What is a HTTPS?
DOWARSSP
What is PASSWORD?
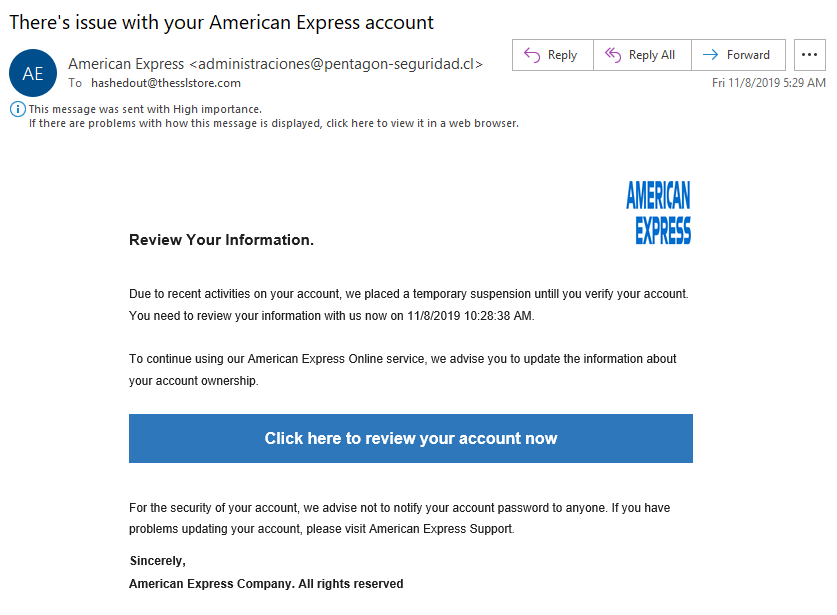
This is a phishing attempt!
A scam when an attacker sends a fake meeting invite containing:
Malicious links
Fake dial-in phone numbers
Fraudulent “document review”requests
What is Calendar Invite Scam?
Sharing your exact home address, phone number, or financial information on social media increases the risk of this type of crime.
What is IDENTITY THEFT?
If a website suddenly displays a pop-up claiming your computer is infected and urges you to call a phone number immediately, you're likely encountering this common online scam?
What is a tech support scam?
WAELRMA
What is MALWARE?
Real!
Malicious Links in Messages (Microsoft Teams)
Attackers send links via chat that lead to:
phishing login pages
malware downloads
credential harvesting sites
Because messages appear internal, users trust them more.
Chat Platform Scams
Cybercriminals often create fake profiles pretending to be friends or companies to trick people into revealing information. This tactic is called this.
What is SOCIAL ENGINEERING?
Attackers sometimes register websites with addresses like "paypal.com" or "amaz0on-login.com" to trick users who don't notice subtle spelling changes - a tactic known as this.
What is typosquatting?
NIOPRTYNCE
What is a ENCRYPTION?
Fraudsters who call pretending to be family members needing emergency holiday funds are using this emotional manipulation tactic.
What is the “family emergency” scam / impersonation scam?
A new technology and cyber threat that can write realistic phishing emails, clone voices and faces (deepfakes), and launch scams at massive scale
What is Artificial Intelligence?
Before accepting a friend request from someone you don’t know, cybersecurity experts recommend verifying their identity to avoid this type of fake account.
What is a BOT or IMPERSONATION ACCOUNT?
When using free public Wi-Fi at places like airports or coffee shops, security experts recommend using this tool to encrypt your internet traffic.
What is a VPN?
Please don't attempt to install 3rd party VPNs on company laptops (:
DTSRIIUBETNDDO
What is DISTRIBUTED DOS?
Many holiday-themed phishing emails use this type of urgent language strategy to pressure victims into acting quickly without thinking.
What is creating a sense of urgency?
A attack is where attackers repeatedly send login approval requests to a user’s phone.
What is MFA Fatigue Attack?
Reviewing and limiting who can see your posts, photos, and personal information is done through these settings.
What are PRIVACY SETTINGS?
Some malicious websites automatically attempt to install malware without requiring them to click anything - a threat known as this type of attack.
What is a drive-by download?
CTATOTNHUOFAWTRITNOAOEC
What is TWO FACTOR AUTHENTICATION?
