A device that uses electrical signals and has an input, process, storage and output.
What is a digital device?
Internally and externally.
What two ways is data transmitted?
File storage provided on third-party servers over the Internet.
What is Cloud storage.
Using obvious passwords such as your favourite pet, place or date of birth
Disclosing passwords with other users
Leaving devices open to other users, such as not locking a device when going for a break
Using the same login details for multiple website accounts
Posting information globally without thinking first as to whether it is sensible to do so
Using personal devices for business operations.
Ways in which data is put at risk.
Input devices
Output devices
Storage devices
Communication devices
Peripherals can be categorised as:
One uses copper or fibre optic cables and the other uses radio waves as the connection medium.
What's the difference between wired and wireless.
VPNs instead of remote desktop.
Which technology should businesses choose for remote working?
A weakness that can be exploited by a cyber criminal allowing them unauthorised access to a computer system. For example, a misconfigured firewall.
What is a vulnerability?
A system that sits between the computer's firmware (BIOS/UEFI) and applications. The vital link between software and hardware.
What is an operating system?

Crosstalk and interface bottlenecks.
What is the issue with parallel communication?
E.g. Twitter (X).
What is an example of a microblog website?

E.g. posting information globally without thinking first as to whether it is sensible to do so. Also, phishing.
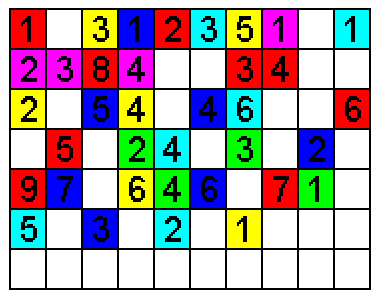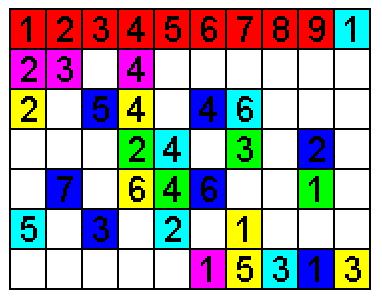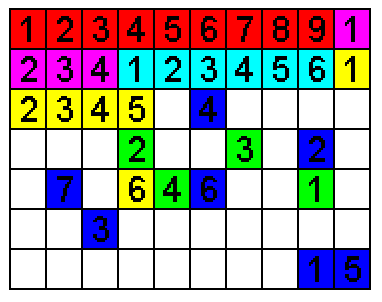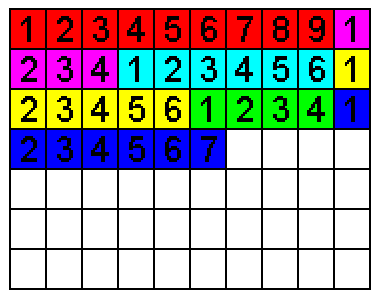
A visual representation of defragmentation.
Run network cables up and down lift shafts.
What is one thing you shouldn't do, to avoid the effects of EMI on networking cabling in large multistory buildings.
Companies publicly list what they want testing and the reward for any disclosed vulnerabilities.
What are bug bounties?
Specifications
?
?
Compatibility
?
Cost
Implementation
Security
Efficiency
?
Which ones are missing?
User experience
User needs
Connectivity
Productivity
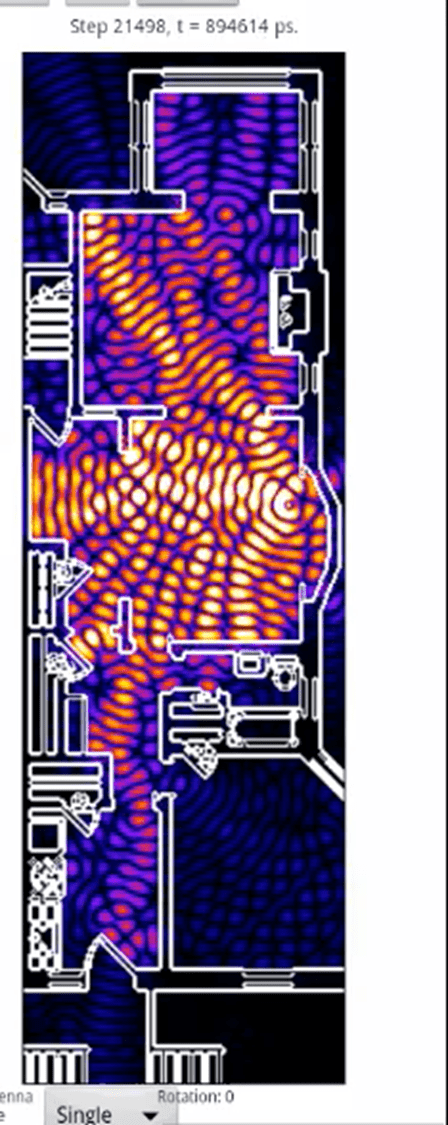
Two walls and the bathroom plumbing are blocking the signal.
Why does the room at the bottom-right have lower signal strength?
Online discussions organised into threads. They are not designed for real-time communication between users. They can cover a wide user base which makes them useful for things such as tech support
Describe forums as an online community.
An attack where malicious content from one website is embedded into another. The content may even be used to cover up things like login forms, so that user credentials can be intercepted.
iframe injection attack.