DineOutHelper is a mobile application that people can use to select a restaurant for a group meal. Each user creates a profile with a unique username and a list of food allergies or dietary restrictions. Each user can then build a contact list of other users of the app.
A user who is organizing a meal with a group selects all the members of the group from the user’s contact list. The application then recommends one or more nearby restaurants based on whether the restaurant can accommodate all of the group members’ allergies and dietary restrictions.
Suppose that Alejandra is using DineOutHelper to organize a meal with Brandon and Cynthia.
What data is not provided by Alejandra but is necessary for DineOutHelper to recommend a restaurant for the group?
- Information about which food allergies and dietary restrictions can be accommodated at different restaurants near Alejandra
Byte pair encoding is a data encoding technique. The encoding algorithm looks for pairs of characters that appear in the string more than once and replaces each instance of that pair with a corresponding character that does not appear in the string. The algorithm saves a list containing the mapping of character pairs to their corresponding replacement characters.
For example, the string can be encoded as
by replacing all instances of
with
and replacing all instances of
with
.
Is this a lossy or lossless algorithm?
Byte pair encoding is an example of a lossless transformation because an encoded string can be restored to its original version.
The cost of a customer’s electricity bill is based on the number of units of electricity the customer uses.
- For the first 25 units of electricity, the cost is $5 per unit.
- For units of electricity after the first 25, the cost is $7 per unit.
Write a code segment that correctly sets the value of the variable cost to the cost, in dollars, of using numUnits units of electricity.

