This is the percentage of data breaches that a study from IBM attributes to human error
What is 95%?
Technology used to send emails that appear to come from a trusted user
What is email spoofing?
This is the cybercrime business model where ransomware operators write software and affiliates pay to launch attacks using said software. Affiliates do not need to have technical skills of their own but rely on the technical skills of the operators
What is Ransomware as a Service (RaaS)?
Four things all passwords should include.
What are Upper case, lower case, number, special characters?
Password phrases are much more difficult to compromise; ex. "I graduated in 2001"=!Gi2001 OR !Gradi2001
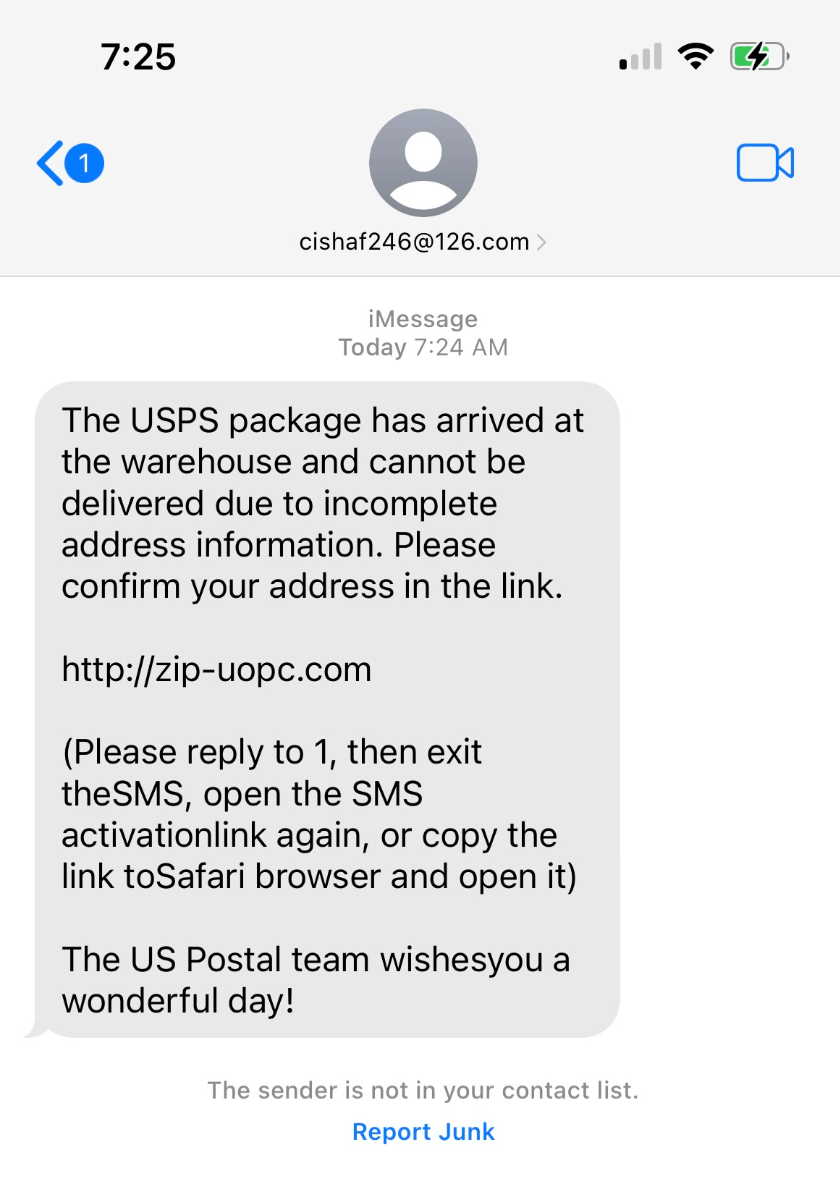
A text message like this one is designed to get PII (Personally identifiable information) from the recipient
What is a smishing scam?
