Which command would be best to use on an unused switch port if a company adheres to the best practices as recommended by Cisco?
Shutdown
Port security limits the number of valid ________ allowed on a port.
MAC addresses
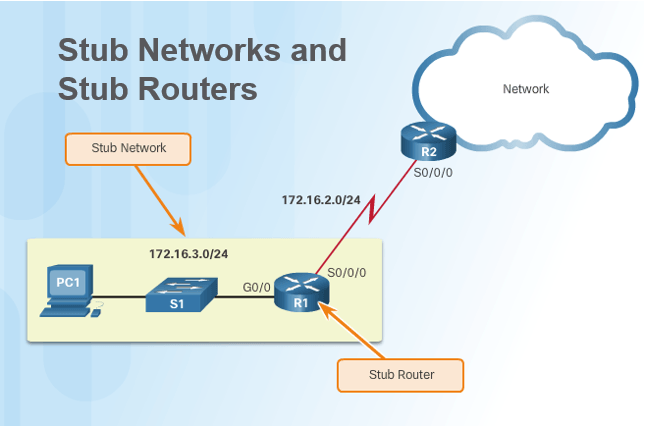
What is a Stub Network comprised of?
One router, one switch, and end device
What is the configuration to have the port/interface automatically learn the source MAC address?
switchport port-security mac-address sticky
What is the default static route?
ip route 0.0.0.0 0.0.0.0
The wildcard mask is typically the ________ of the subnet mask configured on that interface.
inverse or opposite
What is a series of IOS commands that is used to filter packets based on information found in a packet header?
Access Control List (ACL)
In reference for switchport, how many modes are there and what are they?
There are two; switchport mode trunk and switchport mode access
Which security feature should be enable in order to prevent an attacker from overflowing the MAC address table of a switch?
1. BPDU filter
2. Port Security
3. Root Guard
4. Storm Control
2. Port Security
What is the use for NAT?
- Use of NAT is to conserve public IPv4 addresses
- NAT allows networks to use private IPv4 addresses internally and translates them to a public address when needed
- A NAT router typically operates at the border of a stub network
- When a device inside the stub network wants to communicate with a device outside of its network, the packet is forwarded to the border router which performs the NAT process, translating the internal private address of the device to a public, outside, routable address
A routing table contains a list of routes to known networks (prefixes and prefix length). The source of this information is derived from what?
1. Directly connected networks
2. Static routes
3. Dynamic routing protocols
What command is used to set a certain amount of MAC addresses for an interface?
switchport port-security maximum value
What interface do you set your clockrate?
Whatever interface that the topology identifies as the DCE
YES or NO
Does it matter the order that an ACL is placed in?
Yes
Placement of your deny or permit statement makes a big difference on how it is set up
There are two basic tasks when configuring static NAT translation, what are they?
1. Create a mapping between the inside local address and the inside global addresses using the ip nat insdie source static command
2. The interfaces participating in the translation are configured as inside or outside relative to NAT with the ip nat inside and ip nat outside commands.
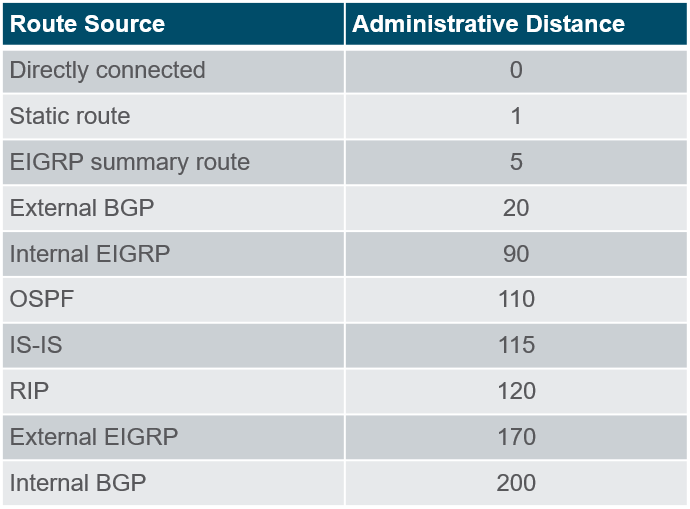
Cisco IOS uses what is known as the _____________ to determine the route to install into the IP routing table. This represents the "trustworthiness" of the route. The lower this is, the more trustworthy the route source.
administrative distance (AD)
OSPF messages are forwarded out all OSPF-enabled interfaces. However these messages only need to be sent out interfaces that are connecting to other OSPF-enabled routers. Sending out unneeded messages on a LAN affects the network in three ways. What are those ways?
