This network security method takes it's name from a military concept and it's purpose is to allow an organization to expose it's internal applications/servers to the internet.
What is a DMZ (Demilitarized Zone)?
A proprietary application language used by Salesforce. The platform is intended to empower an organization to design applications specific to their needs.
What is APEX?
This device in the TFA I.T. infrastructure helps to manage traffic to servers and applications with parity and security.
What is a load balancer or F5?
A network of physical objects that communicate with each other as well as other systems - using the internet.
Hint:
What is IoT (Internet of Things)?
Which of the following TFA subscriptions is not considered Software as a Service (SaaS): Workday, Salesforce, Office 365, Service Now, Confluence?
What is Confluence?
All other applications are hosted and managed by a vendor. Although the application offers itself as SaaS, TFA has an on-premise solution.
A customer can configure their SaaS instances but cannot change any back-end components.
A naming system for computers and services that translates an IP address into a meaningful name. It is often referred to as the internet's phone book.
What is DNS (Domain Name System)?
This simulated attack of back-end I.T. systems has nothing to do with Bic or Papermate.
Most companies will undertake this process yearly, TFA's cycle is 18 months.
What is a PEN Test (Penetration Test)?
The test is performed to assess the vulnerabilities of target servers, applications and services.
Unity, VNX and Google Drive are examples of technologies that are used to...
What is store/save data?
VNX - Dell storage array, combination of regular disks and highly responsive disks.
Unity - Dell storage array, all flash disks.
Google Drive - cloud storage
Bitcoin was one of the first to adapt this secure peer to peer transaction ledger.
What is blockchain?
This is the name of the cloud service offered by Microsoft.
What is Azure?
What is the primary relational database technology used at TFA?
What is Microsoft SQL (Structured Query Language)?
Benefits
1. Very agile
2. Can be used in the cloud
3. Very Good Security Features
4. Performance (built-in compression and encryption features).
5. It costs less than Oracle...
What is the name of the TFA security application that restricts user privileges and limits an individuals ability to only install approved software?
What is Beyond Trust?
Beyond Trust implements a 'least privilege' policy which helps to prevent unauthorized access to I.T. systems. For example, standard users do not have local administrative access to their laptop.
A second feature called application control assists in preventing the installation of unverified software - such as malware.
Application Control Overview:

The act of creating an abstraction of computing resources?
Hint: This company logo is the leader in this technology.
What is Virtualization?
This metaphor describes what type of cyber-security attack?
200 people trying to simultaneously enter the front door of Walmart on Black Friday.
A variant of this type of attack is called:
What is DDoS (Distributed Denial of Service) attack?
During a DDoS attack you send millions of requests, per millisecond, that clog servers rendering them useless. There's no hacking involved, just an abnormal amount of traffic that the servers can't deal with, thus making prevention very difficult.
Which of the following cloud services is fictional?
1. IaaS
2. PaaS
3. CaaS
4. SECaaS
5. JaaS
What is JaaS?
1. IaaS - provides virtual infrastructure such as storage, network and servers
2. PaaS - expands on IaaS and provides operating systems, middleware and runtime environments.
3. CaaS - a relatively new technology used by developers, at a basic level a container is a virtual operating system (not tied to a virtual machine).
4. SECaaS - Security as a service is a group of tools such as anti-virus, anti-spam and intrusion detection that can be applied via the cloud to an organization.
A Microsoft service established in 2014 that allows and organization to replicate virtual servers into the blue cloud.
What is ASR (Azure Site Recovery)?
What is the name of the version control system used by TFA?
Hint: It integrates directly with Jira and Confluence?
What is BitBucket?
This picture represents what programming design concept.
What is API (Application Programming Interface)?
An API consists of an Interface, Protocol, Format and Endpoints.
Interface is a place where different software components interact. A Protocol is a set of rules defining how they interact, and a Format defines how they talk to each other. Endpoints provide different functionalities within the same interface.
The library of routines gives 3rd party programmers (i.e. TFA) access to proprietary (i.e. Microsoft Azure) building blocks to help create applications to talk between the two organizations. These are the 'hooks' and 'calls' in programming lingo.
Additional Details: https://youtu.be/81ygVYCupdo
PETYA and WannaCry are members of this malware family?
What is Ransomware?
- Locker ransomware encrypts the whole hard drive of the computer, essentially locking the user out of the entire system.
- Crypto ransomware will only encrypt specific, seemingly important files on the computer, such as word documents, PDFs and image files.
Gandcab ransomware struck TFA in September.

What type of cloud computing architecture is shown below?
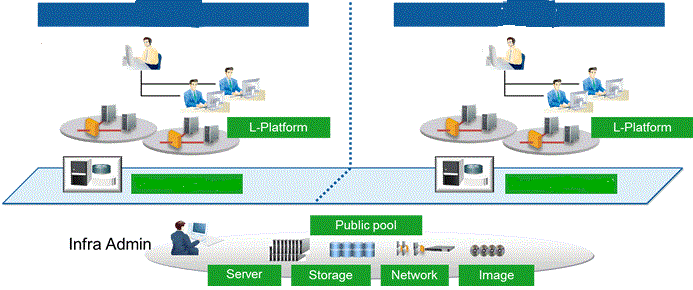
What is multi-tenancy?
1. Customers share computing resources.
2. It also allows the provider to only have to run a single server to support multiple customers (less cost and less complexity).
An appliance that provides a centralized location to save all of your organizations data.
What is a SAN (Storage Area Network)?
This object is stored as a single entity in a database management system and is typically used to hold files such as videos, audio and images.
Hint: It is also the name of this 1958 film starting Steve McQueen and remade in 1988.
What is BLOB (Binary Large OBject)?
Data is often stored as a binary with the database.
What is the name of company that provides TFA's COLO services?
What is SunGard?
Sungard is the TFA COLO (co-location or datacenter) located in Carlstadt NJ and is home to our physical computing/storage/backup/network infrastructure.
If our aspirational goal of Zephyr is realized, we will be able to remove almost all of our infrastructure hardware currently installed in SG.
The opposite of a “monolithic” application where all functionality is part of a single program running in a single environment.
What is a microservice?
eCommerce Shopping Cart Example
'Monolithic'
'MicroService'
Advantages
- It gives developers the freedom to independently develop and deploy services.
- Improves the scalability with the ability to individually scale services as needed.
- Better fault tolerance, which means that if one microservice fails, the others will continue to deliver.
- Code for different services can be written in different languages.
- The microservice architecture enables continuous delivery.
What are the 3 cloud delivery models?
What is Public, Private and Hybrid?
1. Public - available over the internet, often used by small business and where workers are geographically scattered. Examples include web mail and social networking.
2. Private - managed by the organizations IT department, expensive, high-performing. Large corporations and highly regulated industries are the typical consumers.
3. Hybrid - combines features of both public and private cloud. Some companies would archive data to a public cloud and run their critical applications within their private cloud.