These industries were the top 3 targets of cyber security events in 2022
What are health care, financial services and retail
What are 3 things you do not share online?
What are your...
1. Password
3. Address
3. Phone number
4. Birthdate
5. Social Security Number
This manipulation technique exploits human error to gain private information, access to restricted systems, or valuable data.
What is social engineering?
These modern convenience items make daily life easier for the user but also for cyber criminals, due to the fact that their default settings are frequently left unchanged.
What are the Internet of Things (IoT)?
A password attack that tries every possible combination of letters and numbers
What is Brute Force?
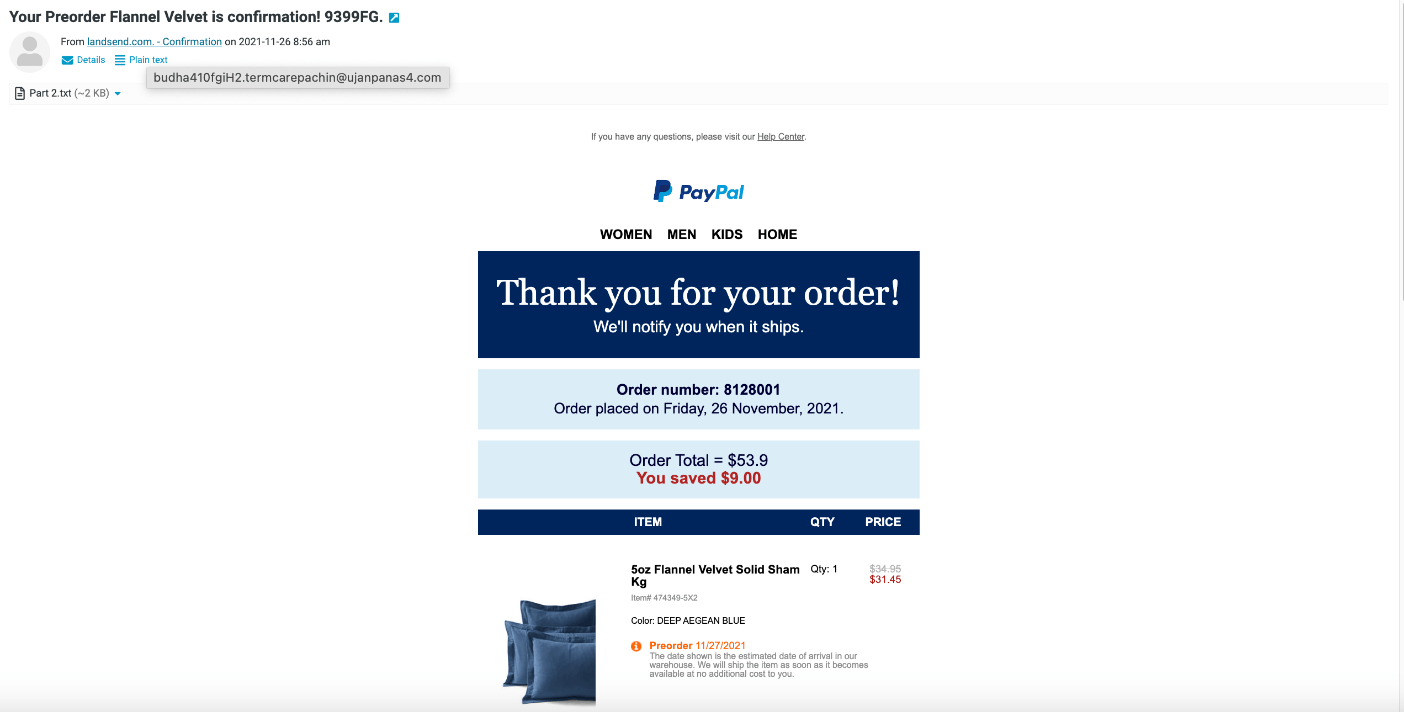
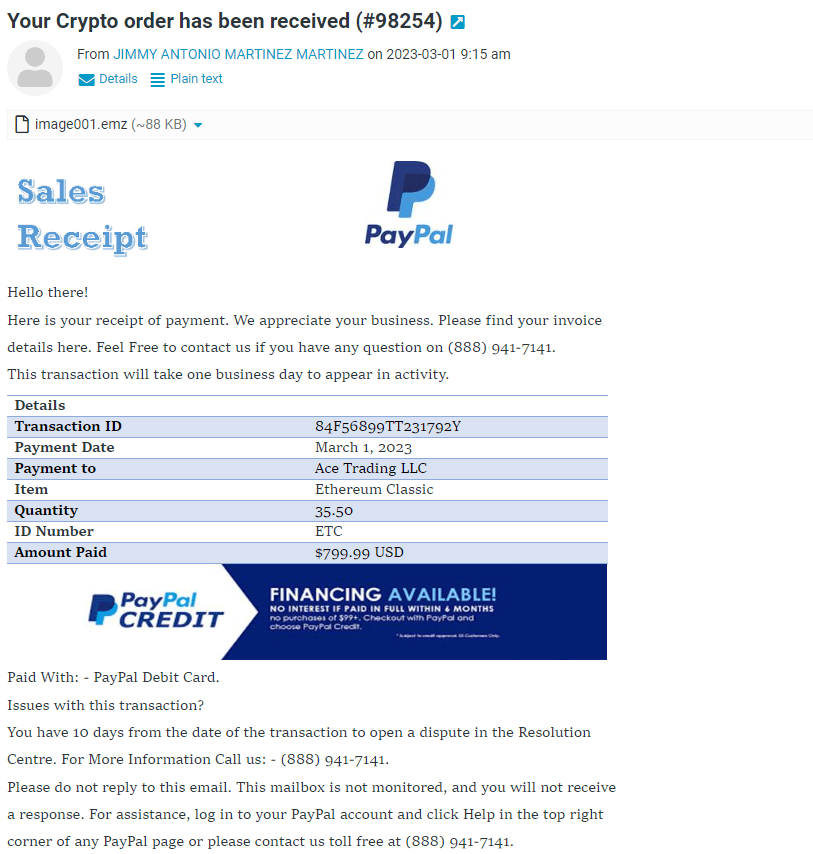
In the email pictured here, this piece of information indicates that this email is suspicious.
What is the sender email address, obtained by hovering over what appears to be a legitimate sender.
The demands in this type of cyber incident increased 144% in 2021
What is ransomware?
The activity you are currently engaged in is one of the best ways to minimize the element of human error in cyber crime.
What is Security Awareness Training?
This major wireless communications provider disclosed in January that a hacker had accessed a trove of personal data for 37 million of the company's customers. A bad actor apparently had access to customer data from November 25, 2022, until the company discovered the intrusion on January 5, 2023. The stolen data includes a customer's name, billing address, email, phone number, date of birth, account number and information such as the number of lines on the account and plan features.
Who is T-Mobile?
This popular family of productivity software has seen an dramatic increase in malware attacks due to it's popularity and misconception that developer provides adequate anti-viral/anti-malware security.
What is Microsoft 365?
This is the process of requiring a second form of identification to log into a system, after providing a valid password. Often this is a physical attribute (fingerprint or face id) or one-time passcode sent via separate application or text.
What is Multi-factor or 2-Factor authentication?