A certain computer has two identical processors that are able to run in parallel. The table below indicates the amount of time it takes each processor to execute each of two processes. Assume that neither process is dependent on the other.
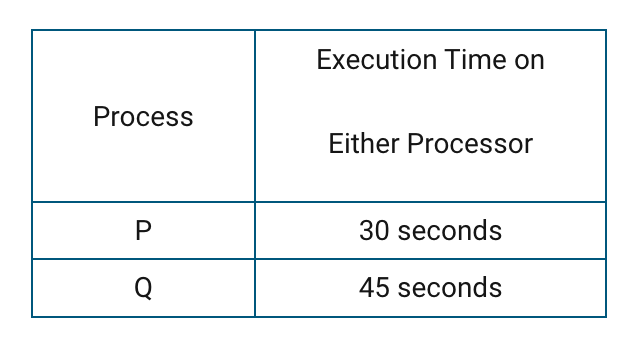
What is the difference in execution time between running the two processes in parallel instead of running them one after the other on a single processor?
30 seconds
Name a piece of information that has potential for compromising a user’s personal privacy.
A group of cookies stored by the user’s Web browser
In the following procedure, the parameters x and y are integers.

Give an example appropriate documentation to appear with the calculate procedure.
Displays the value of (x + y) / x.
The value of the parameter x must not be 0.
A file storage application allows users to save their files on cloud servers. A group of researchers gathered user data for the first eight years of the application’s existence. Some of the data are summarized in the following graphs. The line graph on the left shows the number of registered users each year. The line graph on the right shows the total amount of data stored by all users each year. The circle graph shows the distribution of file sizes currently stored by all users.
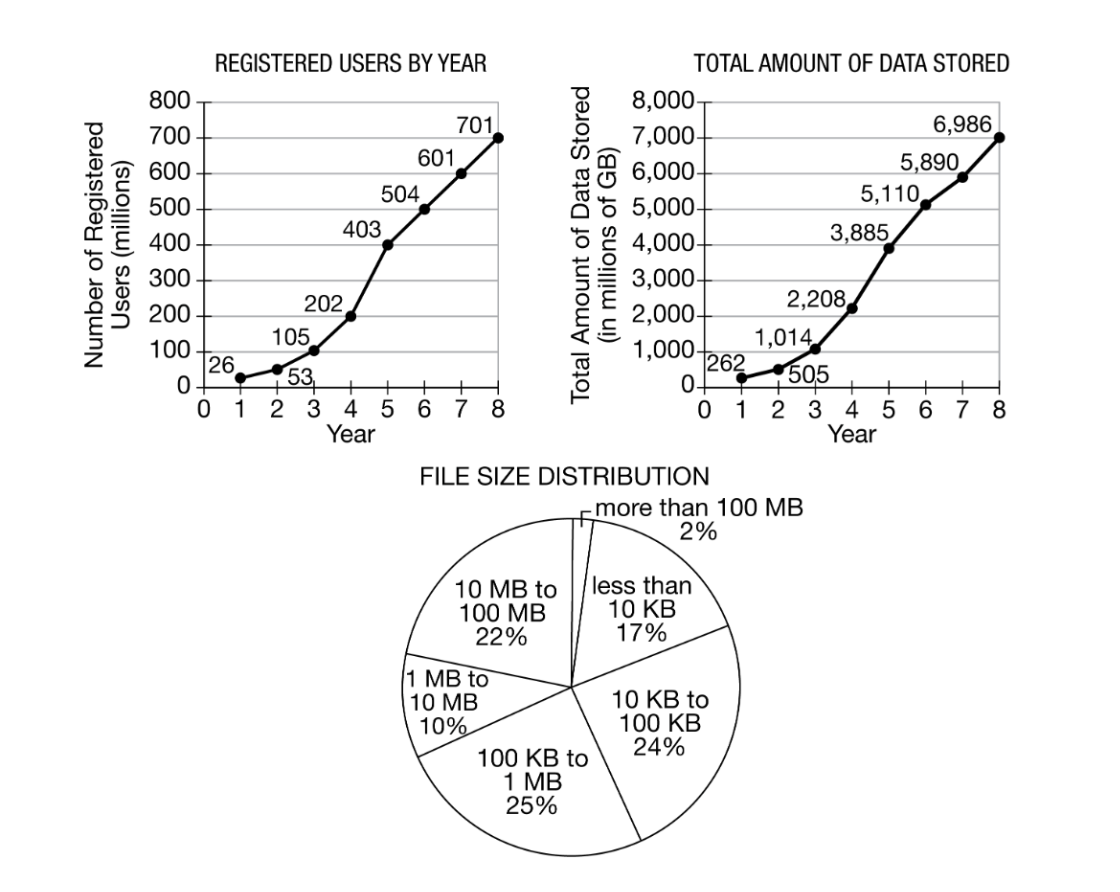
(note: 1 MB = 1,000 KB)
How did the average amount of data stored per user change over the first eight years of the application’s existence?
Across all eight years, the average amount of data stored per user was about 10 GB.
Consider the following code segment, where exam and presentation are integer variables and grade is a string variable.
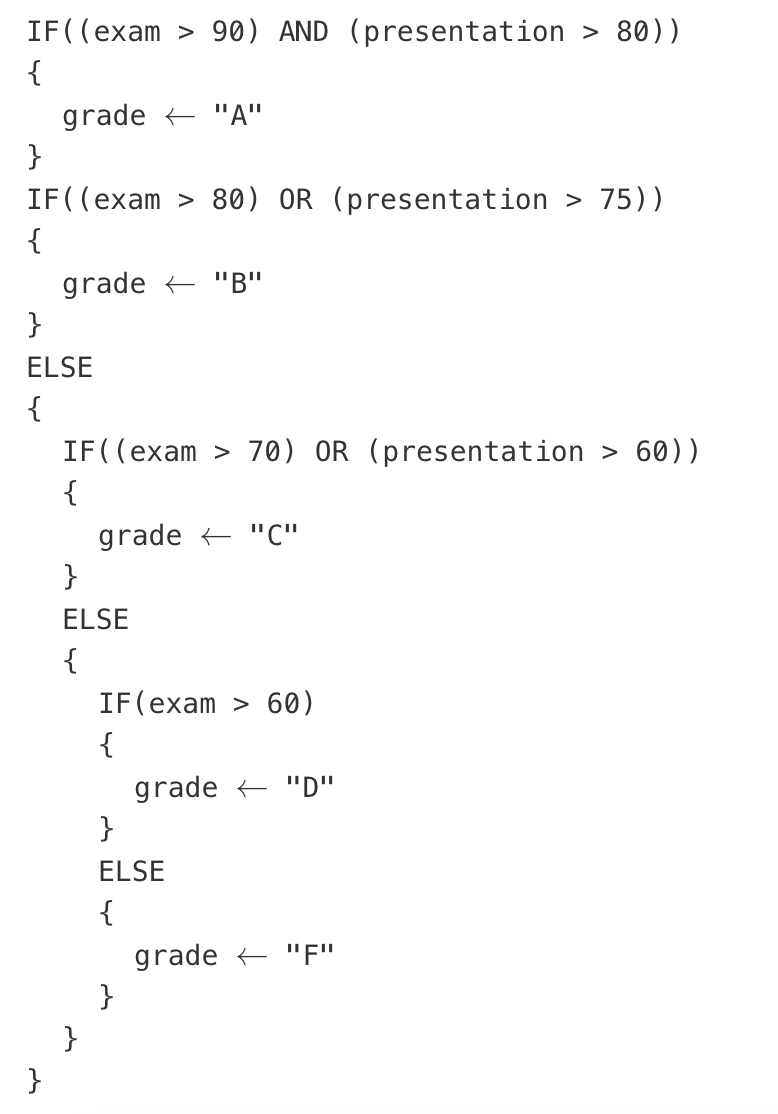
Under what conditions will the value "C" be assigned to the variable grade ?
