It's the K in an ELK stack.
What is Kibana
Wireshark will not warn you when someone does strange things on your network that he/she isn’t allowed to do. You will need this type of detection system on your network.
What is a Intrusion Detection System (IDS)
By default, this should be blocked on your network.
What is all traffic.
To verify the Snort version, you must type this on the command line and hit Enter.
What is, type in snort -V and hit Enter.
This is what it mean to convert data into some unreadable form.
What is
Encryption
Techniques used in Penetration testing include these four "Exercise Type" Teams
What are Red, Blue, White and Purple Teams
It is the "L" in an ELK Stack
What is Logstash
A “packet” is a single message from any ____ protocol
A “packet” is a single message from any network protocol
A layer 4 firewall uses the following parameters for an access rule for protocols, which are:
Protocol of the traffic (TCP, ICMP, or UDP)
It's what the "t" means in the following string
sudo snort -T -i eth0 -c /etc/snort/snort.conf
What is "Test"
This ensures that the message was originated from the originator claimed in the message.
What is
Authentication
Configuration management, expounds upon the importance of security concepts in an enterprise environment with the following:
Diagrams
Baseline Configuration
Standard Naming Conventions
and this "Schema"
What is IP internet protocol
It is the "E" in and ELK Stack
What is Elastisearch
What are the 4 parts of a packet?
What are the 4 parts of a packet?
A layer 4 firewall uses the following parameters for an access rule:
- Source IP address (or range of IP addresses) and
- _______ IP address (or range of IP addresses)
A layer 4 firewall uses the following parameters for an access rule:
- Source IP address (or range of IP addresses)
- Destination IP address (or range of IP addresses)
It is the "A" in the following command string
sudo snort -A console -q -c /etc/snort/snort.conf -i eht0
What is print to standard output. "screen"
This means that Cryptography should ensure that the messages that are received by the receiver are not altered anywhere on the communication path.
What is
Integrity
In the vitualization and cloud computing concepts, the Cloud Models include:
IaaS
PaaS
SaaS
and XaaS which stands for this.
What is Anything as a Service
It's what ESM stands for
Enterprise Security Monitoring
What is a TCP ?
The transmission control protocol (TCP) is the internet standard ensuring the successful exchange of data packets between devices over a network.
Daily Double
Server management ports:
- Linux®SSH : Port ____
- Windows® RDP: Port ____
Server management ports:
- Linux®SSH : Port 22
- Windows® RDP: Port 3389
The arrow in the following screen capture indicates this
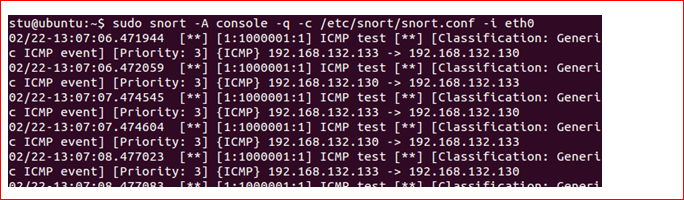
What is direction of flow
Daily Double
Digital signatures help to maintain this, if Alice sends a message to Bob but denies that she has actually sent the message.
What is
Non Repudiation
The visudo command allows you to make changes to this file
What is /etc/sudoers
It's how you say this word SQUIL
Sguil (pronounced sgweel or squeal)
Daily Double
What is UDP
User Datagram Protocol
The worst configuration for firewall would be to
Allow all traffic from any source on any port to any destination
Daily Double
This is how you would read the following log file
sudo ls /var/log/snort/192.168.x.x

You can see there’s a file there named after the protocol (TCP) and the port numbers involved in the activity.
We can read this file with a text editor or just use the cat command:
There are three types of cryptography techniques :
- Secret key Cryptography
- ______ key cryptography
- Hash Functions
There are three types of cryptography techniques :
- Secret key Cryptography
- Public key cryptography
- Hash Functions
Like The traceroute command, the tracecert command checks the connectivity of a device and displays this through the routers that the ICMP packet took.
WHat is the path