This type of malware encrypts a victim's data and demands a ransom for the decryption key.
What is Ransomware?
The initial phase of the Incident Response life cycle where plans and preparations are made.
What is Preparation?
Cellebrite and Oxygen are types of these that extract data from Android and iOS devices.
What are mobile forensic tools?
The process of continuously monitoring systems and networks for unusual activity that could indicate a security incident.
What is Event Monitoring?
A strategy used to prevent the spread of an infection by isolating affected systems.
What is Quarantine?
The installation of malicious software on a system without consent, which can lead to data theft or system disruption.
What is Malware Infection?
The phase where potential security incidents are identified and reported.
What is Detection?
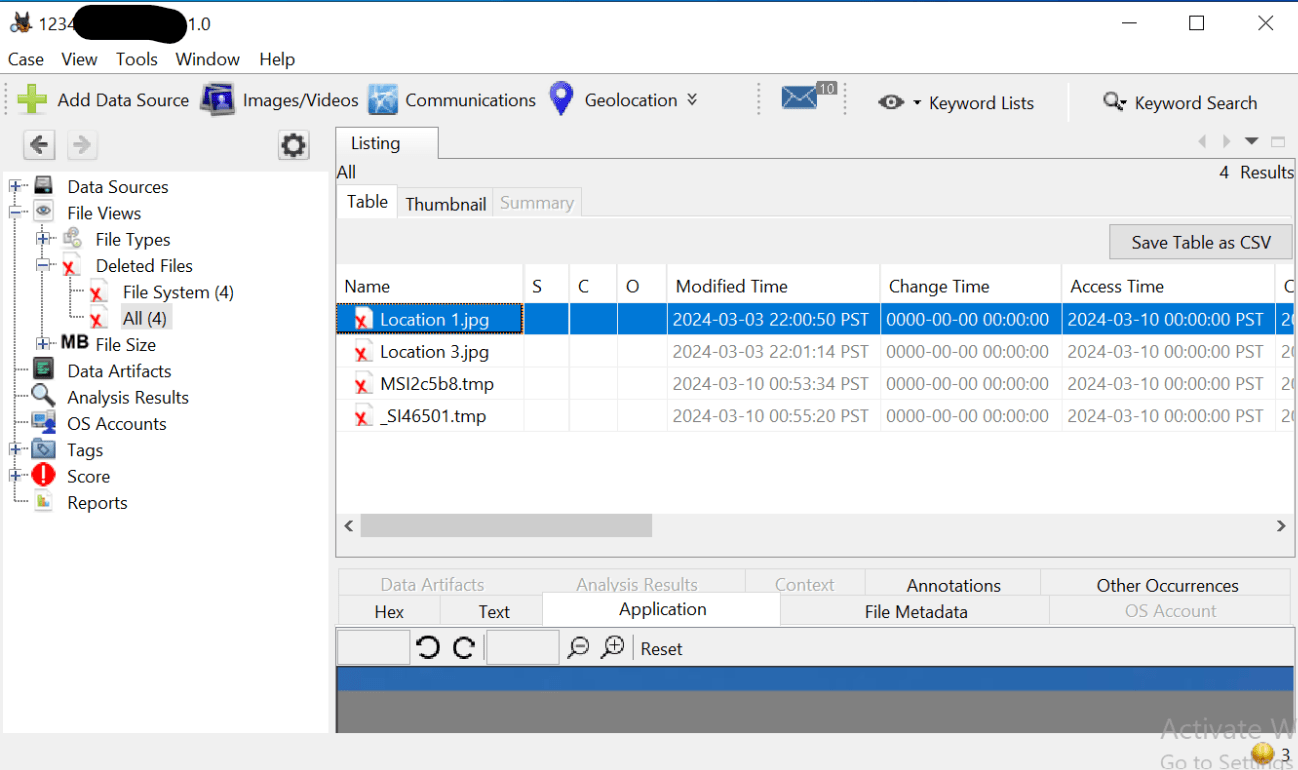
An open-source digital forensic tool used for data analysis and recovery.
What is Autopsy?
This process of effectively responding to security breaches by determining the breach's extent and prioritizing response activities like containment and system restoration.
What is Incident Scoping?
The person who disseminates information about an incident to staff, stakeholders, or the public.
Unauthorized access to sensitive information leading to its exposure or theft.
What is a Data Breach?
Activities conducted after an incident to improve future response efforts and prevent recurrence.
What is Post-Incident Activity?