When the value of exam is 80 and the value of presentation is 60
Explain how data is transmitted on the Internet.
Data is broken into packets, which can be sent along different paths.
MeeReader is an e-reading application that allows users to download and read books and articles on a device. Each user creates a profile with the following personal preferences.
- Screen brightness and contrast
- Choice of typeface and font size
- Amount of spacing between lines of text
- Activation of a text-to-speech feature that reads the text out loud
When the user launches the application, the application scans the user’s face and uses facial recognition software to determine the user’s identity. Once the user has been identified, the user’s personal preferences are applied to whatever book or article the user chooses to read.
The application stores all user information in a database, including personal preferences and a record of previously read books and articles.
Name a benefit of storing all user data in a database.
The developers can analyze the data to make improvements to the application based on user behavior.
A programmer wrote the program below. The program uses a list of numbers called numList. The program is intended to display the sum of the numbers in the list.

In order to test the program, the programmer initializes numList to [0, 1, 4, 5]. The program displays 10, and the programmer concludes that the program works as intended.
Is this true?
The conclusion is incorrect; using the test case [0, 1, 4, 5] is not sufficient to conclude the program is correct.
Two lists, list1 and list2, contain the names of books found in two different collections. A librarian wants to create newList, which will contain the names of all books found in either list, in alphabetical order, with duplicate entries removed.
For example, if list1 contains
["Macbeth", "Frankenstein", "Jane Eyre"]
and list2 contains
["Frankenstein", "Dracula", "Macbeth", "Hamlet"],
then newList will contain
["Dracula", "Frankenstein", "Hamlet", "Jane Eyre", "Macbeth"].
The following procedures are available to create newList.
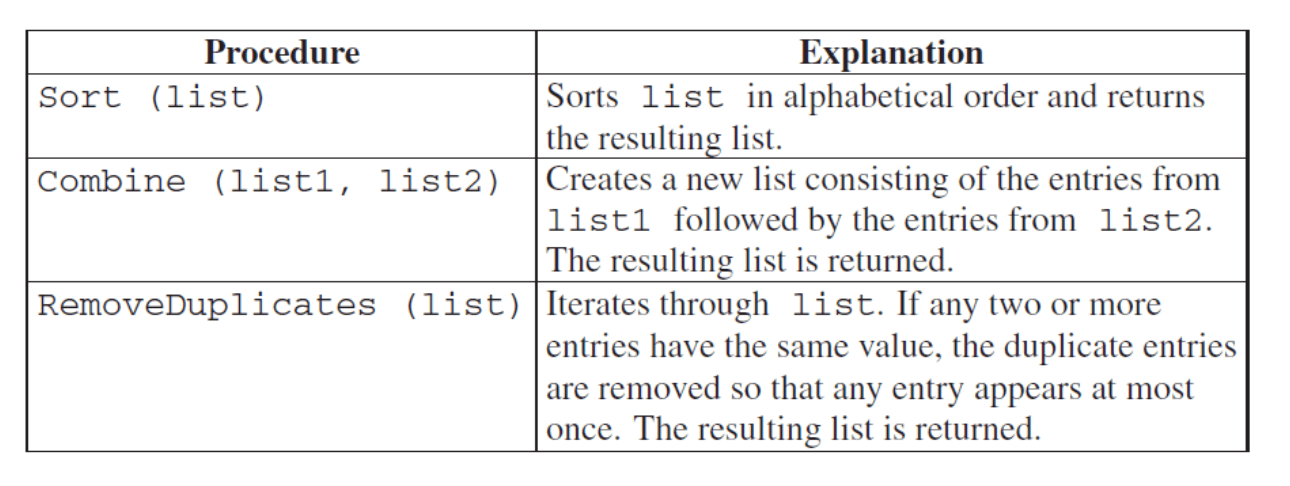
Write some code to create newList.
newList ← Combine (list1, list2)
newList ← Sort (newList)
newList ← RemoveDuplicates (newList)
Write an algorithm to display all integers between 1 and 20, inclusive, that are not divisible by 3.
