What is 100010001 in decimal?
what is 273?
How are messages sent over the internet?
what are packets?
DNS
Domain name system
What is one example of a multi layer authentication?
A common example of multi-layer authentication would be a login page requiring a username (knowledge factor), password (knowledge factor), and security question (knowledge factor).
teachers discretion
how many connections would have to be broken for RAJ to no longer communicate with MP?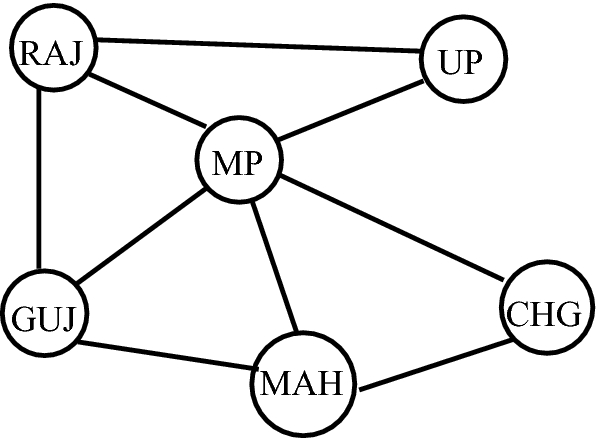
what is 3?
What can binary be used to represent?
a. strings
b. numbers
c. on and off
d. all of the above
what is D?
The world is currently in a transition to using IPv6, a newer version of the IP protocol that uses 128-bit addresses instead of 32-bit addresses used by IPv4. What is the main problem that IPv6 was created to solve?
IPv6 will allow problems with IPv4's address hierarchy to be resolved
32-bit addresses could not ensure that every internet-connected device can receive a unique IP address
32-bit addresses could not accommodate the increased size and amount of data traveling on the Internet as it has grown in popularity
IPv4 proved unreliable in some cases where network redundancy could not be ensured
what is 32-bit addresses could not ensure that every internet-connected device can
HTTP
hyper text transfer protocol
Is this phishing?
if not what is it?
Using software to keep track of key movements
No, key logging
T or F?
Once a program has been written and tested, it almost never needs to be modified
false
what is 38 in binary
100110
According to the domain name system (DNS), which of the following is a subdomain of the domain code.org?
what is educate.code.org
TLS
Transport Layer Security
What is the purpose and meaning of DDoS?
Distributed Denial of Service
involves multiple connected online devices, collectively known as a botnet, which are used to overwhelm a target website with fake traffic
Describes a limitation of using a computer simulation to model a real-world object or system
Computer simulations usually make some simplifying assumptions about the real-world object or system being modeled.
list these in order
10101010
010101010101
011001100110
00110011
00110011, 010101010101, 011001100110, 10101010
What does WWW stand for, and what is it?
World Wide Web
An Internet application that is based on the HTTP protocol. It is a collection of webpages found in the internet
SSL
secure sockets layer
Which of the following data connectivity options is the best to use when both availability and reliability is required?
WiFi
Bluetooth
Cellular
Wired
D
The process of ignoring details in order to better concentrate on problem solving
what is abstraction?
what is the main function of Binary code?
to allow computers to represent and store data
who created the internet?
A. Steve Jobs
B. Satya Nadella
C. Vint Cerf
D. Jack Ma
IPV4
Internet Protocol version 4
Which of the following describes the difference between open source and commercial operating systems?
A- Open source OSs only run on desktop computers, whereas commercial OSs run on servers.
B- Open source OSs only run on on standard and non-standard hardware, whereas commercial OSs run on specifically designed hardware.
C- Open source OSs can be downloads and used by everyone, whereas commercial OSs can only be used by companies
D- Open source OSs are usually provided free of charge, whereas commercial OSs usually require some cost to use.
D
When will hair type be wavy?
IF (fatherAllele = "C" AND motherAllele = "C")
{
hairType ← "curly"
}
ELSE {
IF (fatherAllele = "s" AND motherAllele = "s")
{
hairType ← "straight"
}
ELSE
{
hairType ← "wavy"
}
}When fatherAllele is "s" and motherAllele is "C"
OR
When fatherAllele is "C" and motherAllele is "s"