Which of the following elements would be considered part of the user interface (UI) for an app? Choose all that apply.
A button that appears on the screen
An audible click that happens when the user taps the button
An error message that appears when something goes wrong
The color of the app's background screen
An OR gate is an electronic component with two inputs, A and B, such that *
the gate would be TRUE (or ON) when either or both A and B are TRUE (or ON)
What event causes the AndroidSprite to move to a new random location?*
Clock
Suppose you are sorting the following list of numbers in ascending order using bubble sort: [18, 5, -1, 4, 12, 19, 3, 10, 5, 4]. After the first pass through the numbers, what value would appear on the right of the list?
18
The Domain Name System *
creates IP addresses for clients and servers
Why are "if" blocks used in the "I Have a Dream" app?
"if" blocks are used to determine, when the buttons are clicked, whether a speech is already playing.
____________________ is a data compression technique in which no data are lost.
Lossless
What value would give the MoleTimer's TimeInterval property to have the Mole jump every 2 seconds.
2000
Suppose you are sorting the following list of words into alphabetical order using bubble sort: [parameter, procedure, abstraction, variable, integer, modulus, syntax, heuristics]. After the first pass through the list, what word would appear on the right of the list?
Variable
Caesar cipher, simple substitution cipher, and Vigenere cipher are all examples of __________ ciphers.
Symmetric
Which of the following are examples hardware?
CPU Main memory Integrated circuit Flash drive
________________is a data compression technique in which some amount of data is lost.
Lossy
Evaluate (3+8) mod 7
4
128.87.212.42 is an example of a/an
IP Address
A one-way function
s a function that is easy to compute in one direction but hard to compute in the other.
Which of the following are true statements about a computer's main memory?
It stores data.
It is called RAM, short for random access memory.
Any data stored in main memory disappears when the computer loses power.
Using a variable is an example of abstraction because *
a variable is more general and more abstract than a specific value such as 5.
using a variable instead of a specific value makes an app more generally useful.
a variable is an abstract symbol that can represent lots of different values.
using a variable instead of a specific value makes an app more vague. 24.
using a variable instead of a specific value makes an app more generally useful.
a variable is an abstract symbol that can represent lots of different values.
Which of the following statements describes a limitation of using a computer simulation to model a real-world object or system?
A. It is difficult to change input parameters or conditions when using computer simulations.
B. Computer simulations only run on very powerful computers that are not available to the general public.
C. Computer simulations can only be built after the real-world object or system has been created.
D. Computer simulations usually make some simplifying assumptions about the real-world object or system being modeled.
D. Computer simulations usually make some simplifying assumptions about the real-world object or system being modeled.
Bandwidth measures ___________________.
the amount of data that can be sent in a fixed amount of time
The key exchange problem is
the problem swapping Alice's key for Bob's key.
How long is a millisecond?
1/1000 of a second
Before you use a global variable in App Inventor 2, it must be: *
initialized
What shape would be drawn by IMAGE 1's algorithm? * 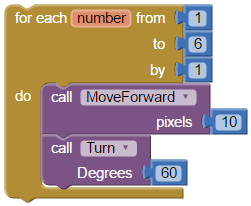
hexagon with sides a length of 10 pixels
Latency measures ___________________.
the amount of time it takes to send data over the Internet
A polyalphabetic cipher *
Uses multiple alphabets