Step 1:Set x to 0.
Step 2:Increment x by 1.
Step 3:If x is not divisible by 3, then display x.
Step 4:Repeat steps 2 and 3 until x is 20.
Step 1: Set x to 1.
Step 2: If x is divisible by 3, then do nothing; otherwise display x.
Step 3:Increment x by 1.
Step 4: Repeat steps 2 and 3 until x is greater than 20.
Explain how the Internet is a fault-tolerant system.
The Internet is fault-tolerant because there are usually multiple paths between devices, allowing messages to sometimes be sent even when parts of the network fail.
Name a contributing factor to the digital divide.
Some individuals and groups are economically disadvantaged and cannot afford computing devices or Internet connectivity.
Some individuals and groups do not have the necessary experience or education to use computing devices or the Internet effectively.
Some residents in remote regions of the world do not have access to the infrastructure necessary to support reliable Internet connectivity.
RunRoutr is a fitness tracking application for smartphones that creates suggested running routes so that users can run with each other. Upon downloading the application, each user creates a username, a personal profile, and a contact list of friends who also use the application. The application uses the smartphone’s GPS unit to track a user’s location, running speed, and distance traveled. Users can use the application to review information and statistics about their previous runs.
At the beginning of a run, users indicate the distance they want to run from their current location, and the application suggests a running route. Once a user accepts a suggested route, the application shares the suggested route with other compatible users in the area so that they can run together. Users are considered compatible if they are on each other’s contact lists or if they typically run at similar speeds.
A basic RunRoutr account is free, but it displays advertisements that are targeted to individual users based on data collected by the application. For example, if a user’s running route begins or ends near a particular store, the application may display an advertisement for that store. Users have the ability to pay a monthly fee for a premium account, which removes advertisements from the application.
Adrianna uses RunRoutr to suggest a running route. All compatible users near Adrianna receive a notification that shows her running route. What data is not obtained using data collected from Adrianna’s smartphone but necessary for RunRoutr to share Adrianna’s running route?
The current locations of other RunRoutr users
A video game character can face toward one of four directions: north, south, east, and west. Each direction is stored in memory as a sequence of four bits. A new version of the game is created in which the character can face toward one of eight directions, adding northwest, northeast, southwest, and southeast to the original four possibilities. How many bits need to be added to the representation to make this change?
Four bits are enough to store the eight directions.
In the following code segment, assume that x and y have been assigned integer values.

Rewrite this code so that the value of sum the same as the value of sum at the end of the preceding code segment.
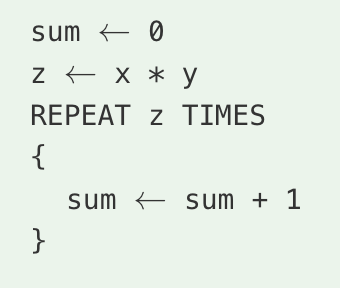
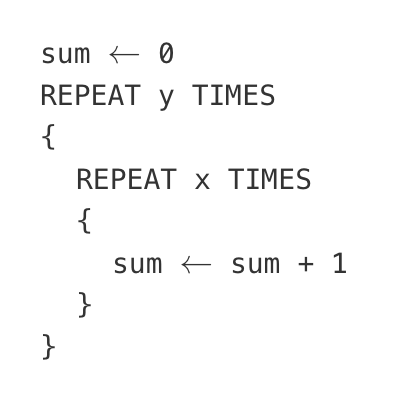
A certain computer has two identical processors that are able to run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. The following table indicates the amount of time it takes to execute each of three processes on a single processor. Assume that none of the processes are dependent on any of the other processes.
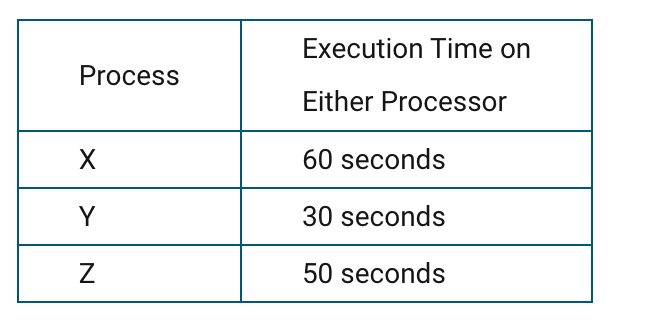 What is the minimum possible time to execute all three processes when the two processors are run in parallel?
