This guiding principle should be used when defining permissions within a network where sensitive information may be transmitted near users who are not supposed to be authorized to see it
What is Principle of Least Privilege?
This address range is defined for Class B within RFC1918
What is 172.16.0.0-172.31.255.255?
RFC1918 Defines private network addresses
The broadcast address of 192.168.2.2/16
What is 192.168.255.255?
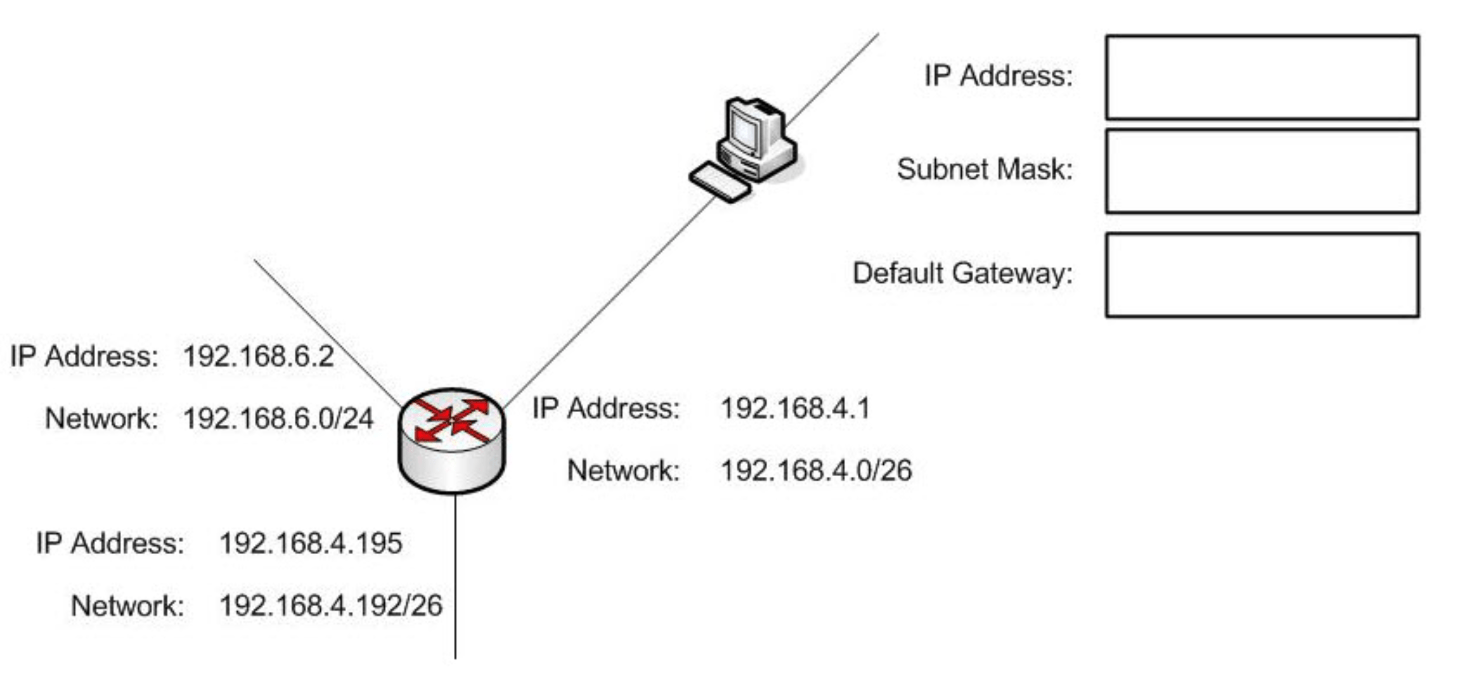
Give me valid entries for all three blanks in this network
What is 192.168.4.1, 255.255.255.192, anything from 192.168.4.2-192.168.4.62
This is indicated by the cable tester output below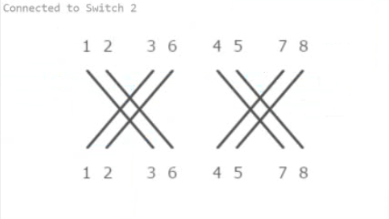
What is using a crossover cable?
