Technology used to send emails that appear to come from a trusted user
What is email spoofing?
Four things all passwords should include.
What are Upper case, lower case, number, special characters?
Password phrases are much more difficult to compromise; ex. "I graduated in 2001"=!Gi2001 OR !Gradi2001
What are 3 things you do not share online?
What are your...
1. Password
3. Address
3. Phone number
4. Birthdate
5. Social Security Number
This manipulation technique exploits human error to gain private information, access to restricted systems, or valuable data.
What is social engineering?
These modern convenience items make daily life easier for the user but also for cyber criminals, due to the fact that their default settings are frequently left unchanged.
What are the Internet of Things (IoT)?
A password attack that tries every possible combination of letters and numbers
What is Brute Force?
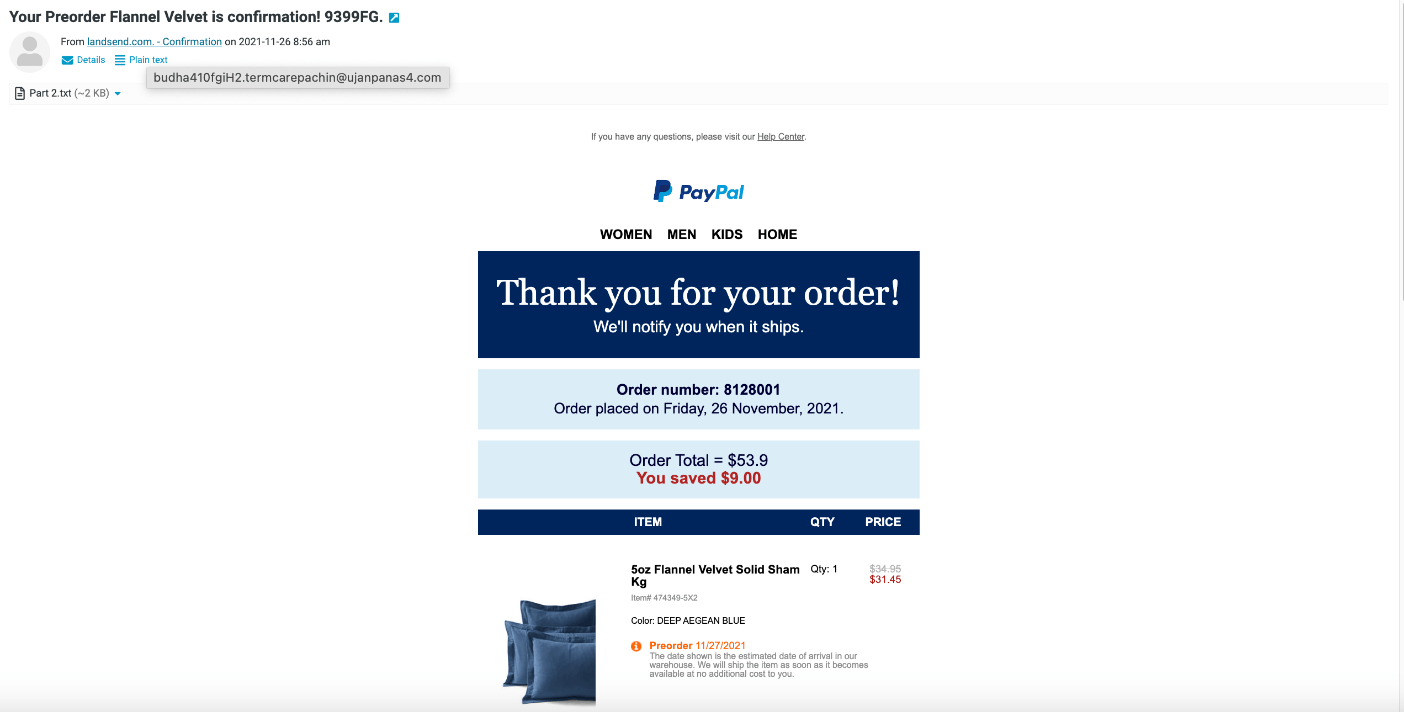
In the email pictured here, this piece of information indicates that this email is suspicious.
What is the sender email address, obtained by hovering over what appears to be a legitimate sender.
The activity you are currently engaged in is one of the best ways to minimize the element of human error in cyber crime.
What is Security Awareness Training?
How Will Cybersecurity be Beneficial to People?