What is the minimum possible time to execute all three processes when the two processors are run in parallel?
80 seconds
A software company is designing a mobile game system that should be able to recognize the faces of people who are playing the game and automatically load their profiles. How could they reduce the possibility of bias in the system?
Testing the system with people of different ages, genders, and ethnicities
In the following procedure, the parameter numList is a list of numbers and the parameters j and k are integers.
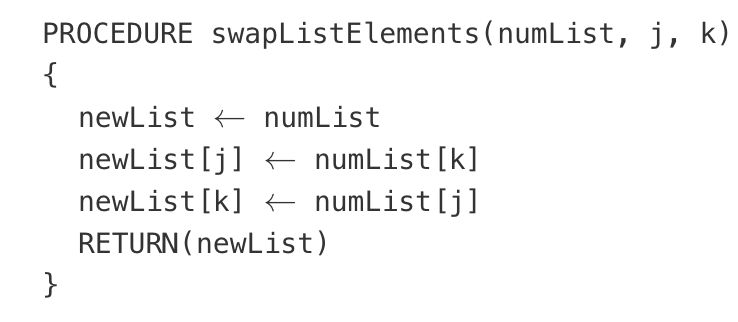
Give an example appropriate documentation to appear with the swapListElements procedure.
Returns a copy of numList with the elements at indices j and k interchanged.
The values of j and k must both be between 1 and LENGTH(numList), inclusive.
Give a short description of the trade-offs lossy vs lossless data compression.
There are trade-offs involved in choosing a compression technique for storing and transmitting data.
268 of 476
268 of 476
Question
Shoppers at a mall were asked whether they preferred wearing gloves or mittens in cold weather. Shoppers’ preferences were stored in the list voteList as strings, with the string "Gloves" representing a preference for gloves and the string "Mittens" representing a preference for mittens.
The following code segment is intended to traverse the list and display the number of shoppers who chose gloves and the number of shoppers who chose mittens.
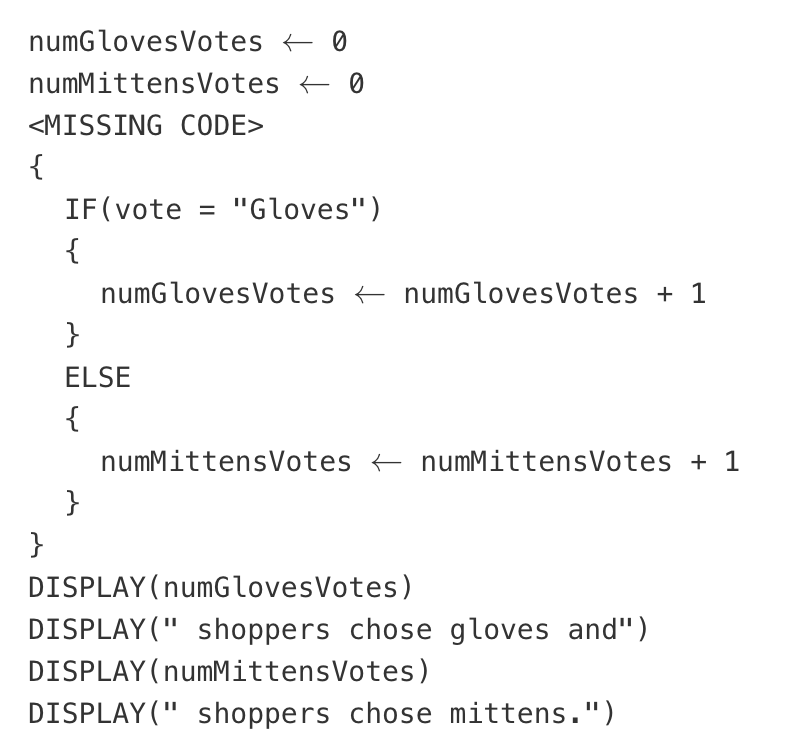
What should replace <MISSING CODE> so that the code segment works as intended?
FOR EACH vote IN voteList
Describe the behavior of packets that are transmitted over the Internet.
The message is broken into packets. The packets can be received in any order and still be reassembled by the recipient’s device.
A system is being developed to help pet owners locate lost pets. How might this system use crowdsourcing?
A mobile application that allows users to report the location of a pet that appears to be lost and upload a photo that is made available to other users of the application