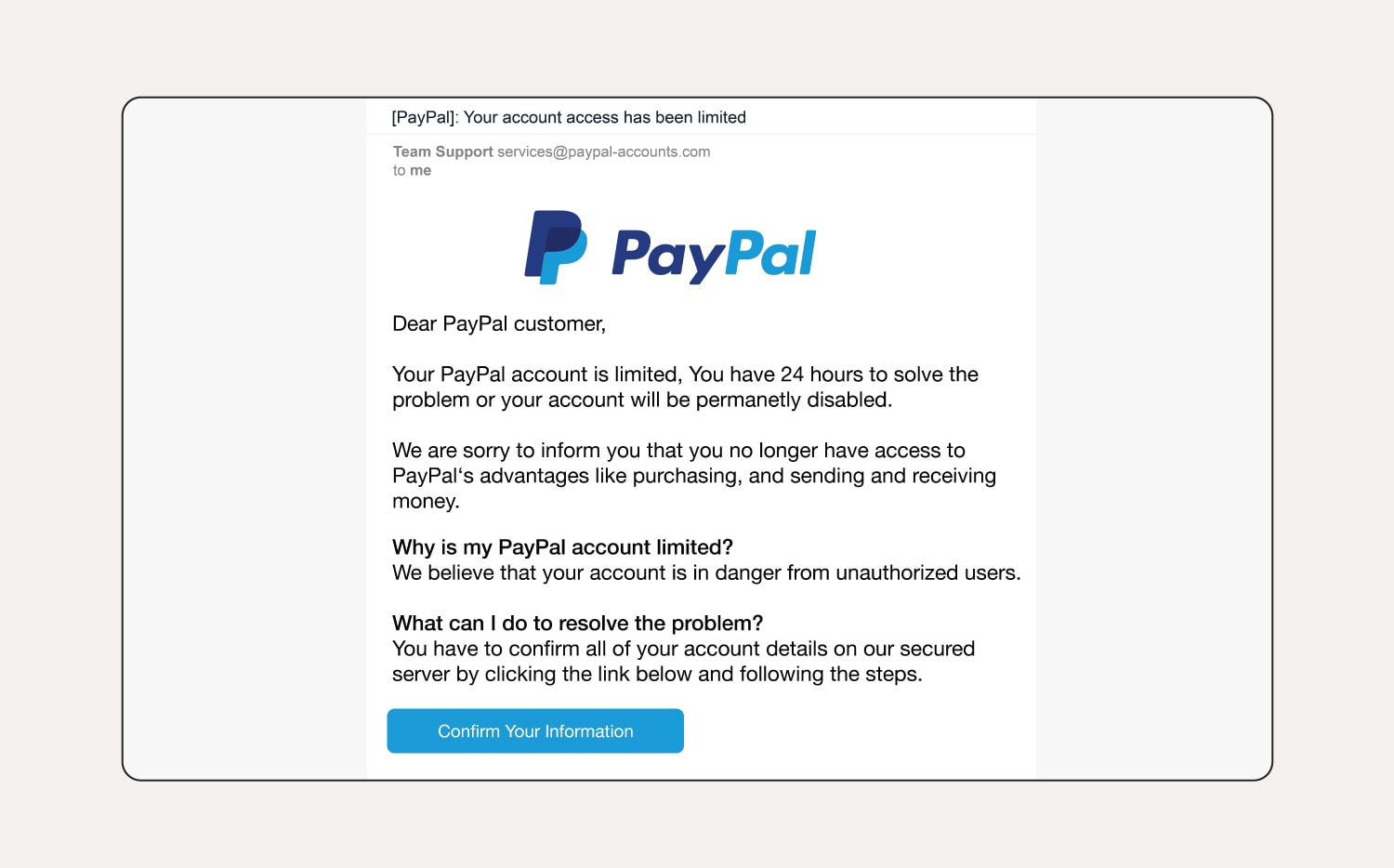
This is a phishing attempt!
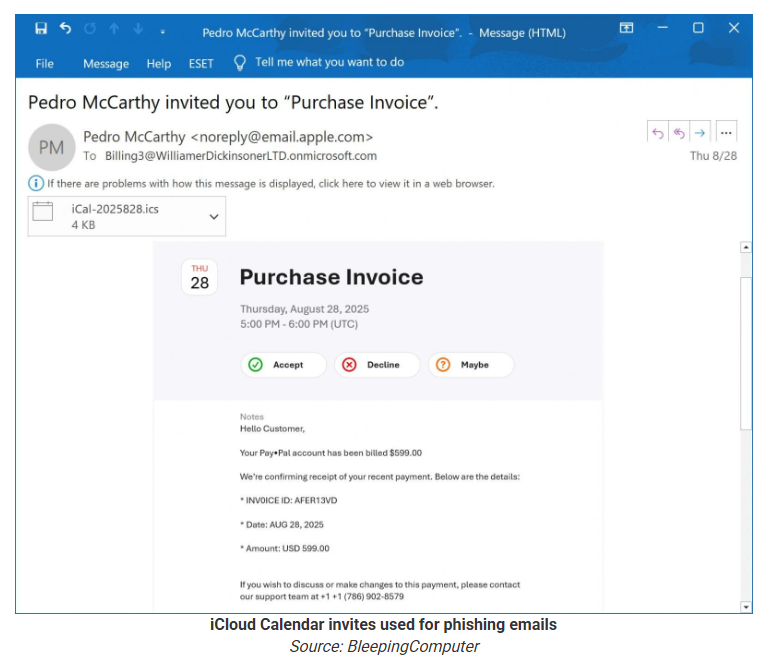
What is a Calendar Invite Scam?
Posting vacation photos in real time can alert criminals that your house is empty, creating this type of physical security risk.
What is BURGLARY RISK (or home invasion risk)?