This type of intelligence is a program or organization that provides threat intelligence feeds and briefs to paying customers. Typically subscription based.
What is Closed-Source Intelligence?
The process of providing multiple forms or "factors" of information to prove your identity.
What is Multifactor Authentication?
Disabling unnecessary services and/or devices, restricting user accounts to least privilege, disabling unused switchports, patching OS and updating antimalware are all examples of what action being taken?
What is System Hardening? also accept (Reducing Attack Surface)
Having this set up ahead of time will prevent an inadvertent leak of information on an incident occurring in your organization.
What is a Communication Plan?
A control that uses technology to implement its purpose.
What is a Technical Control?
This is a tool used to capture HTTP requests in the middle of a session and allows the controller to analyze and amend HTTP requests.
What is an Intercept Proxy? (BurpSuite) or (ZAP)
This port would probably be found open on a local DNS server.
What is Port 53?
You include this flag in your NMAP command if you want it to scan every port.
what is (-p-)?
This is an organization that offers an attack framework that provides detailed descriptions of various attacker TTPs, as well as how to defend against said TTPs
What is The MITRE ATT&CK Framework?
This can be accomplished by adding a user to an existing Group (e.g. Accounting) with particular GPOs set up to limit the user's access to distinct files/folders relating to their job.
This term describes means by which an attacker can gain access to targets.
What is Attack Vector?
Involving this entity in your incident response should be carefully considered. It's involvement more than likely will involve criminal proceedings and public disclosure.
What is Law Enforcement?
What is a Tabletop Exercise?
This is a multi-cloud platform tool that helps detect vulnerabilities in cloud environments.
What is ScoutSuite?
This port supports windows file sharing with pre-windows 2000 version hosts. Known as NetBIOS-ssn.
What is Port 139?
Reverse Jeopardy!!!! Write the command that would change Group access to allow them to read and write to Lordofyeets_folder, assuming you are making the changes as the user shown below./
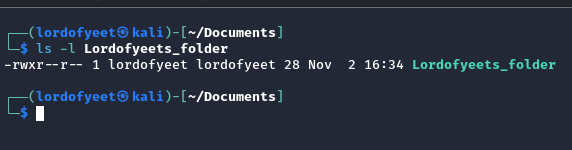
(chmod 764 Lordofyeets_folder)
or
(chmod g+w Lordofyeets_folder)
This describes a Vulnerability Scanner not reporting on a vulnerability that was confirmed to be on a system or network.
What is a False Negative?
This is a machine that allows Administrators to remotely access different network segments to perform system maintenance. This system is typically very hardened.
What is a Jump box?
This action is taken by altering DNS records to reroute malicious C2 traffic to a address that is different than the malicious address.
What is a Sinkhole?
This action takes place during the Eradication and Recovery phase of Incident Response. These are procedures that are used in the disposal of obsolete information and equipment including storage devices, devices with internal data storage capabilities, and paper records.
What is Sanitization?
A technique of constantly evaluating an environment for changes so that new risks may be more quickly detected and business operations improved upon.
What is Continuous Monitoring?
This is a set of tools that help with wireless network security testing, includes tools that captures wireless frames, injects wireless frames, and extracts wireless authentication keys.
What is a Mail Server?
(Reverse Jeopardy!!!) The below image is an example of?