Danny designed his network with security at every device and with multiple layers of security, not just for the edges of his network, because he learned about this concept during yesterday's lecture?
What is Defense in Depth?
The class of network for the IP address 172.19.64.128/17
What is Class B?
This CIDR would cover the addresses 192.168.1.65, 192.168.1.91, and 192.168.1.125 in the smallest network segment possible that contains all three.
What is /26?
The NID would be 192.168.1.64 and the broadcast is 192.168.1.127 with the following NID being at 192.168.1.128
This is the issue with pinging a broadcast address like 192.168.68.255
It is highly unreliable to try to ping broadcast.
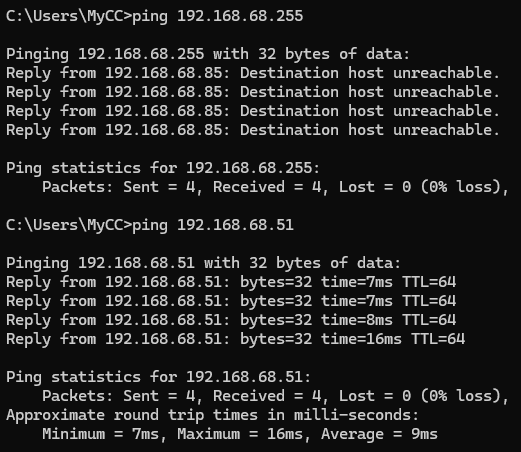
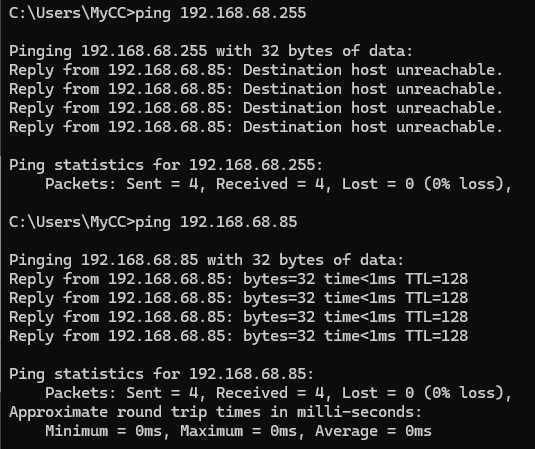
This protocol provides methods to combine multiple physical network connections into one logical network connection
What is LACP Link Aggregation Control Protocol?
You would use this to control access to your network by querying devices for their security status, asking about antivirus being installed, security patches applied, making sure the device meets any other requirements of the network, and that the user is authorized for the requested resource BEFORE connecting the user.
What is NAC Network Access Control?
RFC 1918 defines this as the full class C private range
What is 192.168.0.0-192.168.255.255?
You are selecting IP addresses for your network and have 4 to choose from that must meet the following specification from management: Class B private address type, minimum 63 usable IP addresses.
You have some proposed IPs from your junior network engineer and told them to use this as it meets the requirements from management;
192.168.0.0/26
10.0.64.0/28
10.0.64.0/26
172.23.64.0/26
What is 172.23.64.0/26?
