What does malware stand for?
Malicious Software
What is often the weakest link in a security chain?
Humans
What does DDoS stand for
Distributed Denial of Service
What does a VPN stand for?
Virtual Private Network
What is an insider threats?
An individual within an organization to misuse their access, knowledge, or privileges to cause harm intentionally or unintentionally
What is the worst enemy of security?
complexity
What is a malicious software that encrypts a user’s files and demands payment for their release?
Ransomware
Define Principle of Least Privilege (PoLP)
A concept in information security where a user is granted the minimal access, or permissions, required to carry out their responsibilities.
What are the implications of using a public wifi network?
Subjectable to Man in the middle attacks ,Spoofing, Session hijacking
What are the 3 forms of authentication?
Something you know(pin, password, etc.), something you have(access card, SMS/text, etc.),
something you are(fingerprints, face recognition)
What are the five steps of the software development lifecycle (SDLC)?
Analysis, Design, Implement, Testing, Maintenance
When or where was the Computer Misuse Act passed
1990 in the United Kingdom
What does PDCAERF stand for?
a) Preparation, Detection, Containment, Analysis, Eradication, Repair, Follow-up
b) Preparation, Determination, Containment, Analysis, Eradication, Repair, Follow-up
c) Preparation, Detection, Containment, Authentication, Encryption, Repair, Follow-up
d) Preparation, Determination, Containment, Analysis, Encryption, Repair, Follow-up
a) Preparation, Detection, Containment, Analysis, Eradication, Repair, Follow-up
What is one of the two general goals of social engineering?
Sabotage or Theft
Who created the first computer worm
a.) Bob Thomas
b.) Robert Morris
c.) Joseph Popp
D.) onel de guzman:
a.) Bob Thomas
Decrypt the following using the chart
Wkh Dqvzhu
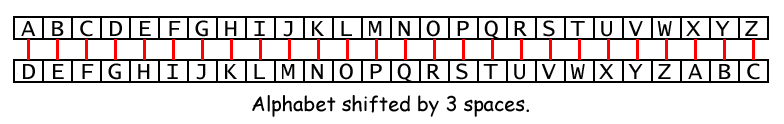
The Answer