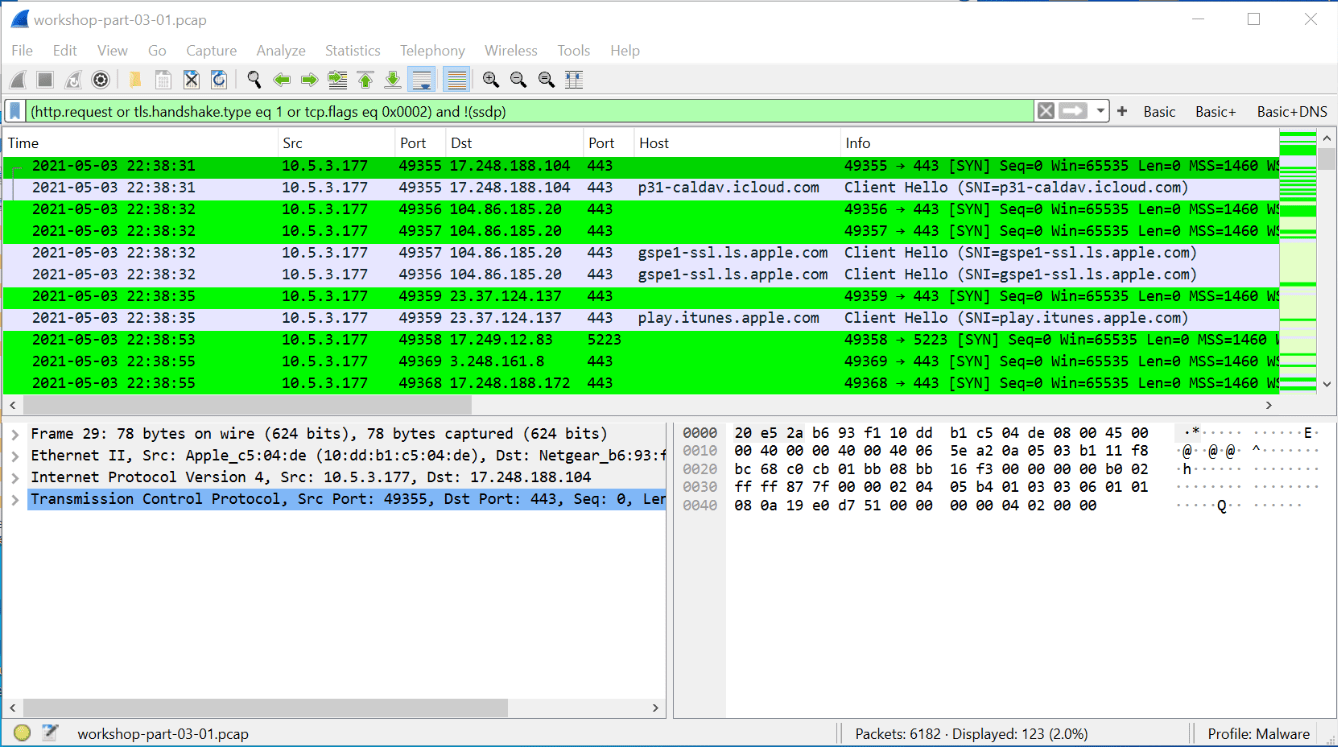
Software used for packet analysis and network troubleshooting
What is Wireshark?
A method to confirm that an event or series of events constitutes a security incident and not a false positive.
What is Incident Validation?
This refers to indicators that warn an incident has occurred or is currently occurring, such as unscheduled login attempts.
What are Indicators of Compromise (IoCs)?
Manipulating individuals into divulging confidential information through tactics like impersonation.
What is Social Engineering?
The process of removing the threat and restoring systems to normal operation.
What is Eradication and Recovery?

A freely available hex editor used for manually carving data from files and images.
What is HxD?
In this step of the Incident Response process, teams aim to preserve evidence, assess the breach's extent, and identify IOCs by gathering logs, network traffic, system images, process memory, and configuration files.
The role identified as the first to detect the SolarWinds Hack, showcasing the importance of external threat intelligence.
Who is FireEye?
This attack overwhelms a system with excessive traffic, rendering it inaccessible to legitimate users.
What is a Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack?
This phase involves stopping the spread of the incident and isolating affected systems.
What is Containment?
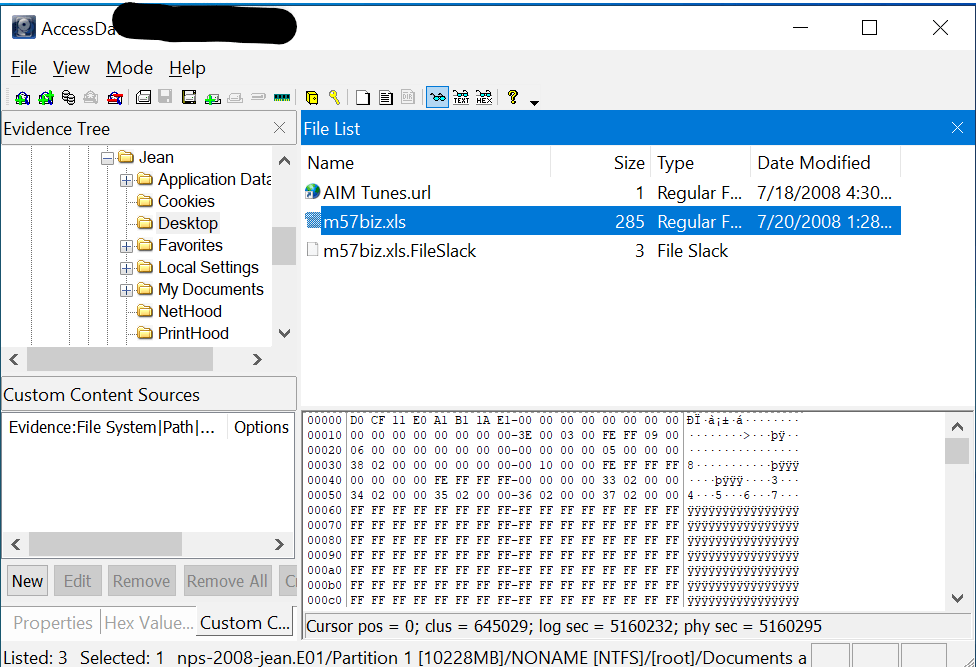
This freely available tool is used for creating forensic images of digital media.
What is FTK Imager?
This component of the IR detection process utilizes tools like SIEM systems, and techniques such as log, traffic, and endpoint analysis, to identify security incidents that event monitoring might miss.
What is Event Correlation?
A type of exercise used to simulate incident response scenarios to test and refine the IR plan.
What are tabletop exercises?