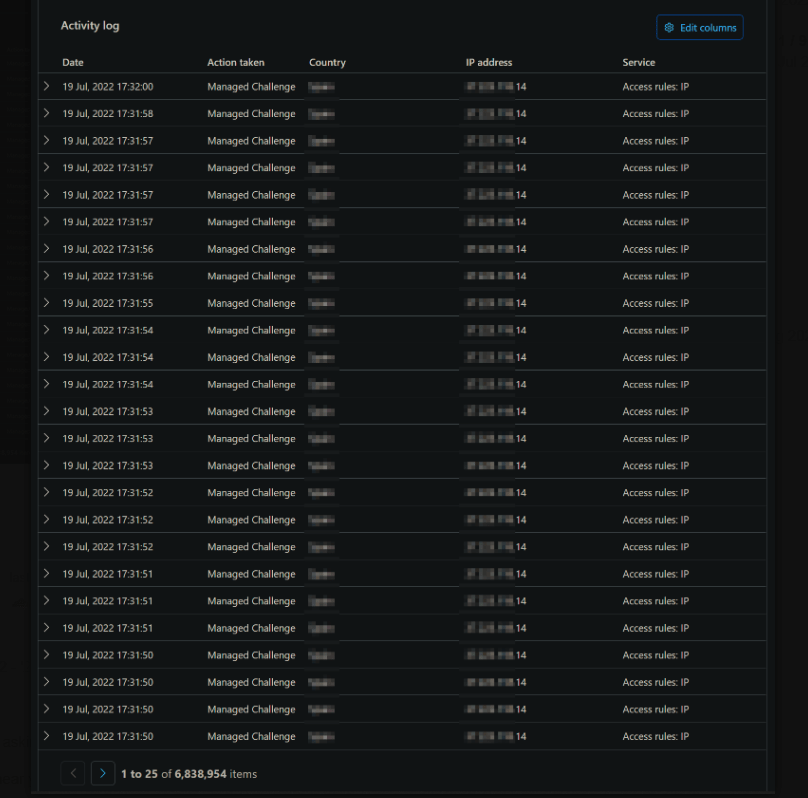
What is a DoS?
This is the act of using scripting/programming that allows administrators to very quickly set up and tear down server instances in the cloud, as well as facilitate security automation.
What is Infrastructure as Code (IaC)?
This occurs when the UEFI of a system sends a report to a separate management server, confirming a secure, step by step boot process has been completed.
What is Measured Boot Attestation, or just (Measured Boot)
This Provides email authentication by allowing mail servers to digitally sign legitimate outbound email messages and is a mitigation against phishing/spam.
What is DKIM?
This is internal traffic between two or more systems that is a tell-tale sign of an attacker trying to pivot through the network.
What is Irregular Peer-to-Peer Communication?
A concept that describes how depending on where you are geographically, the laws may be different and therefore data must be treated differently.
What is Data Sovereignty?
A command line tool that is a Link Local Multicast Name Resolution (LLMNR), NBT-NS, and MDNS poisoner. It allows the attacker to retrieve user hashes and OS info, making this an efficient tool for harvesting credentials and reconnaissance.
What is Responder?
What is SNMP?
Below is something you would see while using this tool: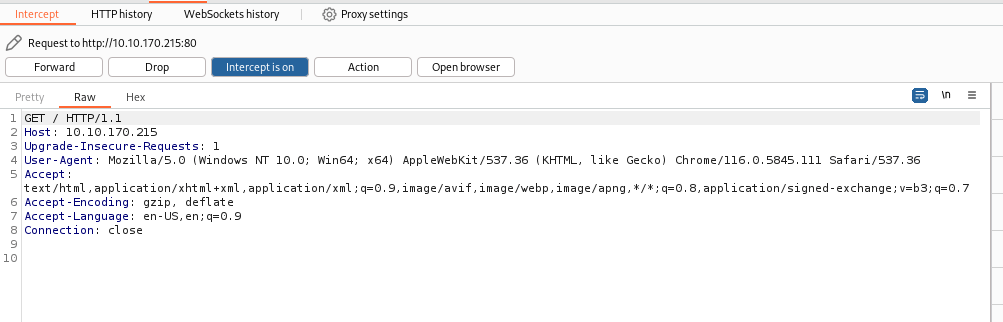
What is an Interception Proxy? or BurpSuite
A processor that can be programmed to perform a specific function by a customer rather than at the time of manufacture.
What is a FPGA (Field Programmable Gate Array)?
Methods that make it difficult for an attacker to alter the authorized execution of software. A PUF (Physically unclonable function) is an example of this.
What is Anti-Tamper?
Provides increased endpoint security by combining endpoint data monitoring with centralized processing to detect and act on malicious activity.
What is EDR (Endpoint Detection and Response)?
This is an activity done in the Post-Incident Activities phase of Incident Response where analysts and IT document malicious behaviors, signatures, and anomalies they discovered during the incident, so that they can watch for them in the future.
What is IoC generation?
This describes A role focused on the quality of the data and associated metadata; Makes sure data is appropriately labelled and classified.
What is a Data Steward?
A command-line tool used to perform brute force attacks against WPS-enable access points.
What is Reaver?
This port is associated with Routing Information Protocol (RIP) which is a distance vector protocol.
What is Port 520?
This flag needs to be included in your nmap scan when crafting an idle (zombie) scan.
What is (-sI)?