1. Inefficient use of bandwidth - Available bandwidth is consumed transporting unnecessary messages.
2. Inefficient use of resources - All devices on the LAN must process and eventually discard the message.
3. Increased security risk - Without additional OSPF security configurations, OSPF messages can be intercepted with packet sniffing software.
What are the port security violation modes?
1. Shutdown
2. Restrict
3. Protect
In reference to OSPF, what are the two things that needs to be the same on all OSPF routers?
1. Process ID
2. Area ID
How do you propagate the default route?
default-information originate
If you wanted to put the same command on multiple consecutive interfaces, what command would you use?
interface range
The source for each route in the routing table is identified by a code. Those common codes are what?
L - identifies the address assigned to a router interface
C - identifies a directly connected network
S - identifies a static route created to reach a specific network
O - identifies a dynamically learned network from another router using the OSPF routing protocol
* - this route is a candidate for a default route
Are router to router interfaces passived?
No
If it is router to router, that interface is not passive
When the client boots (or otherwise wants to join a network), it begins a four-step process to obtain a lease. What is that process?
DORA
1. Discover
2. Offer
3. Request
4. Acknowledgment
What cisco command is configured so that the router acts as a relay agent forwarding the message to the DHCPv4 server?
ip helper-address
NAT has four types of addresses, what are they?
1. Inside local address
2. Inside global address
3. Outside local address
4. Outside global address
Configuring a DHCPv4 server pool name will allow the administrator to know which DHCP pool certain ____ belong to.
IP's
What is the cisco discover protocol that allows for the device to see its neighbor?
show cdp neighbors
cdp stands for ciscor discovery protocol
The last statement of an ACL is always an ________.
implicit deny
If a duplicate MAC address error is presented or a port is in an error-disabled state, what is the fix action?
(give all steps in order to get points)
1. Enter the interface that has the duplicate MAC address or have error-disabled
2. Close the interface (shut)
3. Remove/Delete all the commands that has switchport port-security in the interface (i.e. max/violation/aging/mac-address)
4. Save configuration (copy run start)
5. Reload the device
6. Enter in the interface again
7. Place all the switchport port-security back on the interface
8. Open the interface (no shut)
What command displays the translations from two different hosts to different web servers?
show ip nat translations
There are five tasks when configuring dynamic NAT translations, what are they?
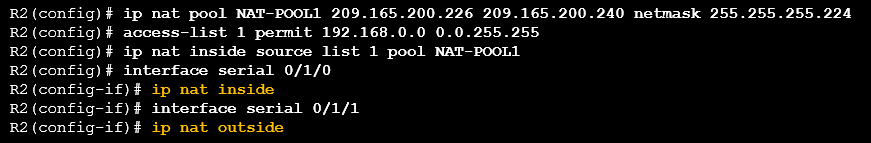
1. Define the pool of addresses that will be used for translation using the ip nat pool command
2. Configrue a standard ACL to identify (permit) only those addresses that are to be translated
3. Bind the ACL to the pool, using the ip nate inside source list command
4. Identify which interfaces are inside
5. Identify which interfaces are outside
Administrative Distance protocols
By default, the ip helper-address command forwards eight UDP services. What are the ports and name of those UDP services?
Port 37 = Time
Port 49 = TACACS
Port 53 = DNS
Port 67 = DHCP/BOOTP server
Port 68 = DHCP/BOOTP client
Port 69 = TFTP
Port 137 = NetBIOS name service
Port 138 = NetBIOS datagram service
What are the 7 steps of troubleshooting?
1. Identify the Problem
2. Develop a Theory
3. Test the Theory
4. Create a Plan of Action
5. Implement the Solution
6. Verify System Functionality
7. Document the Issue