This kind of antenna should be used for AP2 to minimize the ability for unauthorized users to see the wifi network from outside the office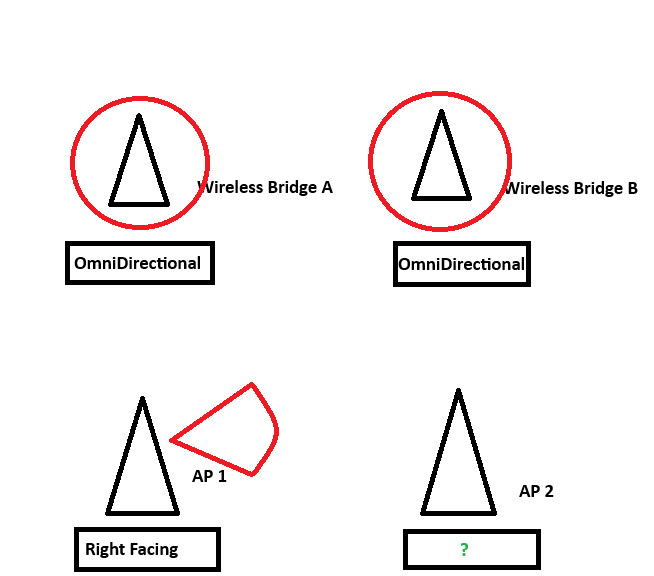
What is a directional antenna facing left?
This is the designation of the port meant to carry multiple VLANs for your network over a single link
What is a trunk port?
This technology is used to detect intrusion and other security events by gathering logs in a central location and correlating events from the totality of the signals on your network and only alerts an administrator or an application that CAN take action of it's findings, does not take action itself.
What is a SIEM Security Information and Event Management?
You attempt to ping 172.16.32.213 from 192.168.1.54 knowing that they are separate networks and get no response because of this
What is private network addresses are dropped by routers?
This is the sequence of NID w/CIDRs needed to fulfill the requirement of not wasting more IPs than needed to make 4 networks consisting of 56 hosts, 100 hosts, 600 hosts, and 40 hosts, starting from 172.24.0.0
What is 172.24.0.0/22, 172.24.4.0/25,172.24.4.128/26, 172.24.4.192/26?
You have received equipment from corporate to setup a new multi-building wifi for your location and need to properly order the equipment for best access;
Wireless Range Extender
Router
Switch
Firewall
Wireless Access Point
Hub
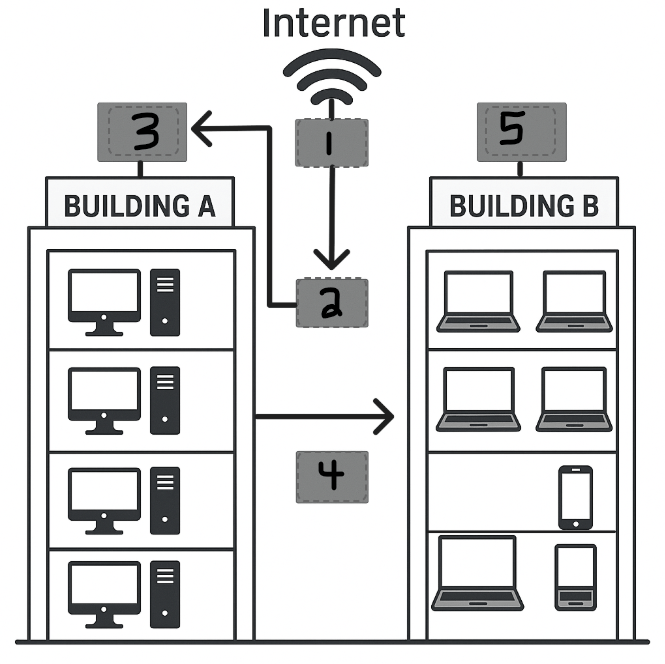
What is Firewall, Router, Switch, Wireless Range Extender, Wireless Access Point, throw the hub in the garbage?
