recommends using this three letter acronym to identify the open source software is included in your codebase.
What is a Software Composition Analysis (SCA) tool?
BAD GATEWAY minus FORBIDDEN
What is 99?
502 - 403
A security tool that is deployed in front of your APIs that can improve authentication, filter input, and add logging.
What is an API gateway?
In this 90s sci-fi blockbuster, Jeff Goldblum saves humanity by uploading a computer virus to an alien mothership using a laptop which apparently uses alien-compliant drivers and protocols.
What is Independence Day?

There once was a man from Nantucket
Who had a allow *:* policy on his S3 ____
What is bucket
What is git checkout -- <file>?
How do you pronounce this word
"SIEM"
Audience cheer if this is correct?
BAD REQUEST divided by OK
What is 2?
400 / 200
This common standard lets APIs and applications act on behalf of a user without ever seeing their password, often using tokens with scopes.
What is OAuth?
In this scenario, a hacker cracks a government system in 60 seconds while dubstep plays, bouncing between multiple monitors and GUI hacking tools that look more like WinAmp skins than terminals.
What is any Hollywood hacking montage ever?
They sent all the logins in plain text,
A packet sniffer knew what came next;
They skipped over certs and encryption finesse—
They should have used ____.
What is TLS/HTTPS?
Some teams stop developers from committing code with secrets or missing tests by running these custom checks before Git accepts the commit.
What is a pre-commit hook?
If your app lets users hand it a URL and it says “Sure, I’ll grab that for you!”—you’ve probably built this OWASP #10 vulnerability.
What is Server-Side Request Forgery (SSRF)?
REQUEST TIMEOUT divided by 4
What is 102?
408 / 4
This advanced authentication mechanism requires both the client and the web server to have valid and accepted TLS certificates for a connection to be valid.
What is mutual TLS (mTLS)?
In this 90s spy thriller, a Russian hacker in an arctic bunker knows he has been detected by the FBI when giant yellow lights flash on his screen. He then hacks back against those tracking him by sending them a "spike" attack which allows him to send snarky messages to the FBI.
What is Golden Eye?

The sticker on the router’s back,
Spelled “admin / admin” right on the rack;
They skipped MFA and other essentials—
What doomed the box?: ____ ____.
What is default credentials?
When you check out a specific commit instead of a branch, you end up here — changes aren’t attached to any branch until you create one.
What is a detached HEAD?
To stop cross-site scripting, OWASP recommends setting this HTTP header which limits the resources a browser is able to load for a given page.
What is Content-Security-Policy (CSP)?
I’m a teapot
What is 418?
The HTTP 418 I'm a teapot status response code indicates that the server refuses to brew coffee because it is, permanently, a teapot.
By flooding an API with requests, an attacker can rack up cloud bills or burn CPU cycles in this costly attack.
What are unbounded consumption or denial of wallet attacks?
According to the TV show NCIS, you hack twice as fast through the use of this advanced hacking technique.
What is having two hackers on the same keyboard at the same time?
DOUBLE JEOPARDY!
PASSWORD PURGATORY
Enter the following password:
P@ssw0rd_Purg@t0ry_2024!@#$%^&*()_+{}|:</`~
Use this command to find the branch that you accidentally deleted. Then flog yourself again as punishment.
What is git reflog?
