What does tracert do?
Tracert: displays the route of packets and timing between point A and point B.
What does the cat command do?
The cat (short for “concatenate“) command is one of the most frequently used commands in Linux/Unix-like operating systems. cat command allows us to create single or multiple files, view content of a file, concatenate files and redirect output in terminal or files.
What does ipconfig do?
Ipconfig is used to view the current configuration of IP interfaces at the command line.
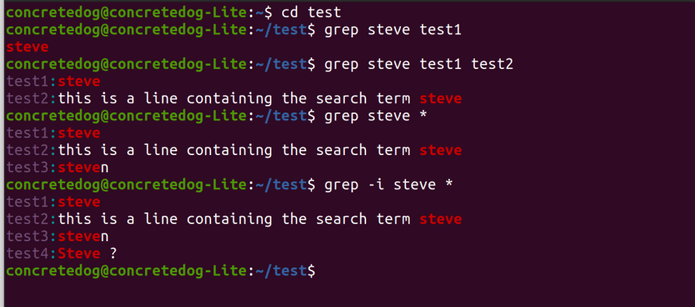
What is the grep command in Linux used for?
The grep command syntax is simply grep followed by any arguments, then the string we wish to search for and then finally the location in which to search.
What is nmap used for?
Nmap is a port scanner that tells what port are open on your device. It also allows you to scan your network and discover not only everything connected to it, but also a wide variety of information about what's connected, what services each host is operating, and so on.
What are the two types of RBAC?
What is Role Based Access Control, what you do or what group you are part of People have roles.
What is Rule Based Access Control this is part of an ACL and firewalls always think Rules are objects
What does nslookup do?
Nsloohup used to search the Domain Name System (DNS) to determine the mapping of domain names to IP addresses.
What does the route command do?
The route command allows modification of the IP routing table. It is primarily used to set static routes for traffic to be sent to specific networks or hosts.
What does pathping do?
Path ping combines ping and tracert in one command and it helps you to find the location of a packet loss in a route between you and a host
What is Wireshark used for?
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues.
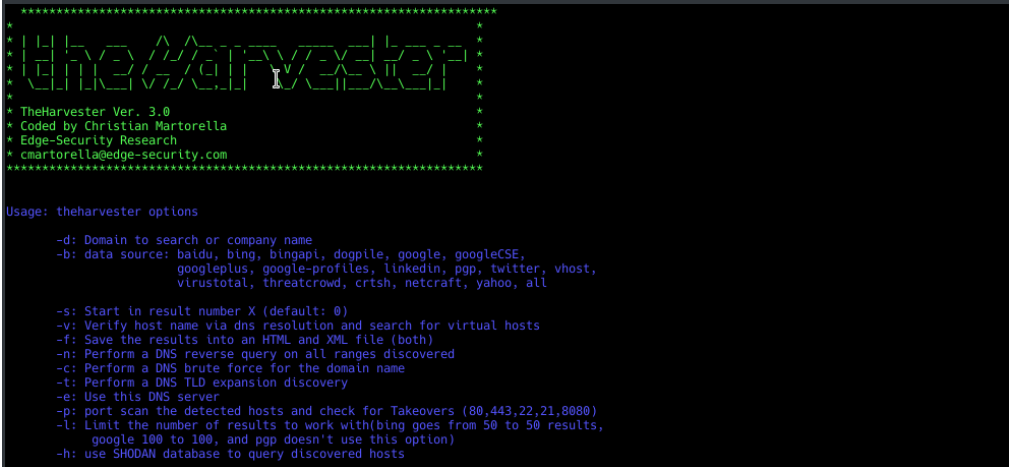
The Harvester is used for what?
TheHarvester is an open source python program used to gather OSiNT.
What are the two types of MAC?
What is Mandatory Access Control set by the system
What is Media Access Control (Itme ID)
What command is used for ICMP? What does it do this show you?
What is ping, this shows if a a device is connected and if if is able to be discovered.
What does ifconfig do?
ifconfig is used to view the current configuration of IP interfaces at the command line; ifconfig also permits the enabling and disabling of interfaces.
What does the arp command do?
Apr allows you to display the IP-address-to-MAC-address mappings that a system has built so that it doesn't have to fetch the same information repeatedly for systems it communicates with.
What does the Linux command chmod do?
chmod changes directory permissions in Linux, use the following: chmod +rwx filename to add permissions. chmod -rwx directoryname to remove permissions.
Nessus is used for what?

Nessus is a vulnerability scanner. Nessus can scan a wide variety of operating systems and applications, including all flavors of Windows, macOS, and most Linux distributions. Nessus reports provide information on missing patches and updates, configuration issues, and so on. It can break those down into OS, network segment, vulnerability severity, and many other categories.
What is DAC?
What is Discretionary Access Control this is set by the owner of the data
What does netstat do?
Netstat displays active TCP connections. There are various Switches that can be used with the netstat command to display different types of networking related data. For example the switch –a lists all of the TCP/IP connections and listening ports.
What does traceroute do?

In Linux traceroute displays the route of packets and timing between point A and point B.
What is the curl command used for?
Curl allows you to transfer data from a server using various protocols HTTP, HTTPS, FTP, ect...
What is a rainbow table attack?
A rainbow table attack is a password cracking method that uses a special table (a “rainbow table”) to crack the password hashes in a database. It includes symbols as substitutes ie @ = a
What does Cuckoo do?
Cuckoo is a Linux based sandbox environment tool.
What is IaaS?
What is Infrastructure as a service this is hardware only
What is SSH used for?
SSH enables a user to log in to a remote machine and execute commands as if they were on the console of that system. SSH is a secure replacement for the older Telnet, which is insecure because its data isn’t encrypted when communicated. SSH provides a secure, encrypted tunnel to access another system remotely.
what does dig do?
Dig is used to search the Domain Name System (DNS) to determine the mapping of domain names to IP addresses.
Pizza Pizza is the trade mark of which company?
What is Little Cesar's

Who is this this and did his voice originally?

Who is Buzz Lightyear, and Tim Allen
What is the dd tool used for?
dd is a command-line utility for Unix and Unix-like operating systems whose primary purpose is to convert and copy files.
What is PaaS?
What is Platform as a service this is where hardware and OS are set for you