- Protects programs
- Sends warnings to the user's device
- Operating at all times
A claim that there is a "problem" with your account, or a request to "verify your identity", update personal information such as password, credit card, social security or bank account numbers like the one shown here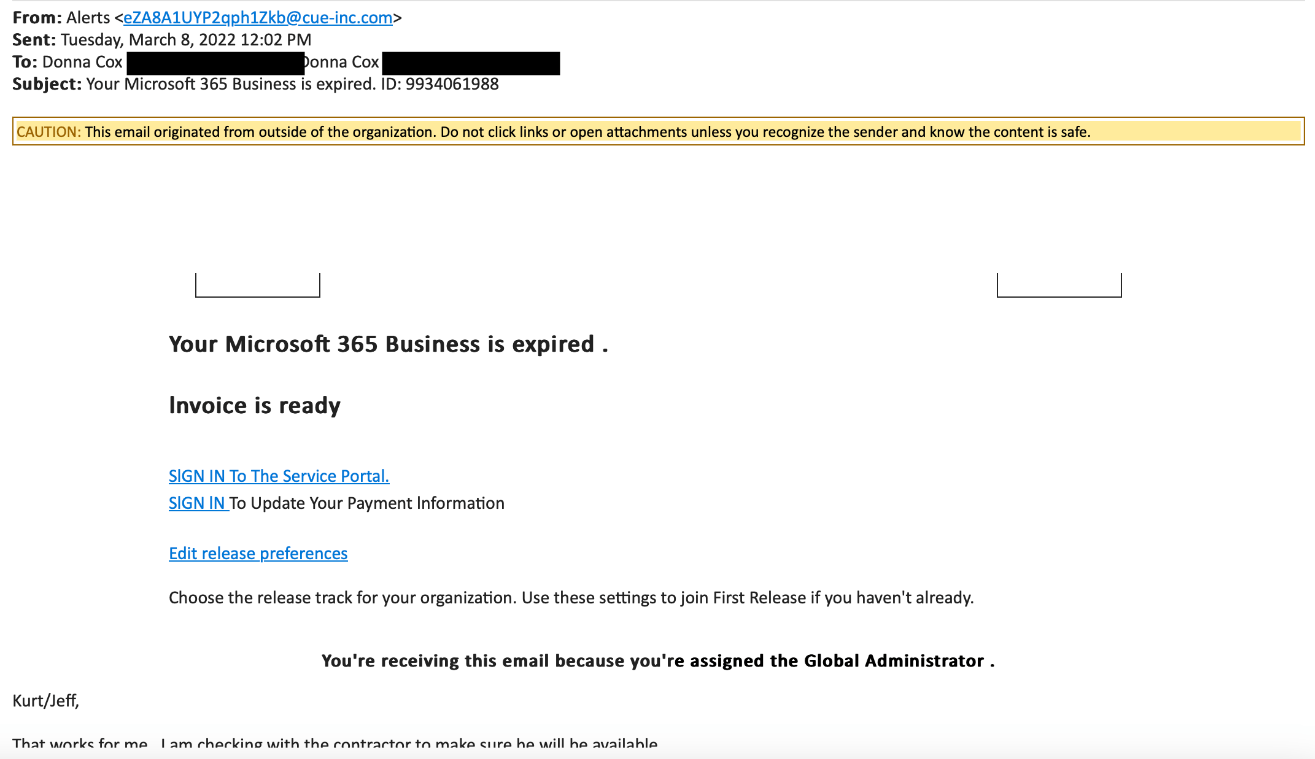
What are examples of a phishing email?
This type of threat appears to be from a trusted source such as a supervisor, can take the form of fraudulent wire transfer directions, bogus invoices, attorney impersonation, bank account misdirection, or socially engineer emails such the one shown here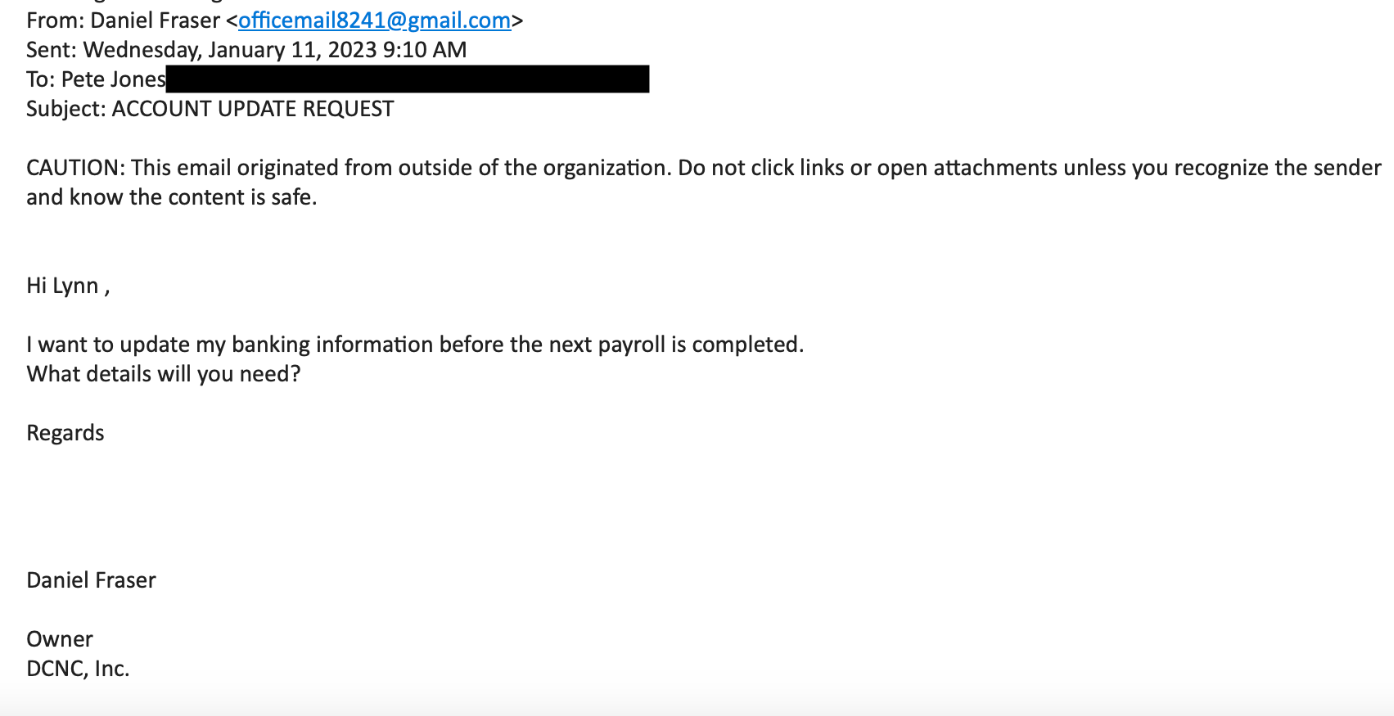
Business Email Compromise?
What you should do if you suspect you have received a phishing email.
Need to report to the IT technical team.