Which cybercrime is considered to be a form of harassment?
Pharming
Clickjacking
Cyber-stalking
Phishing
Cyber-stalking
P2P networks are normally found in ________.
corporations
universities
homes
libraries
homes
The SDLC follows the development of a system from planning to the final stage, ________.
maintenance
implementation
analysis
design
maintenance
Jules has walked away from a lab computer without logging off. Trish sits down and, still logged in as Jules, sends inflammatory e-mail messages out to several students and posts similar messages on the class newsgroup.
Thou shall not use a computer to harm other people.
Thou shall not use other people's computer resources without authorization
Thou shall use a computer in ways that show consideration and respect.
Thou shall not use a computer to steal.
Thou shall not use other people's computer resources without authorization
In this image, which feature did we most likely use to quickly change the background, fonts, and layout? Themes
Themes
SmartArt Graphics
AutoLayout
Transitions
Themes
An email supposedly from your bank asking for your password so that it can troubleshoot your account is a form of ________.
pharming
cyber-stalking
cyberbullying
phishing
phishing
Which of the following statements about P2P networks is false?
They can only support a small number of devices.
The services and security are centralized.
All computers are considered equal.
They can share a printer.
The services and security are centralized.
The SDLC, the traditional model for system development, is also called the ________ model.
spiral
whirlpool
Gantt
waterfall
waterfall
Lester sends an e-mail to the entire student body inviting them to a BYOB party at his house while his parents are out of town. Lester receives a message from a system administrator calling him in for a meeting with school officials. He objects because he feels that his e-mail is his own private business.
Thou shall not snoop around in other people's files
Thou shall not appropriate other people's intellectual output.
Thou shall think about the social consequences of the program you write.
Thou shall not interfere with other people's computer work.
Thou shall think about the social consequences of the program you write.
Suppose you're sharing a presentation with several coworkers, but you're not sure if they all have PowerPoint. What's the best way to ensure everyone will still be able to view your presentation?
Export as a PDF
Save as a Rich Text File
Print handouts and mail them
Describe each slide over the phone
Export as a PDF
Clickjacking results in ________.
sending spam to your friends' email accounts
malware posting unwanted links on your Facebook page
you sending money to get more money in return
your Facebook account being closed without your knowledge
malware posting unwanted links on your Facebook page
Which of the following statements about P2P networks is false?
They can only support a small number of devices.
The services and security are centralized.
All computers are considered equal.
They can share a printer.
The services and security are centralized.
In what phase of the SDLC does testing occur?
Implementation
Analysis
Maintenance
Design
Implementation
It seems like every time Melanie logs on to her account, Stanley knows about it and sends messages that cover her screen with text. At first, she thinks it is funny, but now it's really starting to bother her. The messages reformat the text on her screen and, besides, its kind of creepy the way he always knows she’s logged on.
Thou shall not interfere with other people's computer work.
Thou shall think about the social consequences of the program you write.
Thou shall not use or copy commercial software for which you have not paid.
Thou shall not use a computer to harm other people.
Thou shall not interfere with other people's computer work.
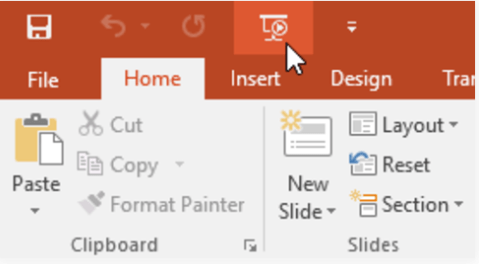 In this image, we are clicking a button on the Quick Access Toolbar. What will happen after we click it?
In this image, we are clicking a button on the Quick Access Toolbar. What will happen after we click it?
Export as a PDF
When a company pays people to hack into its own system, it calls in ________ hackers.
green hat
black hat
gray hat
white hat
white hat
A ________ network is one that has at least one computer that provides centralized management, resources, and security.
homegroup
peer-to-peer
workgroup
client-server
client-server
In what phase of the SDLC does user training take place?
Analysis
Planning
Maintenance
Implementation
Implementation
A secretary on the campus of a tax-supported university has been requested to give her staff a password to her supervisor. The supervisor would like to check the secretary’s e-mail when she is not at work to see if departmental-related mail is coming in. The secretary is not comfortable giving her password to her supervisor but is afraid to say no.
Thou shall not snoop around in other people's files
Thou shall not appropriate other people's intellectual output.
Thou shall not use a computer to bear false witness
Thou shall use a computer in ways that show consideration and respect.
Thou shall use a computer in ways that show consideration and respect.
Most slide layouts include at least one ________ by default.
transition
action button
placeholder
animation
placeholder
Hacking to make a political statement is called ________.
politicking
sneaking
cracking
hacktivism
hacktivism
To connect peripherals at short ranges, you would use the ________ wireless technology.
ultraviolet
Bluetooth
infrared
RFID
Bluetooth
The ________ is a set of five steps that a programmer follows to create a computer program.
Software Design Lifecycle
Program Development Cycle
Program Design Lifecycle
Computer Programming Cycle
Program Development Cycle
Marla figures out that when she is logged into the server, she can look at others' directories, make copies of files, and deposit new files. The operating system was designed to allow this functionality so that people could share their work. Mr. Klausinsky objects when he observes Marla poking around in another student's directory. But Marla responds by saying, "If the system allows me to do it and there's no specific rule against it, what's the problem?"
Thou shall not snoop around in other people's files.
Thou shall not use a computer to bear false witness.
Thou shall not interfere with other people's computer work
Thou shall not use a computer to harm other people.
Thou shall not snoop around in other people's files.
The New Slide command on the Ribbon lets you choose ________.
slide layouts
transitions
print settings
slide dimensions
slide layouts