A claim that there is a "problem" with your account, or a request to "verify your identity", update personal information such as password, credit card, social security or bank account numbers like the one shown here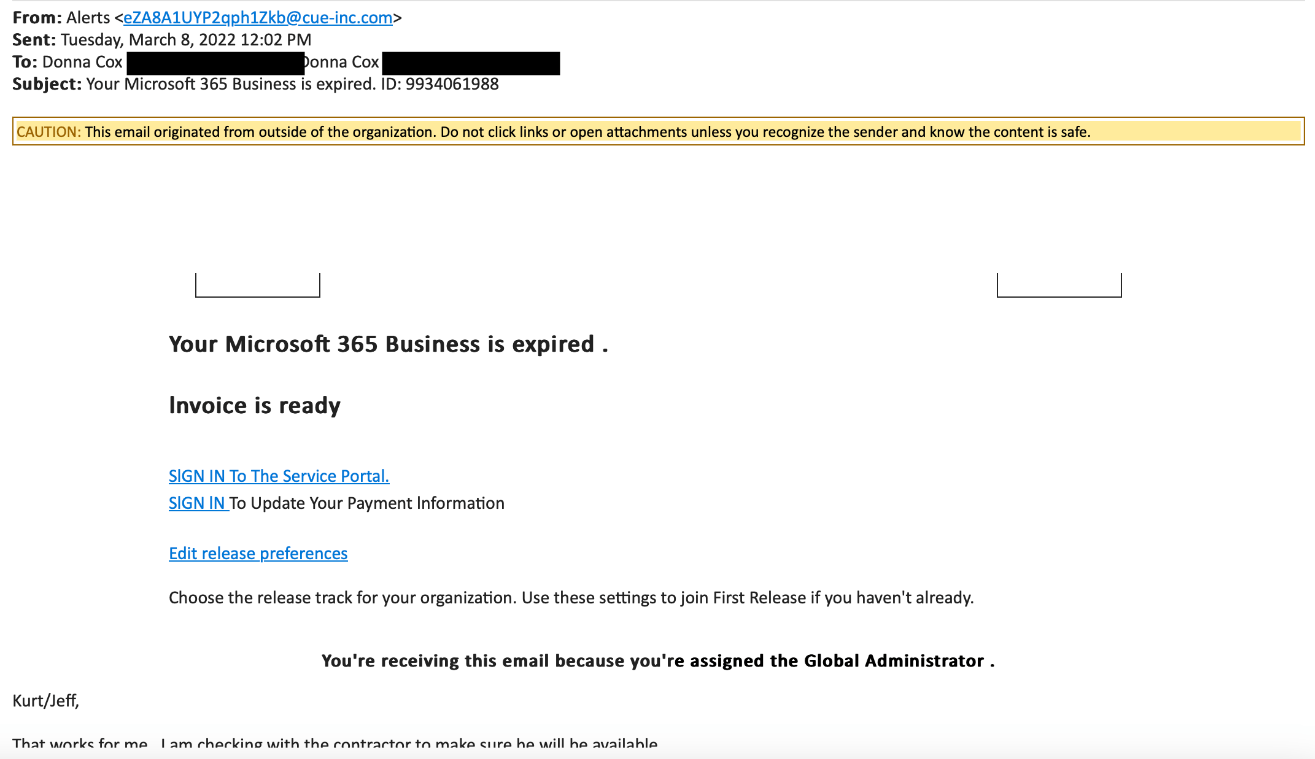
What are examples of a phishing email?
This percentage of a company's data is usually recovered after a ransomware attack
What is 65%?
The policy of limiting employee access to files, based on job function, is call this and is a highly effective way to minimize vulnerability of sensitive data.
What is Selective Access or Zero-Trust policy?
The increase in the remote workforce caused a spike in cyber threats due in part to a lack of this policy in many companies
What is a BYOD policy?