This technology is being shown overall by the diagram below
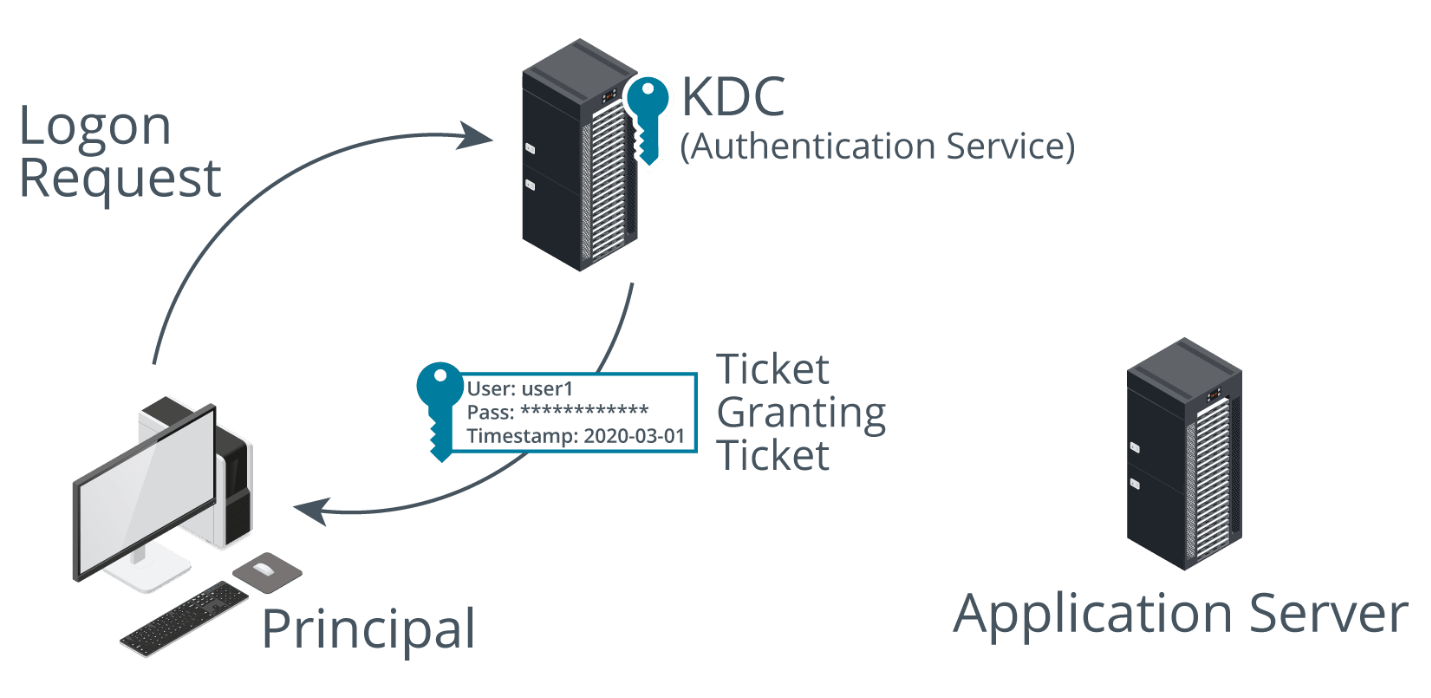
What is Kerberos? Named after Cerberus.

Explain the purpose of MAC filtering
MAC filtering is a network security technique that restricts access to a network by allowing or denying devices based on their unique MAC (Media Access Control) addresses. It helps administrators control which devices can connect, adding an extra layer of protection beyond passwords by creating a whitelist or blacklist of approved hardware. While useful for managing access and reducing unauthorized connections, MAC filtering has limitations—such as vulnerability to MAC spoofing and the administrative burden of maintaining device lists—making it most effective when used alongside other security measures.
Explain how an ACL is used by a firewall
Top down priority, a connection will follow the first rule that applies to it even if another afterwards changes that rule's intent, implicit deny will stop anything not explicitly allowed, like the list a bouncer has at the door
Explain how we use a proxy server for network security
Content filtering, URL filtering, bandwidth usage, keyword filtering, destination site reputation, use in combination with a firewall to add connection based security.
Explain AAA
Authentication (verifying identification) Authorization (what you're allowed to do) and Accounting (tracking what you have actually done)
Explain SSO vs Federation
SSO Single Sign On, access multiple network resources or applications with a single authentication, think signing into GMail and being able to access Docs and Drive and Photos by just clicking a link once you're signed in.
Federation; another authentication authority is vouching for your identity on a network they do not control, think "Sign on with Google" or "Sign in with your AppleID" buttons on websites that aren't Google or Apple