This type of threat appears to be from a trusted source such as a supervisor, can take the form of fraudulent wire transfer directions, bogus invoices, attorney impersonation, bank account misdirection, or socially engineer emails such the one shown here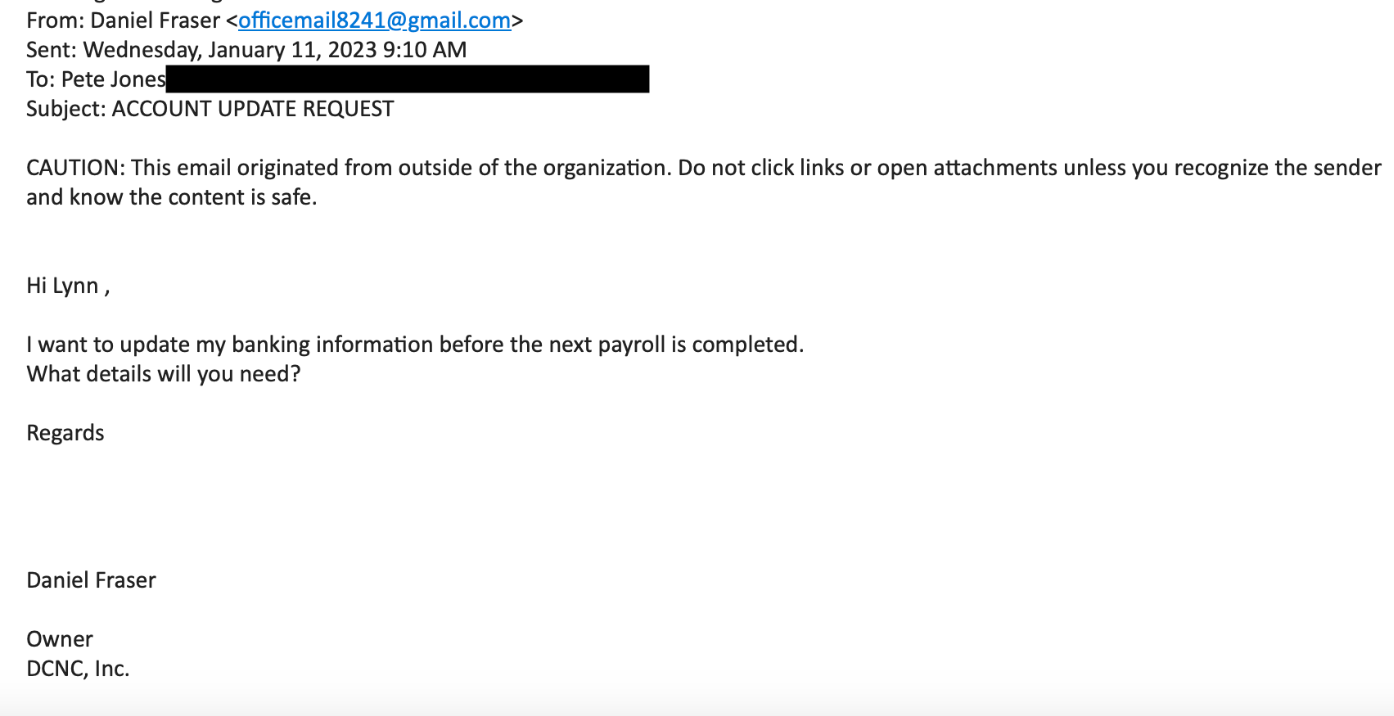
Business Email Compromise?
To initiate this attack, the hacker tries a long list of common words, together with numbers before or after them like people often use.
What is a Dictionary Attack?
This type of phishing campaign targets C-suite executives
What is "whaling"?
This cost an average of $4.35M in 2022.
What is a data breach?
Up to $5.1 M when the majority of the workforce is remote.
This type of phishing attack targets specific individuals by exploiting information gathered through research on such platforms as social media accounts?
What is spear phishing?
Answers to security questions and passwords can also be obtained.
Erratic computer behavior, lack of response to keyboard or mouse commands, crashing or restarting on its own, or running slower than usual are potential symptoms of this
What is a malware infection?
These can be organized crime syndicates, a nation state, a business competitor or a disgruntled employee
Who are threat actors?
This is the term given to the process of fixing code that proves to be a vulnerability in software. Many developers release these fixes on an on-going basis, and the service of Remote Monitoring and Maintenance that DCNC provides helps keep your systems up to date.
What is patch management?
This is what you should do if you receive an email notification like the one pictured below.
According to the Cybersecurity and Infrastructure Security Agency, this is the number of cybersecurity attacks reported to the Pentagon every day
What is over 300,000?